A Threat-Informed Community is Necessary for Defense to Function
Threat-informed defense changes the game on the adversary. Threat-informed defenders read their adversaries’ playbooks and then orchestrate a …
By Suneel Sundar • April 22, 2025

The Center for Threat-Informed Defense has published the results of three new projects so far in 2025, as well as three updates within the corpus of Security Capability Mappings. Within the Center, our most impactful work comes from enabling efficiency and innovation across the industry, and we do so in our three key problem areas:

Threat-informed defense aligns defensive measures to real-world observations of adversary tradecraft. Where cybersecurity often focused on brittle indicators of compromise that are easy for an adversary to change, threat-informed defense addresses the root adversary behavior, which is more stable over time and more expensive for adversaries to change. The result is more efficient use of defenders’ resources and a more robust program of prevention, detection, and response.
A principle that guides our research program is Threat-Informed Defense applies broadly. In 2025 the Center will broaden our R&D program and apply a threat-informed approach to securing artificial intelligence enabled systems and fighting financial fraud.
In 2024, the Center and 16 of our member organizations applied the principles of threat-informed defense to AI-enabled systems in our first Secure AI project. This resulted in a significant expansion of MITRE ATLAS™ with case studies that are curated by and relevant to industry partners, as well as the launch of the AI Incident Sharing Initiative.

These successes demonstrated that there is more the Center can and will do in AI research. In 2025, we will further our AI Focus Area in four ways:
Expand the ATLAS Knowledge Base. Capture and characterize the evolving threats to AI-enabled systems by collecting empirical data from real-world observations and incorporate findings as structured updates to ATLAS. Furthermore, this year’s research includes adversary behaviors such as malicious use of AI (AI-enabled attacks), especially as it pertains to attacks accelerated by GenAI.
Expedite AI Incident Sharing to enable rapid characterization and dissemination of anonymized information about attacks and failures in AI-enabled systems.
Verifiable AI Vulnerability Discovery. Integrate existing model scanning and adversarial attack tools into a common platform to enable the creation of verifiable and reproduceable vulnerability reports in collaboration with CWE and CVE AI working groups and the AI Risk Database.
AI Red Teaming and Adversary Emulation. Develop strategies and guidance in the form of structured playbooks to emulate threats to AI-enabled systems so that defenders can test AI-enabled system defenses against known threats and collect telemetry for downstream defensive forensics.
Threat-informed defense is the systematic application of a deep understanding of adversary tradecraft and technology to improve defenses.
It identifies known adversary behavior, relevant to an organization’s threat model, and fosters a community-driven approach to enable an organization to proactively defend, self-assess, and improve defenses against those known threats.
The problem of financial fraud is prime for the application of threat-informed defense. When we address financial fraud at the time of the material event, we are necessarily reacting to a fraud actor. It would be like placing our controls for intellectual property theft exclusively in the exfiltration stage. We will develop resources to apply intelligence and defensive measures enabling fraud teams to act earlier.
The Center’s Fight Financial Fraud research area will unite the events detected through cyber means with the material fraud event. This requires data fusion and analysis. Through collaborative research we will create a shared language for threat-informed financial fraud defense.
Sign up here to contribute to this effort. The goals of fraudsters hurt us all: social engineering, money laundering, cash out, and more. Our collective success requires that we identify the varied sources of telemetry for fraud detection, and we document the tactics and techniques used by fraud actors.
A second principle of the Center’s research program is Good work becomes better work. We observe which prior Center publications are impactful to the community, and we hear your suggestions to extend prior research. Some of our 2025 projects build upon Summiting the Pyramid, Security Capability Mappings, and Attack Flow.
MITRE ATT&CK® is a comprehensive reference of publicly reported adversary tactics, techniques and procedures (TTPs), including how to detect and mitigate them. However, ATT&CK techniques are not all intrinsically malicious. In fact, threat actors commonly achieve their objectives by living-off-the-land, leveraging native platform capabilities that may be critical business enablers. These ambiguous techniques are difficult to detect as adversary behaviors due to the need to separate benign activity from malicious activity. The Ambiguous Techniques project identified core behaviors and observables associated with ambiguous techniques and built robust detections for them. This research will lower the false positive rate of ambiguous techniques. It will be available to you in May 2025. Register here to Stay Informed about this and all our R&D project publications.
