A Threat-Informed Community is Necessary for Defense to Function
Threat-informed defense changes the game on the adversary. Threat-informed defenders read their adversaries’ playbooks and then orchestrate a …
By Suneel Sundar • February 12, 2026

Threat-informed defense changes the game on the adversary. Threat-informed defenders read their adversaries’ playbooks and then orchestrate a defense based on that knowledge. MITRE ATT&CK® is the core of threat-informed defense as our framework of adversary tactics, techniques, and procedures (TTPs). From this foundation, we build detection rules that find and security controls that mitigate adversary actions. From this inspiration, we defend AI-enabled systems and document the playbooks of insider threats and fraud actors. In 2026, the MITRE Center for Threat-Informed Defense (CTID) continues to bring tradecraft out of the shadows and deliver tailored practical, research-driven defenses for the global cybersecurity community.
A threat-informed community is essential for effective cyber defense. In 2026, the MITRE Center for Threat-Informed Defense (CTID) will focus its R&D program on a clear set of outcomes that help defenders operationalize adversary behavior at scale. Our 2026 roadmap centers on six lines of effort:
This roadmap is designed to guide defenders toward capabilities to adopt, integrate, and scale—so organizations can start quickly, then continuously get better at threat-informed defense.

David Bianco’s Pyramid of Pain introduced the defenders to the idea that by identifying and detecting adversary tactics, techniques, and procedures (TTPs), it would be harder for adversaries to evade detection. The higher up the Pyramid a defender can detect, the greater the cost imposed on the adversary. Many detection analytics are vulnerable to low-cost adversary evasion. CTID’s Summiting the Pyramid (STP) methodology defines and quantifies detection robustness—how difficult it is for adversaries to evade a detection.
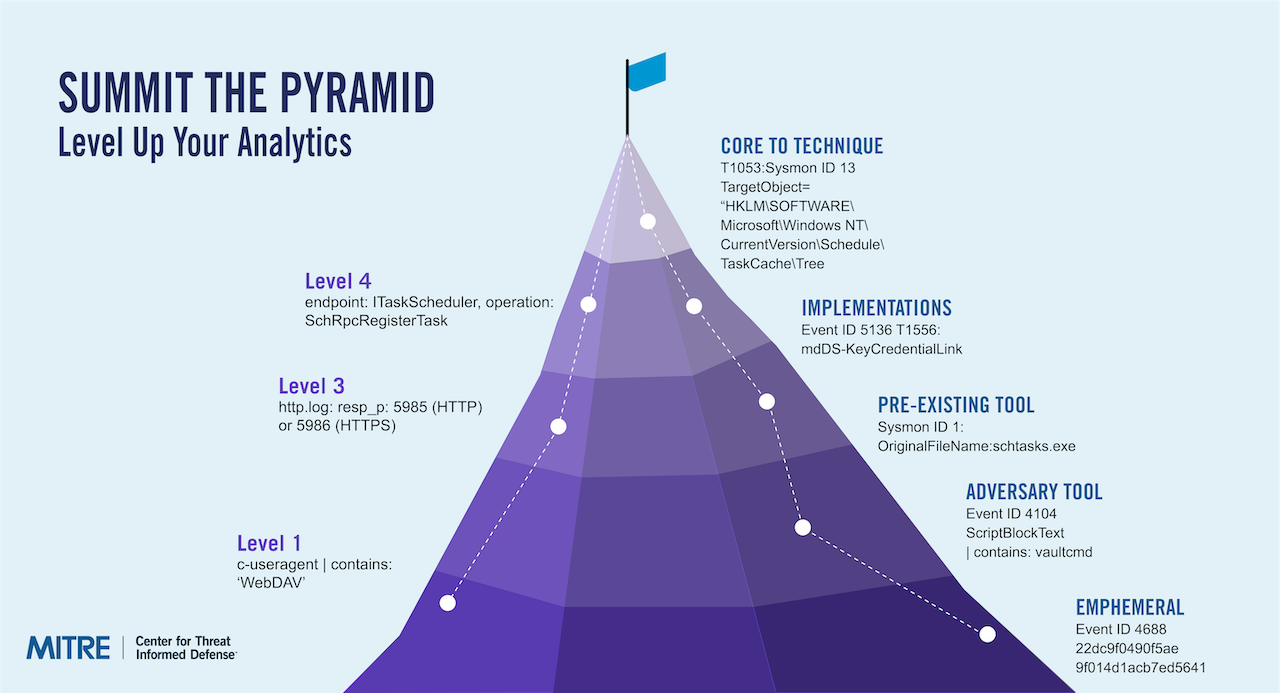
Building on this work, CTID advanced detection engineering through its Ambiguous Techniques research. Because many ATT&CK techniques are living-off-the-land and not inherently malicious, this work focused on determining the telemetry required to distinguish benign from malicious behavior. We grouped ambiguous techniques into adversary use cases, analyzed the log sources required to detect those use cases, and moved detection analysis beyond individual techniques to the telemetry needed to observe real adversary behavior.
