Threat-Informed Defense for Cloud Security
Use our latest mappings to replace assumption-driven cloud defense with evidence-based decisions to stop cloud adversaries in their tracks. With …
July 28, 2022
The Cloud Analytics project sought to advance the state of the practice by developing a blueprint for writing analytics for cloud platforms. To create the blueprint, the team “learned by doing” – exercising adversary behaviors, developing analytics, and refining them. Lessons learned were gathered along the way and incorporated into the analytics blueprint shared with the community.

Defenders achieve sufficient visibility of adversary behaviors in on-premises environments, but they struggle to achieve comparable visibility in cloud environments.

Developed a foundational set of cloud analytics for key TTPs and captured best practices and lessons learned in an analytics blueprint document.

Improves defenders’ ability to develop analytics to detect adversary behaviors in cloud environments.
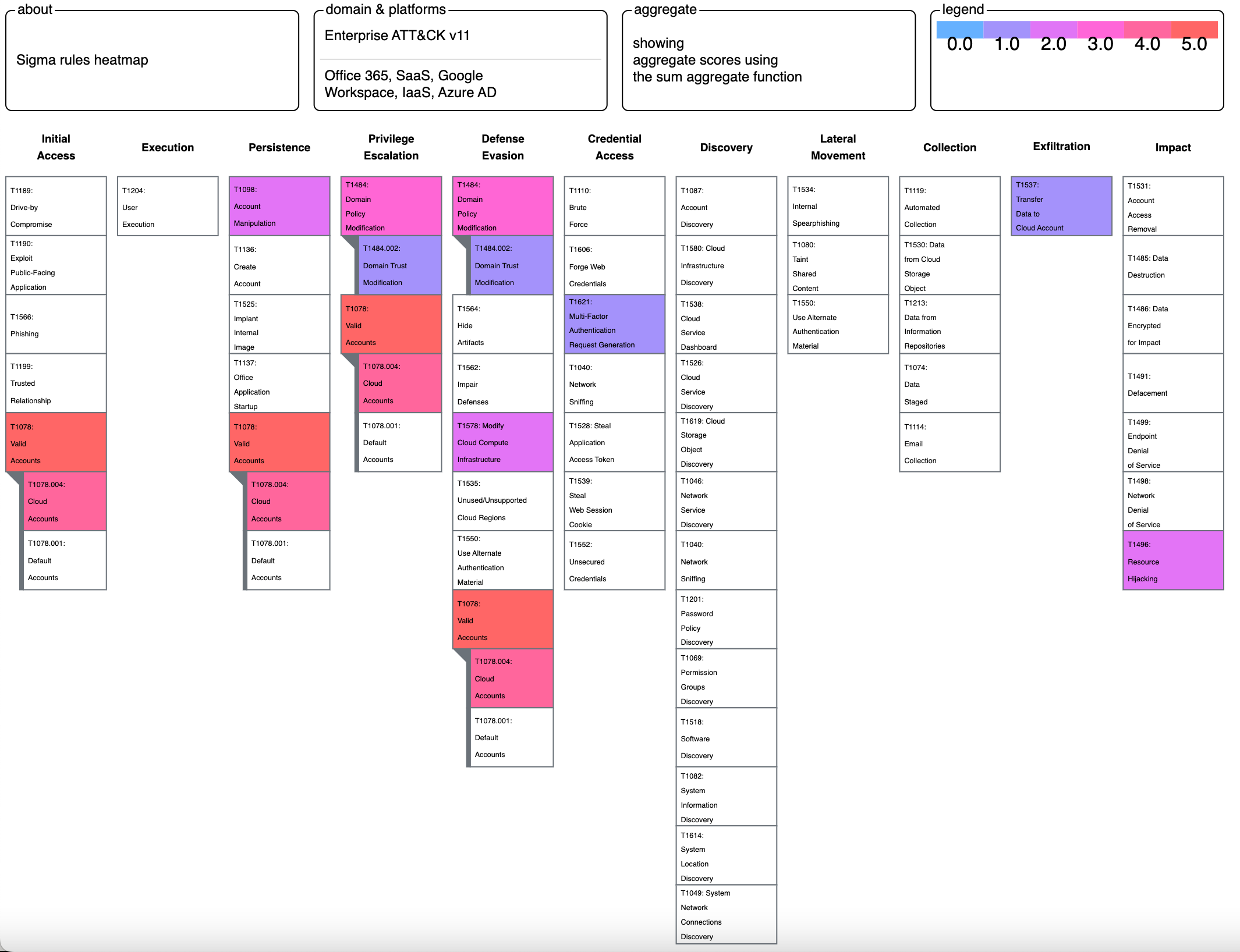










Use our latest mappings to replace assumption-driven cloud defense with evidence-based decisions to stop cloud adversaries in their tracks. With …
MITRE INFORM is a program-level assessment designed to show how threat-informed your organization is and where to improve next across cyber …
With Attack Flow, you will capture the entire attack and communicate what matters!
Sign up for our "Stay Informed" mailing list to receive announcements for project publications, upcoming events, and other news about the Center.