ATT&CK updates to a new major version twice per year, and security vendors constantly change their offerings. The Center’s Mappings Program updates all the mapping resources to reflect the most current versions of native platform security and adversary techniques.
Security capability mappings correlate the defensive measures you have procured to the threats that keep you awake. We have shared updated mappings resources to the community on the Mappings Explorer platform.
The Prioritize Known Exploited Vulnerabilities with ATT&CK project bridges threat management and vulnerability management by connecting Common Vulnerabilities and Exposures (CVEs) that are actively exploited by adversaries to the impact of exploitation. We completed 800 mappings for over 400 CVEs from the Cybersecurity and Infrastructure Security Agency’s Known Exploited Vulnerabilities (KEVs) Catalog. Our research prioritized recent vulnerabilities and the most exploited ones as determined by inclusion in CISA’s Top Routinely Exploited Lists.
In January 2025 we published our mappings of security capabilities in hardware to adversary behaviors in Security Stack Mappings – Hardware-Enabled Defense. This project demonstrates the effectiveness of a hardware capability with operating system, anti-virus, or endpoint detection and response software features.
The Cyber Risk Institute (CRI) profile includes controls from the NIST Cyber Security Framework tailored to financial sector needs. In June 2025, we publish Threat-Informed Defense for the Financial Sector project, which maps the CRI’s financial sector profile to adversary behaviors. This gives cyber defenders in financial services organizations resources for threat-informed analysis and decision-making.