Ambiguous Techniques exposes a critical reality: modern adversaries deliberately operate in the gray space between benign behavior and malicious action.
Douglas Jose Pereira dos Santos: Director, Advanced Threat Intelligence, Fortinet
We then introduced a confidence score to identify which log sources consistently produce high fidelity detections. By evaluating confidence across use cases we identified the log sources that consistently produce high-fidelity detection, which justifies data collection and detection investment. We further scaled this using LLM-driven Retrieval-Augmented Generation to automate confidence scoring across telemetry sources.
In 2026 CTID’s research will answer questions in detection that are operationally relevant now to threat-informed defenders:
MITRE CTID’s Insider Threat research began with acknowledgement that insider threat practitioners did not have a common language to share non-attributable observation of insider techniques. So we published the first evidence-based, cross-sector, community-sourced, and openly accessible knowledge base of the TTPs used by insiders in the enterprise environment: the Insider Threat TTP Knowledge Base. MITRE CTID then expanded the techniques of the Insider Threat KB, prescribed detection tools and preventative measures for insider techniques, and defined Observable Human Indicators (OHIs): qualitative and objective attributes of insider threat actors that add context to the TTPs.

Consider now these dozens of sequences of seemingly benign techniques that were used maliciously by insider threat actors. In 2026 our Insider Threat research will apply CTID’s Ambiguous Techniques methodology to the InT KB data set and derive context and observational principles to distinguish when possibly benign techniques (such as zipping files or utilizing ipconfig) are used by insider threat actors for malicious ends.
Finally, we will demonstrate how an insider threat program can avail itself of CTID research and results. We will define pre-requisites for insider threat programs to use the InT KB, OHIs, and the Ambiguous Techniques methodology. For organizations that are building an insider threat program, we will document technology, policy, and governance best practices. These recommendations will demonstrate the necessary conditions to implement the detection and mitigation results derived in the Insider Threat TTP Knowledge Base.
Security capability mappings connect the defenses you’ve invested in to the specific threats that keep you up at night. In January 2026, we mapped adversary behaviors to the Cloud Security Alliance Cloud Controls Matrix (CCM), a set of cloud security controls that address technical and operational aspects of cloud computing across shared responsibility models. The mappings demonstrate how these industry-recognized cloud controls can mitigate specific adversary behaviors. The mappings establish a shared foundation across teams so that organizations will apply threat-informed defense consistently across cloud environments.
ATT&CK updates to a new major version twice a year, and security vendors constantly change their offerings. Continuing in 2026, CTID’s Mappings Program will deliver new collections for threat-informed defensive measures and update the existing mappings collection to reflect techniques in ATT&CK v18. These and our continual updates are available on the Mappings Explorer platform. This year, we will scale the Mappings Program by using an AI-enabled process to align security capability mappings with the latest versions of ATT&CK.
Some mappings relate adversary behaviors documented in ATT&CK to security controls or compliance frameworks. For example, the NIST 800-53 mappings enable cybersecurity architects to cross walk between adversary behaviors and defensive posture. CTID will grow the corpus of mappings in 2026 by:
In 2024, MITRE CTID undertook the effort to Measure, Maximize, and Mature Threat-Informed Defense (M3TID) by advising organizations on incremental efforts to implement and improve their threat-informed defense. Our 2026 research publication INFORM retains that core intent and sharpens it to address how organizations operate today.

