Cloud Security Built with ATT&CK
Threats to cloud computing span multiple security domains, objectives, and layers of technology. Defenders must protect dynamic, shared …
By Antonia Feffer, Mike Cunningham and Suneel Sundar • May 13, 2025

MITRE ATT&CK® describes the tactics and techniques that have been used by cyber adversaries. Some techniques, such as System Network Configuration Discovery (T1016), are used during campaigns but are not intrinsically malicious. An ambiguous technique is an ATT&CK technique whose observable characteristics are insufficient to determine intent. In such cases, observable data does not allow us to confidently ascertain whether the intent behind the activity is malicious or benign. These ambiguous techniques are not typically used by defenders to detect adversary behavior because they do not provide enough information on their own to determine malicious intent. Ambiguous techniques may also have multiple procedural implementations which are difficult to distinguish from benign user activity until after a forensic investigation has been completed.
Adversaries know this and use living-off-the-land (lotl) techniques for malicious outcomes. Identifying adversarial use of lotl techniques requires deliberate and conclusive detection methods to minimize false positives. In the end, detection engineers need to infer motive from security logs.
In partnership with Citigroup, Crowdstrike, Fujitsu, Fortinet, HCA Healthcare, Lloyds Banking Group, and The Microsoft Corporation, the Center for Threat-Informed Defense expanded Summiting the Pyramid to create Ambiguous Techniques, a methodology for determining the context required to discern between malicious and benign behavior while maintaining a robust detection that has high accuracy and is resistant to adversary evasion.
We classify three types of context that a defender can use to discern an actor’s intent: peripheral-level, chain-level, and technique-level. Each of these contexts adds information to the usage of a technique, which is necessary to determine intent.
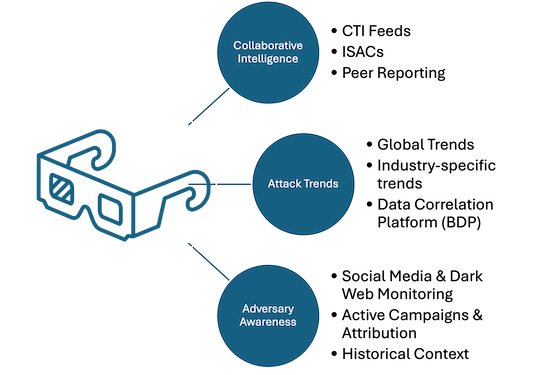
Peripheral-level context includes external information that is most valuable for defending against potential attacks targeting your network. This is an “outside-looking-in” perspective.
We apply peripheral-level context to techniques associated with pre-compromise activities, such as those in the Reconnaissance tactic. As a result, the detections generated in this category are proactive in nature. Peripheral-level context derives from cyber threat intelligence on threats to your network, industry, or sector.
Chain-level context comes from observed co-occurring techniques - those that occur before, after, or concurrently with the specific technique of interest - in order to establish intent. We examined chain-level context techniques by leveraging data from our repository of Attack Flows and our Adversary Emulation Library.
