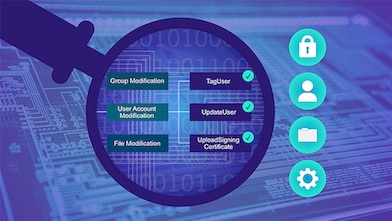
Ambiguous Techniques: Determine Malice through Context
An ambiguous technique is a MITRE ATT&CK® technique whose observable characteristics are insufficient to determine intent. This means that the observable data does not allow us to confidently ascertain whether the intent…