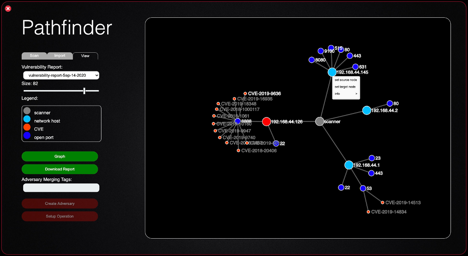
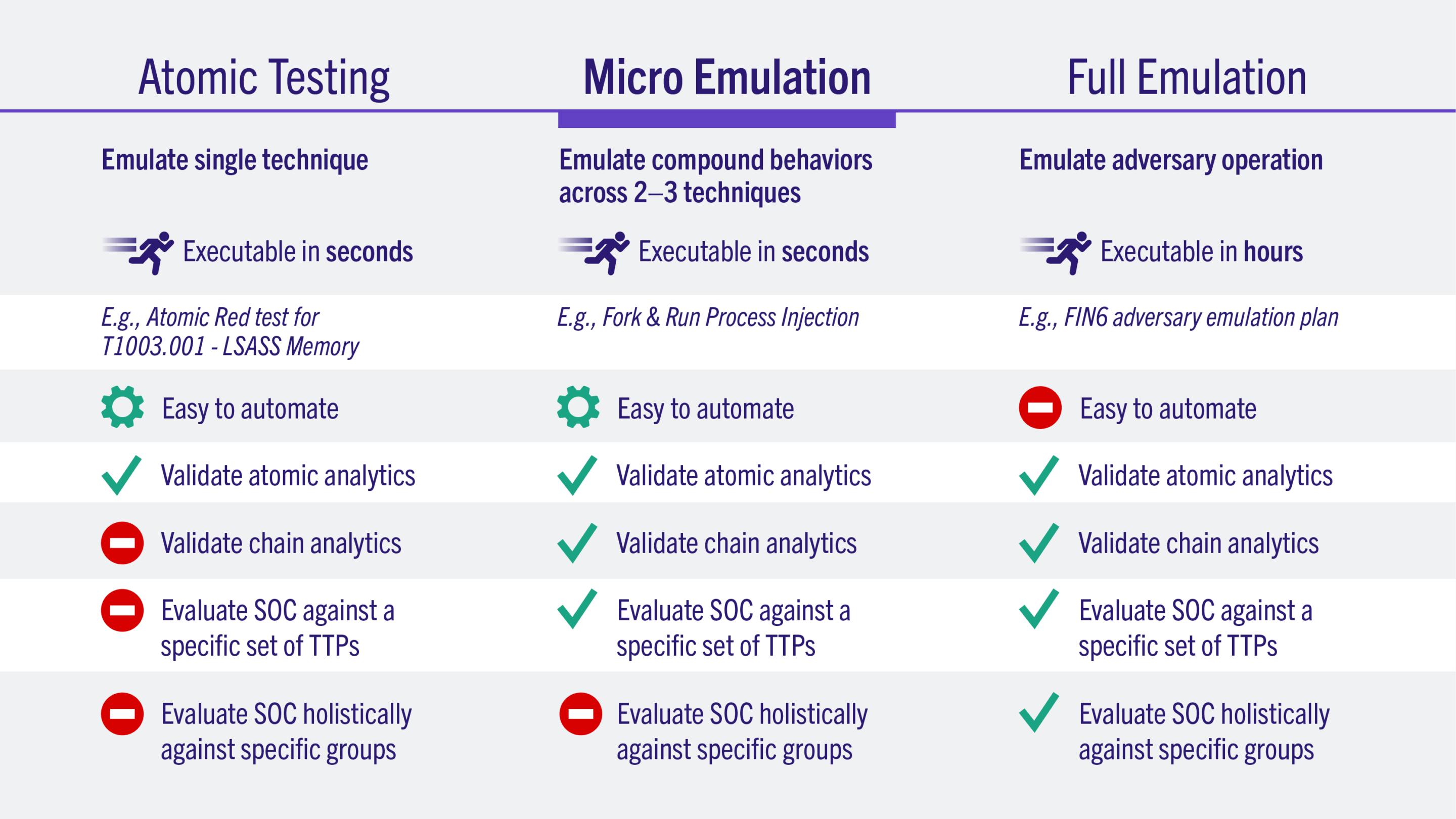
OceanLotus Adversary Emulation Plan
OceanLotus (aka APT32, SeaLotus, APT-C-00) is a suspected Vietnam-based threat group that has been active since at least 2014. The group has targeted multiple private sector industries as well as foreign governments, dissidents, and journalists. This project adds the first macOS and Linux focused …