INFORM builds upon the M3TID model and evaluates threat-informed defense as holistic practice rather than a series of initiatives. Key advances include:
INFORM provides a program-level view and complements models that focus on specific teams and functions. For example, capability maturity models such as CTI-CMM, SOC-CMM, and Red Team-CMM, typically operate at the tactical level, driving depth within a function. INFORM tells leaders whether the overall program consistently applies threat-informed defense and where coordinated investment will improve outcomes.
The problem of financial fraud is prime for the application of threat-informed defense. When we address financial fraud at the time of the material event, we react. It would be like placing our controls for intellectual property theft exclusively in the exfiltration stage.
Our Fight Financial Fraud (F3) framework enables fraud defenders by codifying the tactics and techniques used in fraud events. Fraud actors use some ATT&CK techniques with traditional fraud techniques, making cyber-fraud fusion framework necessary. After initial publication in March 2026, we will add additional fraudster techniques, data sources that detect the techniques, and mitigations to reduce harm from fraud.
With our members we seek to expand the Fight Fraud research area to additional sectors like retail fraud, health benefits, and aviation. The foundation remains to unite the events detected through cyber means with the material fraud event via data fusion and analysis.
Top ATT&CK Techniques provided defenders with a structured, transparent approach to prioritize ATT&CK techniques. That work established a practical starting point for defensive effort and enabled organizations to align resources against the techniques most relevant to themselves. Since then, adversary behavior has expanded and defensive practice has evolved. Notably in 2025, ATT&CK v18 introduced Detection Strategies and overhauled Analytics. In 2026 our Top ATT&CK Techniques renewal (TAT2) will evaluate, score, and prioritize techniques with empirical grounding and alignment to defensive action.
The TAT2 project will produce a prioritization methodology for ATT&CK techniques, supported by a fully documented scoring model. One component is prevalence data aggregate from public vendor threat reports. Another component is