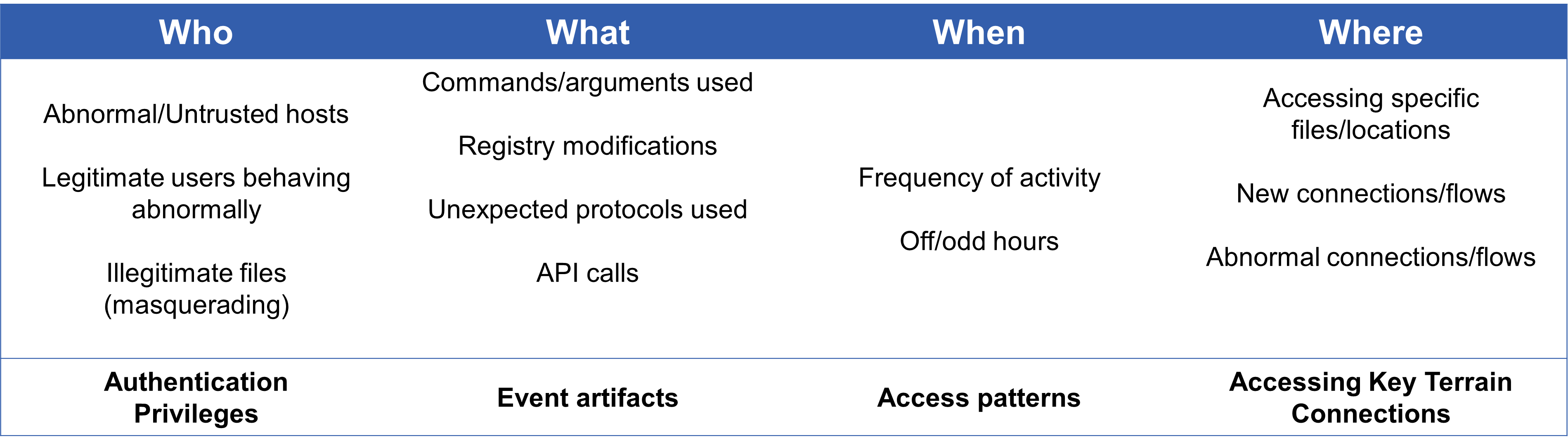
Technique-level context identifies artifacts related to the detection of a single technique. To determine technique-level context, we break down the detection criteria into four categories: Who, What, When, and Where.
By organizing detection criteria into these categories, we provide a structured approach to developing detection analytics and identifying technique-level differentiators. This framework enables defenders to focus on key aspects of network activity - authentication, artifacts, timing, and terrain - while leveraging baseline data and behavioral analysis to detect anomalies and differentiate between benign and malicious behavior.
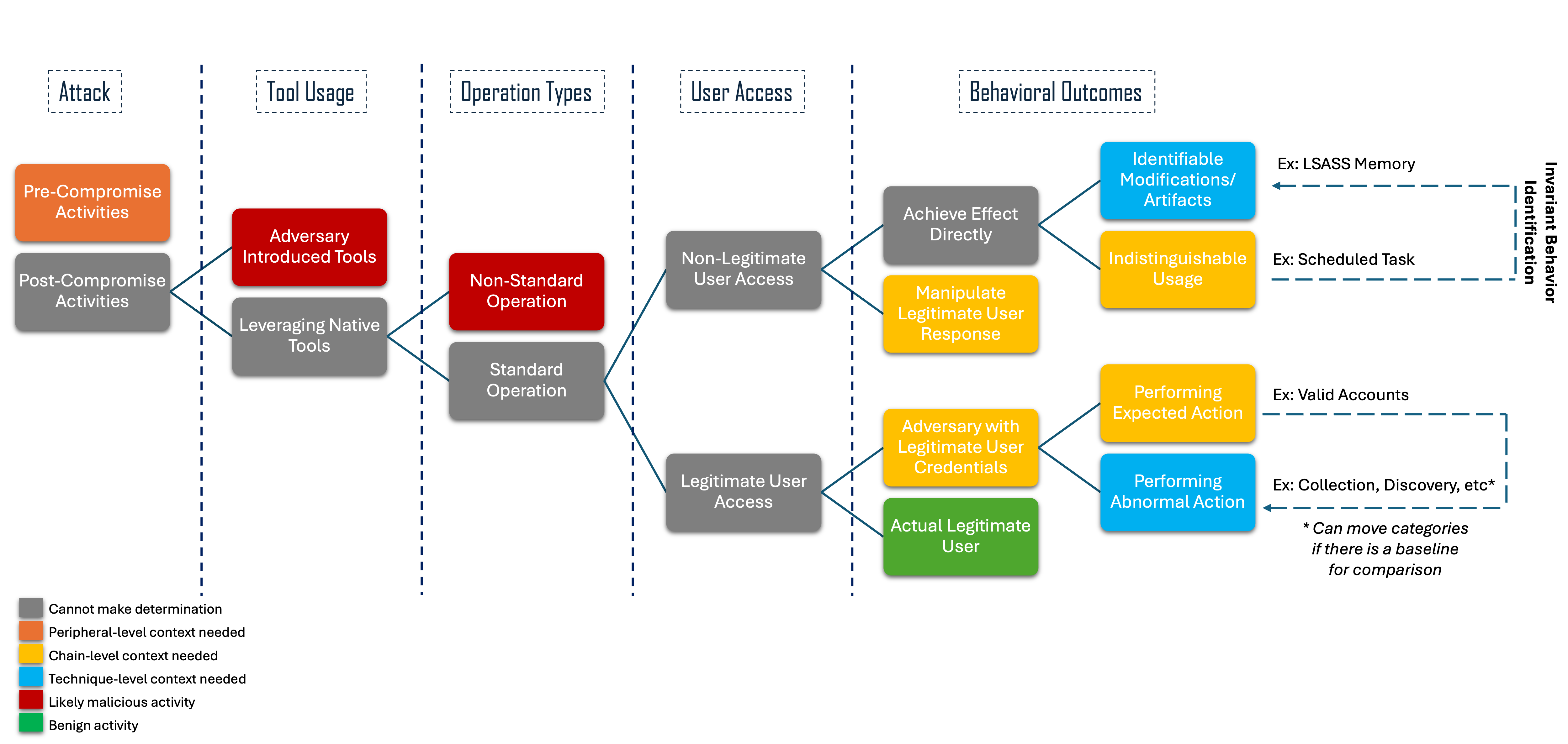
The above flowchart represents the progression of activities during an incident, and which type of context to use as a defender. The flow starts from the onset of the attack behavior and moves toward behavioral specifics. The legend at the bottom-left highlights the different contexts, with gray representing not enough information to make a determination. For a deeper dive of how to use the context flow charts, head on over to our project website.
Once we have determined which context to use, we combine analytics to improve the fidelity of our detections. We identified two distinct approaches when chaining analytics together: direct correlation and loose correlation. These methods are designed for different scenarios and are generally not interchangeable. Each serves a specific purpose depending on the level of certainty and the nature of the adversary’s actions.
