Threat-Informed Defense for Cloud Security
Use our latest mappings to replace assumption-driven cloud defense with evidence-based decisions to stop cloud adversaries in their tracks. With …
September 15, 2022
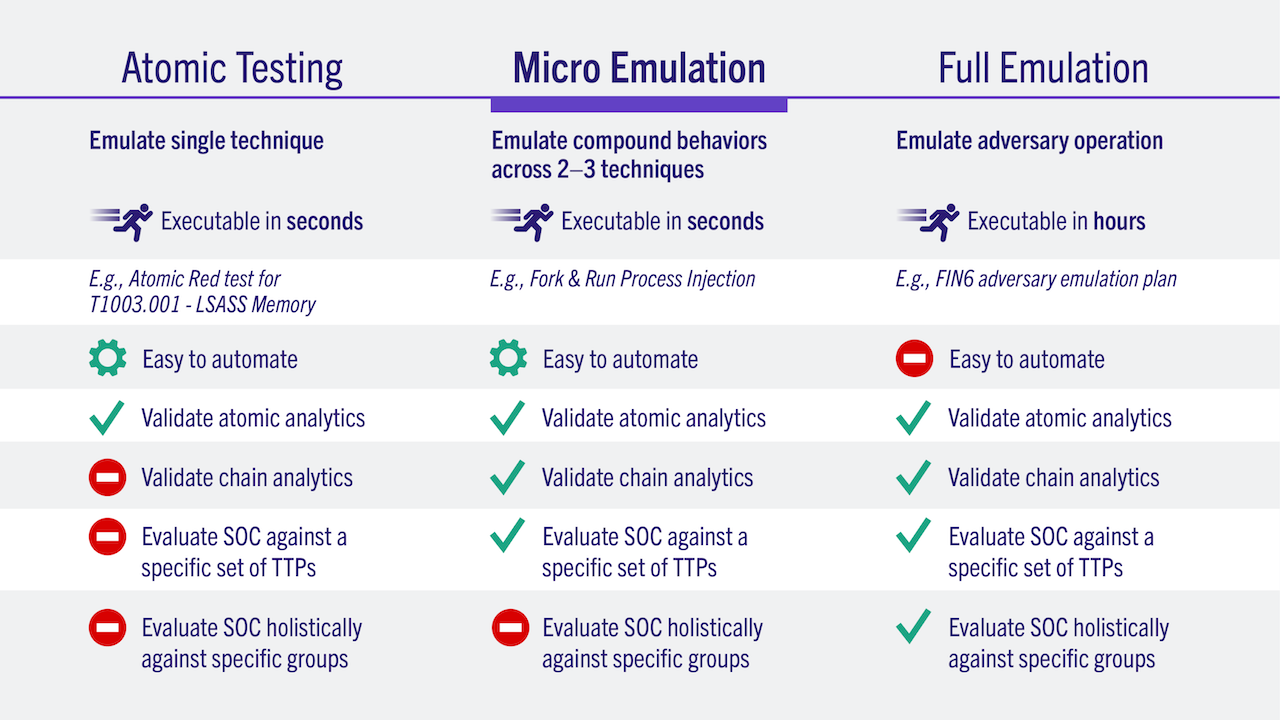
Micro Emulation Plans help organizations validate their defenses quickly and easily by building smaller scale adversary emulation plans that are fully automated using compatible tools and focused on common threats. The Micro Emulation Plans help scale the impact of the Adversary Emulation Library beyond those with sophisticated red teams to allow even those without a red team to run scenarios in compatible breach and attack simulation or automated adversary emulation tools, make improvements, and validate improvements.

Long and complicated emulation plans can be complex and costly for organizations to implement and rapidly iterate on results.

Create light-weight emulation plans that focus on key attack techniques for important threats.

Red teams and others can quickly perform emulations for relevant threats that lead to positive changes in defensive posture.










Use our latest mappings to replace assumption-driven cloud defense with evidence-based decisions to stop cloud adversaries in their tracks. With …
MITRE INFORM is a program-level assessment designed to show how threat-informed your organization is and where to improve next across cyber …
With Attack Flow, you will capture the entire attack and communicate what matters!
Sign up for our "Stay Informed" mailing list to receive announcements for project publications, upcoming events, and other news about the Center.