actionability, scored using ATT&CK v18 Detection Strategies and the mitigations contained in Mappings Explorer. The result is no fixed list. With TAT2, organizations will evaluate relative importance and apply the results in a way that reflects their own threats, environments, and defensive maturity.
As the saying goes, Defenders think in lists. Attackers think in graphs. But threat-informed defenders look at adversary behavior as sequences of actions rather than isolated TTPs. By looking at combinations of behaviors, defenders learn the relationships among them: how some techniques set up other techniques, or how adversaries handle uncertainty and recover from failure. Attack Flow is the language to describe how cyber adversaries combine and sequence various offensive techniques to achieve their goals.
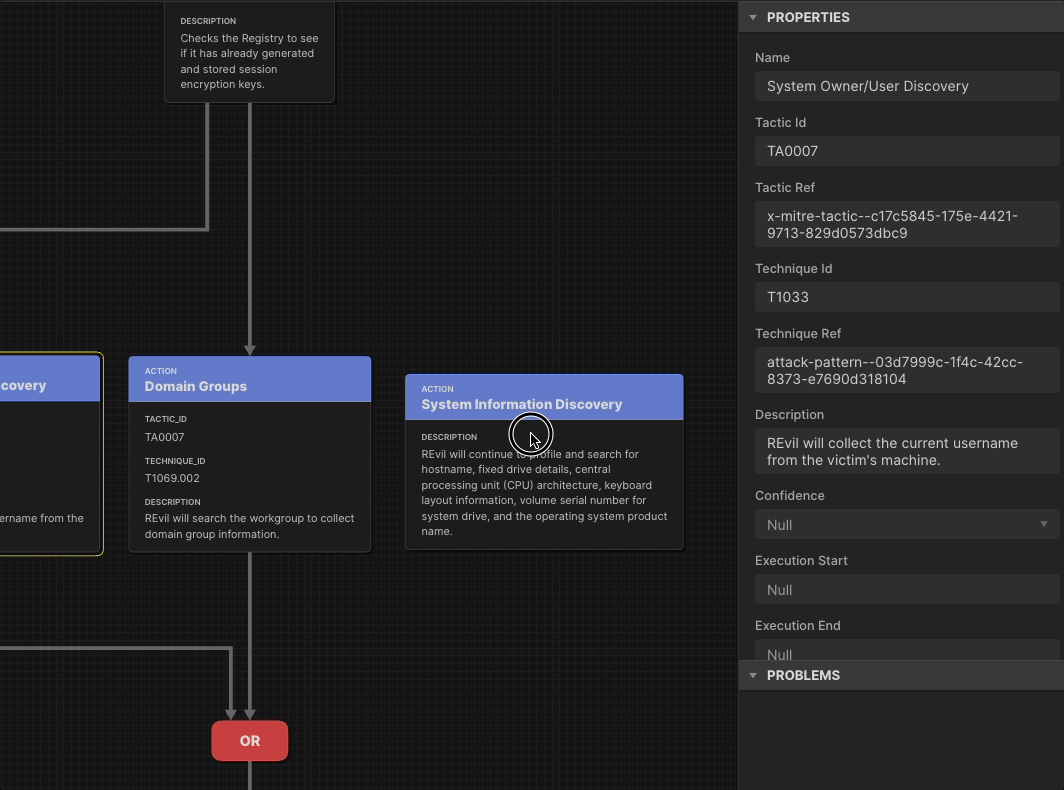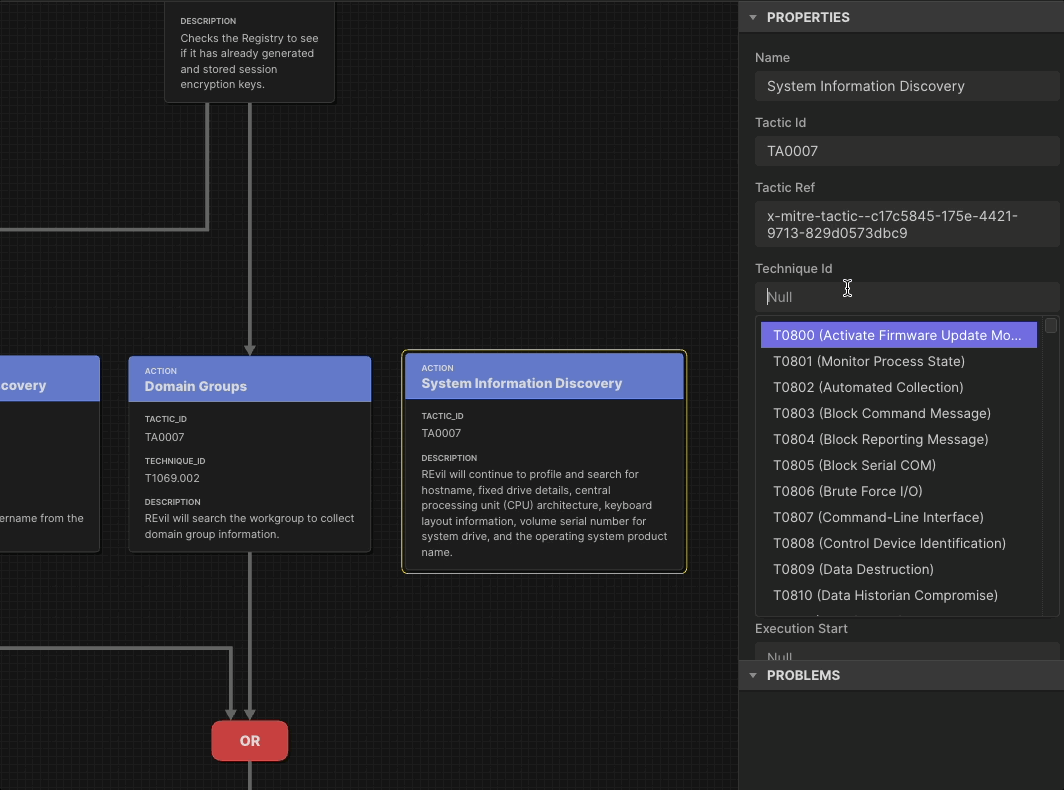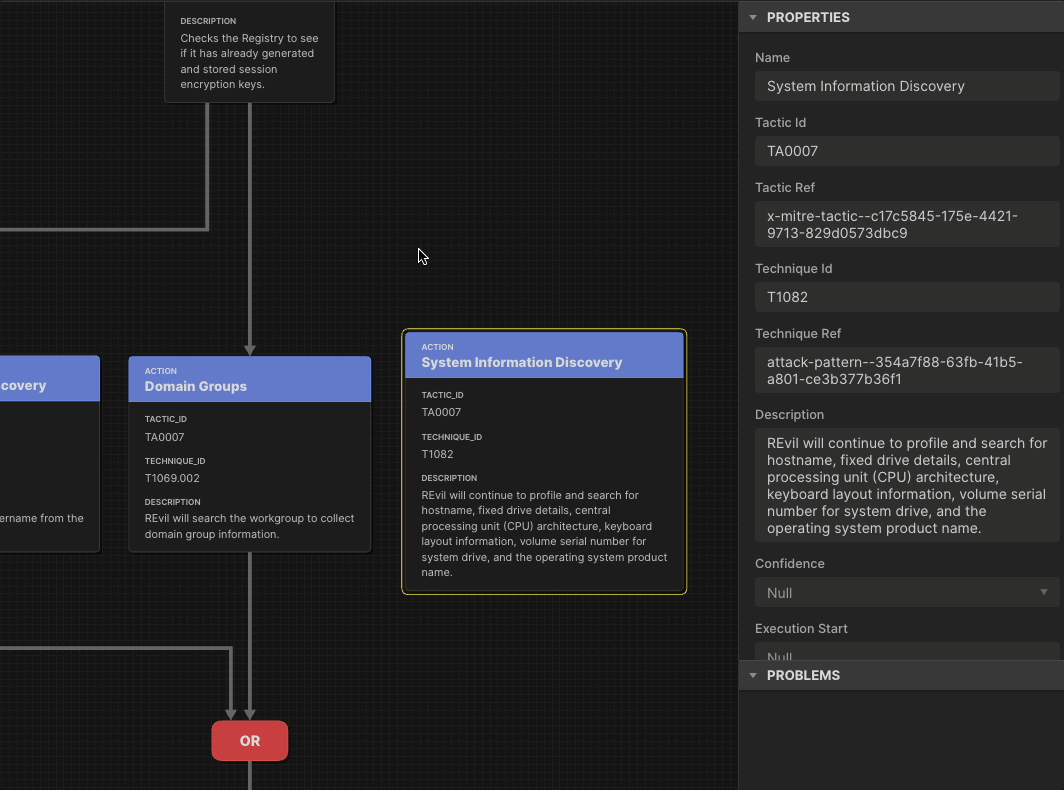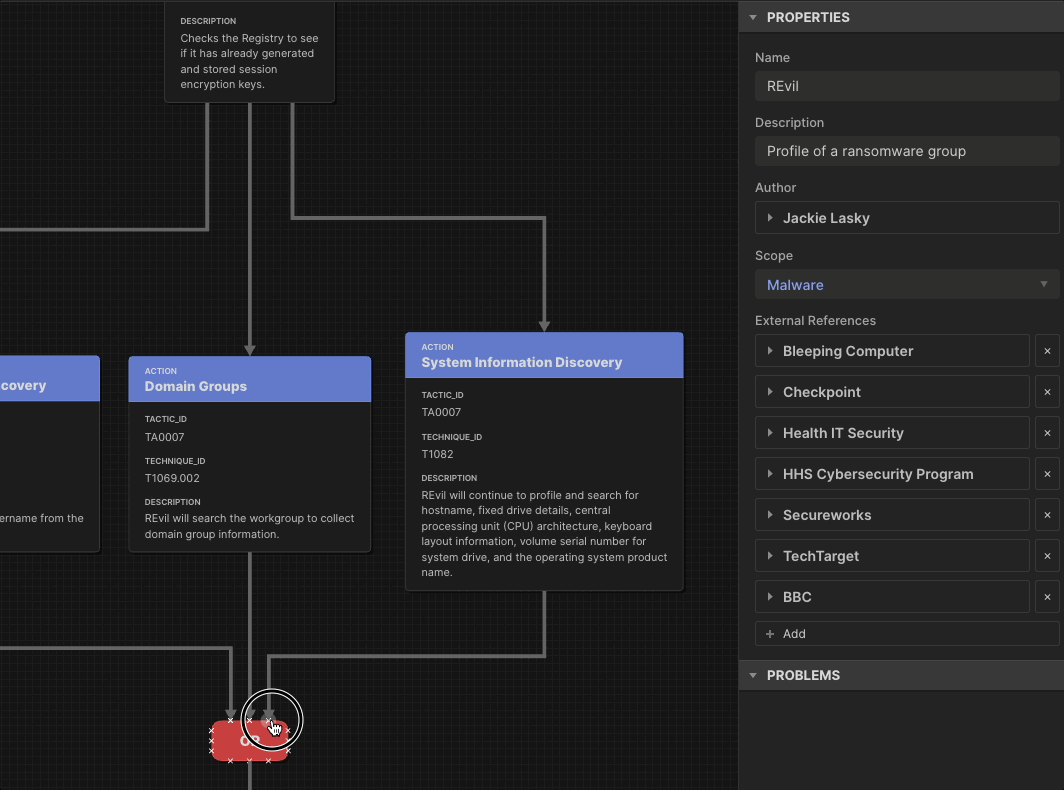
Our research in Attack Flow has produced an on-demand training series and innovation from industry partners. In 2026 we will make it faster for you to build a flow by releasing an updated AI-enabled Attack Flow Builder.