While some implementations of analytic chaining attempt to enforce strict sequencing, we have found that complexity and cost of such implementations often outweigh the benefits. Thus, adoption of strictly sequences analytic chains is limited. Loose correlation allowing organizations to adapt thresholds and analytics to their specific environments while maintaining a balance between detection accuracy and operational feasibility.
The Ambiguous Techniques framework determines the intent behind a technique through context. It offers a way to develop analytics for these techniques, enhancing efficiency by reducing resource burden and increasing visibility. We have included several example analytics that demonstrate how to improve your current detections. Defenders can apply these insights by integrating our guidance into their own development processes, using the documentation to create robust detections.
Please take our work and adapt it and extend it, and contribute back to the AT knowledge base by identifying attack chains and refining technique observables.
Future Summiting detection engineering work will focus on how compound and layered detections can be used to build robust detections, as well as how we can effectively measure multi-faceted detection coverage.
Tell us how you are using our work! If you have any feedback, technical questions, concerns, or contributions you’d like to make to the project, email us at ctid@mitre.org
© 2025 The MITRE Corporation. Approved for Public Release. ALL RIGHTS RESERVED. Document number
25-1550.
Threats to cloud computing span multiple security domains, objectives, and layers of technology. Defenders must protect dynamic, shared …
INFORM builds on M3TID to translate threat intelligence, defensive measures, and test & evaluation into a measurable, repeatable practice. …
Threat-informed defenders can use ATT&CK Sync and the enhanced Mappings Editor to keep ATT&CK-based tools and mappings current with major …