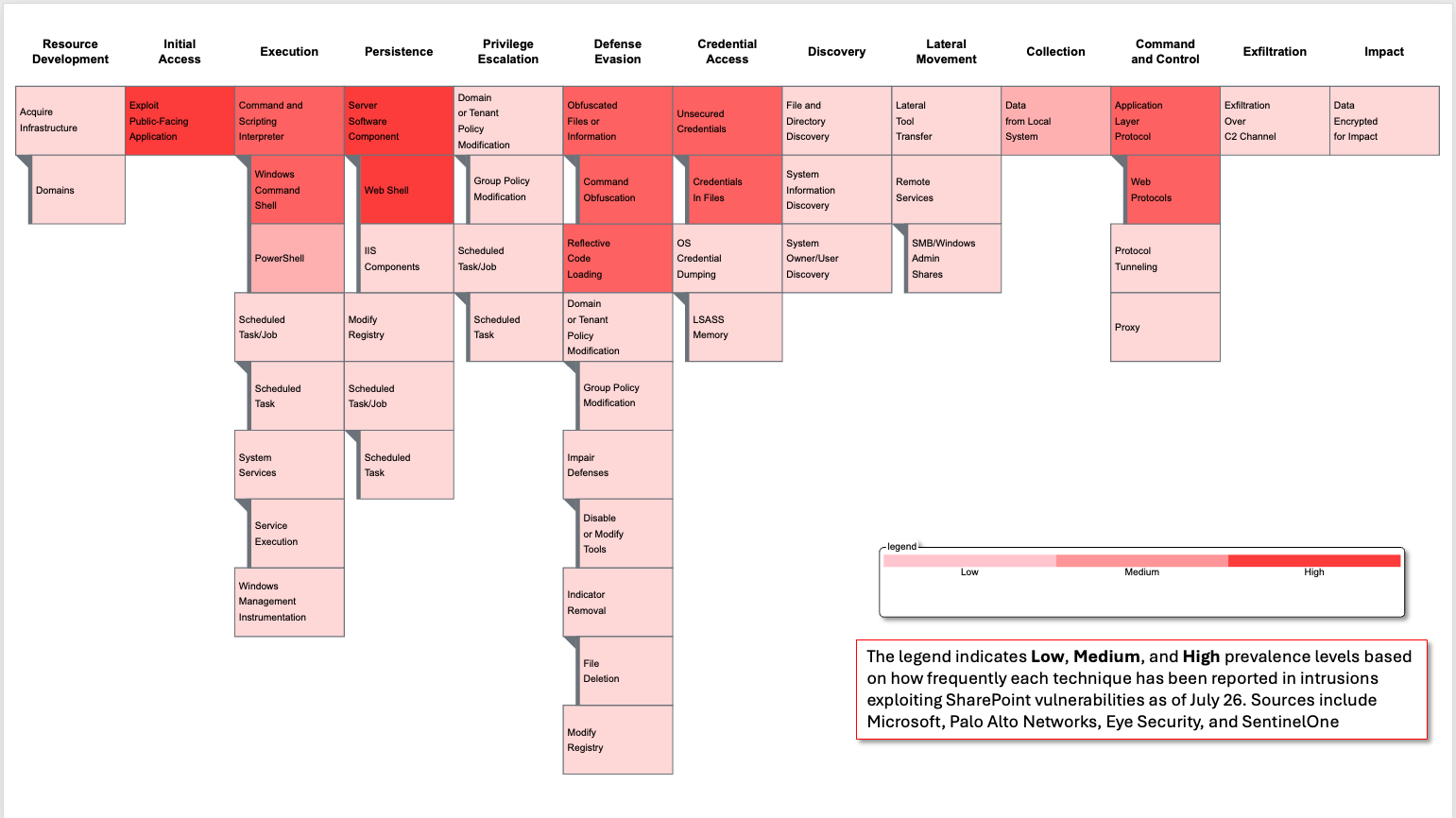
Can You Detect What You Can’t Predict? Lessons from SharePoint Vulnerability CVE-2025-53770
The exploitation of critical zero-day vulnerabilities in Microsoft SharePoint highlights that adversaries don’t always need new tools to succeed. By chaining familiar techniques with newly discovered flaws, they can bypass defenses without deploying novel malware or infrastructure. Sometimes, all it …