We will also integrate the predictive model from Technique Inference Engine (TIE) into Attack Flow. TIE uses a machine learning model trained on cyber threat intelligence to recommend likely TTPs based on a set of known input TTPs. This project will modernize TIE’s dataset to include techniques tagged to ATT&CK for Enterprise v18.
With TIE, analysts discern what is likely to have happened given the evidence of what did happen. Cyber defenders use TIE’s recommendations to prioritize specific techniques for threat hunting; incident responders use this information to highlight lateral movement and persistence behaviors. Merging TIE into Attack Flow will:
Another highlight of Attack Flow in 2026 is the addition of TTP frameworks such as MITRE ATLAS or ATT&CK for ICS to Attack Flow Builder. Adversaries execute across platforms and Attack Flow will map their journey wherever it may lead.
[Attack Flow] makes it easier than ever to quickly document chains of actions and choke points in adversary activities and show that information in easily consumed visualizations for different stakeholders.
David Vasil: Security Threat Architect, HCA Healthcare
AI-enabled systems are susceptible to traditional cybersecurity vulnerabilities and new attacks. As consumers and organizations integrate AI-enabled systems into their business, adversaries exploit them. Defenders must unite to thwart these new threats.

CTID applies a threat-informed approach to AI security that enables rapid exchange of new threat information, develops approaches to emulating those threats, and provides comprehensive and effective mitigation strategies. Moreover, we acknowledge that there is no pause in real-world attack observations and realistic demonstrations from Al red teams and security groups. In our research we must continually add to the knowledge base of adversary tactics and techniques against Al-enabled systems. In 2026 we will:
Our R&D program has evolved in our consideration of AI. It is not practical to silo our AI research into a single AI project. So CTID will incorporate AI, ML, or automation as appropriate into each threat-informed defense project. Here are some examples:
Threat-informed defense will always be a team sport. We are grateful for your feedback on the products of our research, on how you use CTID resources, and the content of our trainings, workshops, and other engagements. We aim to create widely-used, easily accessible, and practical resources through our R&D program. That is only possible with community support and engaged CTID Research Participants. Your feedback is key to evolving our work and maximizing its impact. Contact us here.
Join us to advance Threat-Informed Defense — CTID Research Participants are thought leaders with sophisticated security teams, advanced practitioners of threat-informed defense, and users of ATT&CK. With the understanding that the cyber challenges we face are bigger than ourselves, our members join CTID prepared to tackle hard problems in a uniquely collaborative environment. If this sounds like your organization, become a CTID Participant.
Stay informed — Be the first to know about R&D project releases by signing up for our Stay Informed newsletter and following us on LinkedIn.
Use CTID R&D and share your feedback — Let us know how you are using CTID R&D and allow us to continually refine our work, making it more accessible and impactful.
© 2026 The MITRE Corporation. Approved for Public Release. ALL RIGHTS RESERVED. Document number
25-02691-5.
Threat-informed defense changes the game on the adversary. Threat-informed defenders read their adversaries’ playbooks and then orchestrate a …
MITRE ATLAS™ analyzed OpenClaw incidents that showcase how AI-first ecosystems introduce new exploit execution paths. OpenClaw is unique because …
Threats to cloud computing span multiple security domains, objectives, and layers of technology. Defenders must protect dynamic, shared …