Later this year, we will share Threat-Informed Defense for Cloud. Threats to cloud computing cover multiple security domains, objectives, and aspects of cloud technology. This project will create a common technical foundation for implementing cloud-native capabilities to mitigate threats to cloud environments.
We built Attack Flow as the data model for representing the sequence of adversary behaviors.
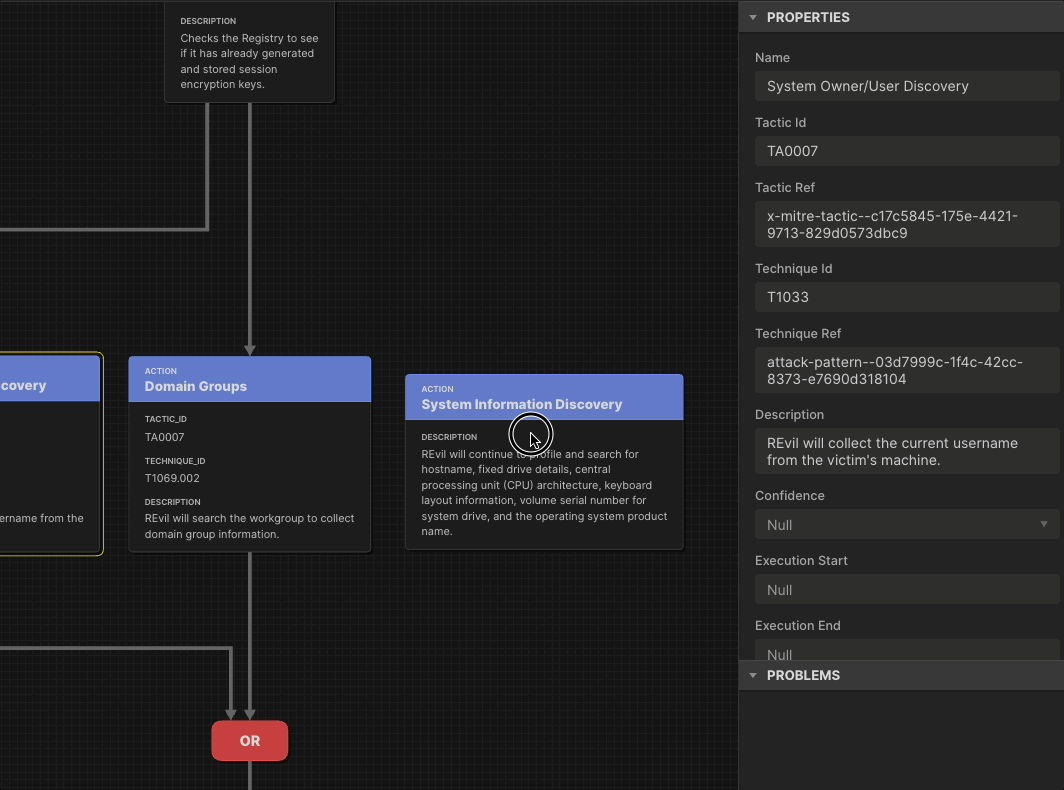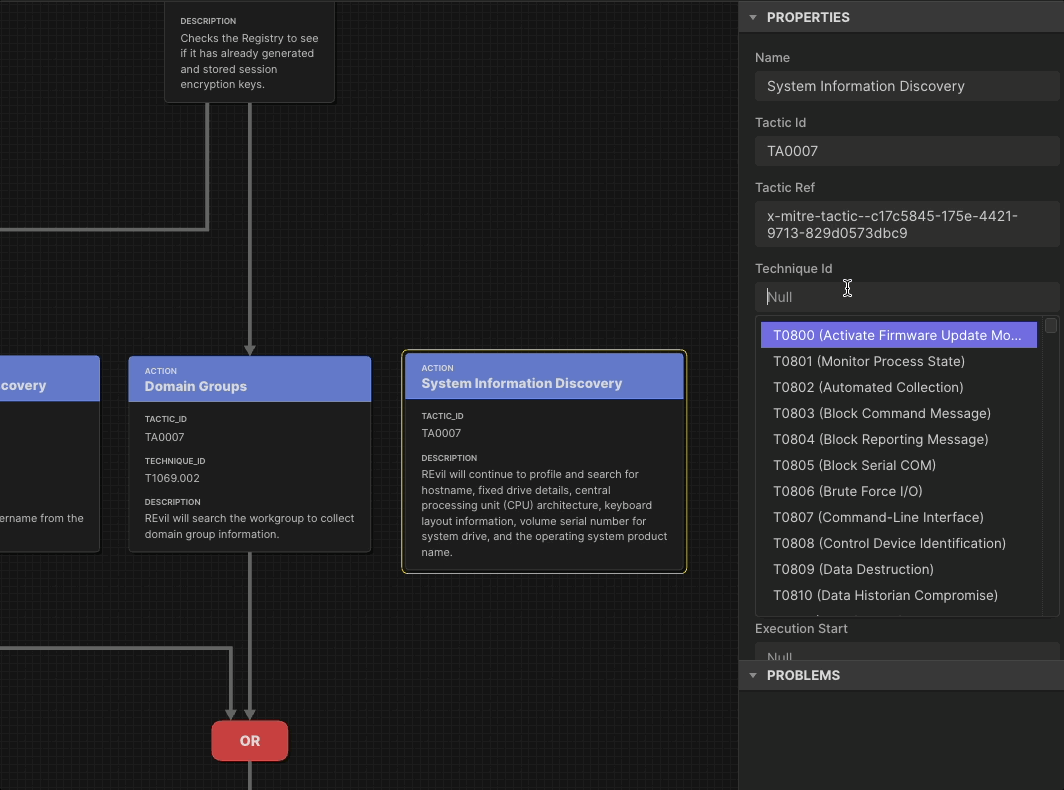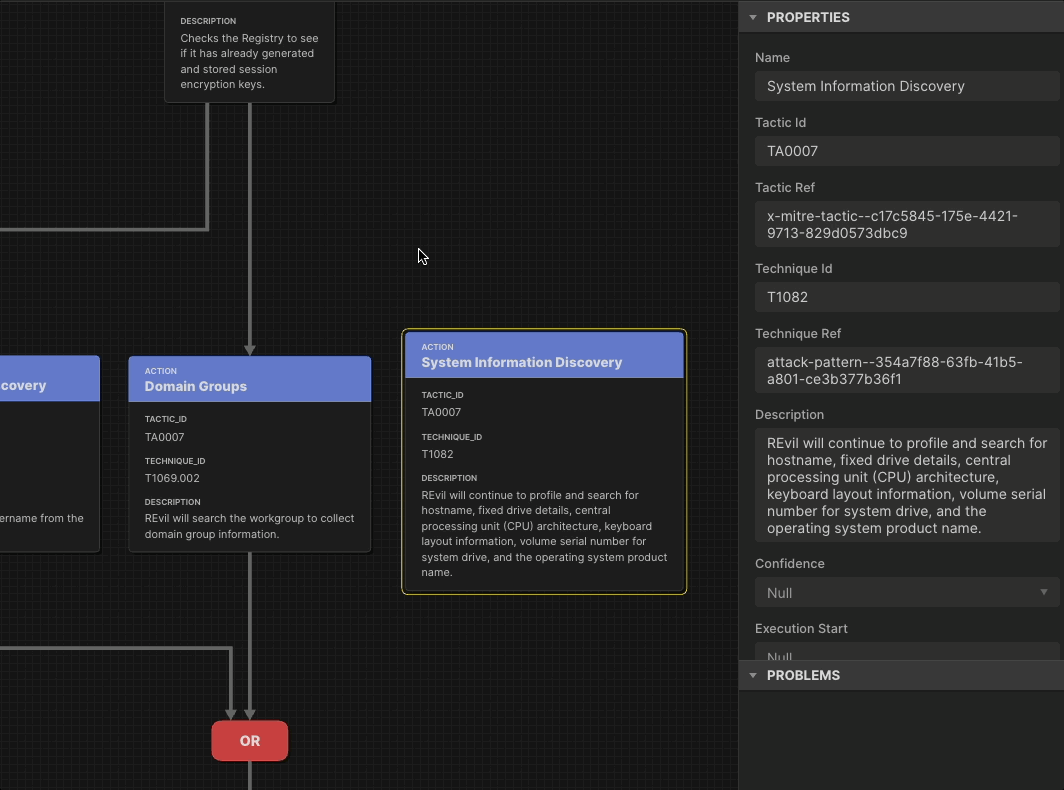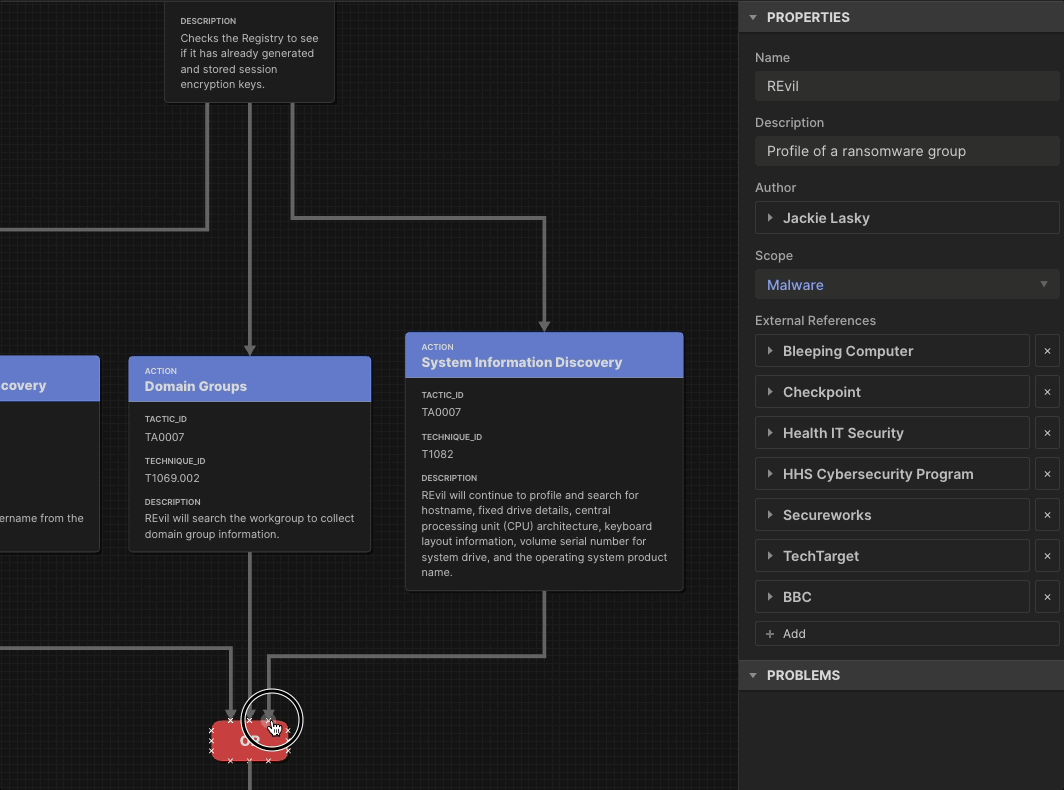
To defend against the adversaries’ sequence of behaviors, we have a data model with a web application that allows you to build and visualize those attack flows. Publishing June 2025, Flow Visualization will reap the benefits of this powerful data model by providing a users’ guide to Attack Flow Builder and template visualizations for important use cases. We will also build more flows into our set of Examples.
Threat-informed defense enables the collective resources of all defenders to be greater than those of any one adversary. So, we develop those resources for the collective while delivering our research. This is the third principle of Center research: Share the How. Making our R&D usable to the worldwide community of threat-informed defenders is an explicitly stated goal of all who are part of the Center for Threat-Informed Defense.
The Center creates operational resources for threat-informed defenders through our collaborative research and development program. Adoption of those resources by Center members and the worldwide community of threat-informed defenders is a Center goal. The Center and members have observed that adoption improves when users are trained in why, when, and how to implement the work. Prominent examples of this include Summiting the Pyramid training, a Secure AI webinar, and Attack Flow workshops.
We have embraced our responsibility by creating our Threat-Informed Training and Outreach project. This project will develop training modules for Center resources and deliver trainings at conferences, webinars, and to Center members. The Center will also record and distribute freely online the training we create, just as we give the products of our R&D program.
The Center’s initial Measure, Maximize, Mature Threat-Informed Defense (M3TID) project described the aspects of threat-informed defense (TID) and answered, “what does a healthy implementation of TID look like, both now and in the future?” Threat Informed-Defenders – from the Security Operations Center (SOC) analyst, who responds in real-time, to the Chief Information Security Officer (CISO), who sets the vision and drives defensive strategy – allocate resources to further impede the adversary in achieving their objective. M3TID started with a breadth-first approach, identifying the three dimensions of threat-informed defense and the first five components of each dimension.
In our follow-on INFORM Your Defense project, the Center will collect data on the dimensions and components that the Center has hypothesized will prove most important based on existing research and experience. Based on evidence, we seek to incorporate more granular sub-components with associated levels, more objective criteria for levels that tied to specific data sources and assessed by a 3rd party or automation, and additional components within the dimensions. This project may also modify the model to improve on the quantification of levels and modify the scoring algorithm to better align with evidence on the relative importance of each component to bottom-line security efficacy.
We are grateful to the global community who has joined our mission to advance the state of the art and the state of the practice in threat-informed defense. We highlight the sponsors and participants of our Asia-Pacific ATT&CK Community Workshop: our host Citigroup, and sponsors Acronis, AttackIQ, Ensign Infosecurity, Fortinet, SquareX, and Trainocate. This event in Singapore anchors the Asia-Pacific region into our global series of community events with EU ATT&CK in Belgium, and ATT&CKcon in the U.S. Global adoption leads to impact and community feedback that enhances Center R&D.
Second, the Benefactor Program enables the global community to advance critical, public interest cybersecurity programs such as MITRE ATT&CK®, Caldera™, MITRE Engage™, and the Center for Threat-Informed Defense through charitable giving. Our benefactors support independent research in the public interest. We thank Acalvio, Coalfire, Limber Security, NVISO, SANS, SOC Prime, Tidal Cyber, and Zimperium for financially supporting our research to change the game on the adversary.

The Center’s mission is to advance the state of the art and the state of the practice in threat-informed defense globally. We create widely usable, easily accessible, and practical resources for all. That is only possible with community support and engaged Center Participants. Your operational challenges, shared across organizations, sectors, and across regions, incite our impactful solutions. You’ve now read our plans for 2025; tell us what you need most from the Center.
Stay informed — Be the first to know about R&D project releases by signing up for our newsletter and following us on LinkedIn.
Utilize Center R&D and share your feedback — Use our work to advance threat-informed defense in your organization and ultimately change the game on the adversary. Tell us how you use Center R&D, and we will refine our work to be more accessible and impactful.
Join us to support and advance the R&D program — Our Participants are thought leaders with sophisticated security teams that are advanced practitioners of threat-informed defense and users of ATT&CK. With the understanding that the cyber challenges we face are bigger than ourselves, our members join the Center prepared to tackle hard problems in a uniquely collaborative environment. If this sounds like your organization, learn more here about how to become a Center Participant.
© 2025 The MITRE Corporation. Approved for Public Release. ALL RIGHTS RESERVED. Document number
25-00912-4.
Threat-informed defense changes the game on the adversary. Threat-informed defenders read their adversaries’ playbooks and then orchestrate a …
MITRE ATLAS™ analyzed OpenClaw incidents that showcase how AI-first ecosystems introduce new exploit execution paths. OpenClaw is unique because …
Threats to cloud computing span multiple security domains, objectives, and layers of technology. Defenders must protect dynamic, shared …