Cloud Security Built with ATT&CK
Threats to cloud computing span multiple security domains, objectives, and layers of technology. Defenders must protect dynamic, shared …
By Tiffany Bergeron, Mike Cunningham and Suneel Sundar • February 13, 2025
Historically, vulnerability management and threat management have been separate disciplines, but in a risk-focused world, they need to be brought together. Defenders struggle to integrate vulnerability and threat information and lack a consistent view of how adversaries use vulnerabilities to achieve their goals. Without this context, it is difficult to appropriately prioritize vulnerabilities.
Back in 2021, the Center for Threat-Informed Defense, developed a methodology to use the adversary behaviors described in MITRE ATT&CK® to characterize the impact of vulnerabilities from CVE® in order to bridge vulnerability management and threat management. Vulnerability reporters and researchers can use the methodology to describe the impact of vulnerabilities more clearly and consistently. When used in a vulnerability report, ATT&CK’s tactics and techniques enable defenders to quickly understand how a vulnerability can impact them, helping defenders integrate vulnerability information into their risk models and identify appropriate compensating security controls.
This methodology aims to establish a critical connection between vulnerability management, threat modeling, and compensating controls. CVEs linked to ATT&CK techniques can empower defenders to better assess the true risk posed by specific vulnerabilities in their environment. When we first applied this methodology, it became clear that mapping all CVEs to ATT&CK was not feasible. As of this publication, there are more than 240,000 CVE Records. Trying to protect against every vulnerability on the list is cost-ineffective and daunting, if not impossible. To help the cyber community keep pace with threat activity and manage vulnerabilities, Department of Homeland Security (DHS) Cybersecurity and Infrastructure Security Agency (CISA) maintains the Known Exploited Vulnerabilities (KEV) Catalog, the authoritative source of CVEs that have been confirmed as being exploited.
To help focus defenders on this subset of CVEs, we created the Prioritize Known Exploited Vulnerabilities (PKEV) project in collaboration with Center participants, including AttackIQ, Citigroup, HCA Healthcare, JPMorgan Chase Bank N.A., and Microsoft Corporation. With PKEV, defenders make threat-informed vulnerability management and risk management decisions by focusing resources on relevant, active exploits, saving both time and money.
The resources for the project — mappings, ATT&CK Navigator layers, and the mapping methodology — are all available in Mappings Explorer. Mappings Explorer enables defenders to access and explore the Center’s mapped security frameworks, bridging the gap between risk management and threat informed defense.
The Center’s mapping methodology for KEVs categorizes attack steps by method of exploitation, primary impact, and secondary impacts of exploitation. Using these categories, we create a vulnerability impact description template such as: The vulnerability allows the attacker to use [Exploitation Technique] which enables the [Primary Impact], which leads to [Secondary Impact].

Our team prioritized mapping the KEV Catalog by frequency and recency, resulting in about 800 mappings for over 400 CVEs. The most exploited KEVs as determined by inclusion in CISA’s Top Routinely Exploited Lists for years 2020 through 2023 are included in the mapping repository. The KEV Catalog includes vulnerabilities going back to 2002; mapping priority was given to more recent vulnerabilities by CVE date (2021 on).
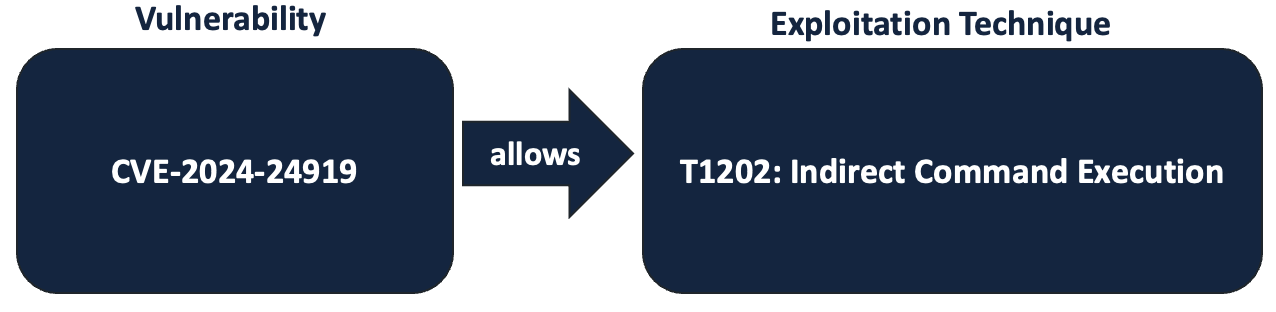
In 2024, Checkpoint disclosed CVE-2024-24919, which is a path traversal exploit that allows an adversary to execute root-level commands on the affected device. This is the exploitation technique, mapped to T1202: Indirect Command Execution.
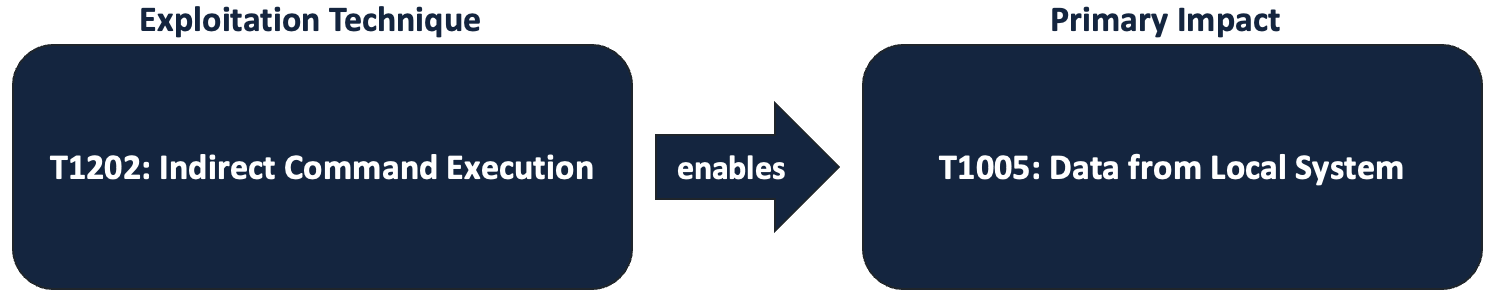
After the CVE was released, security research firm, Greynoise, saw malicious actors exploiting the vulnerability which enabled them to search the local file system for sensitive data. This is the primary impact of the exploit, mapped to T1005: Data from Local System.
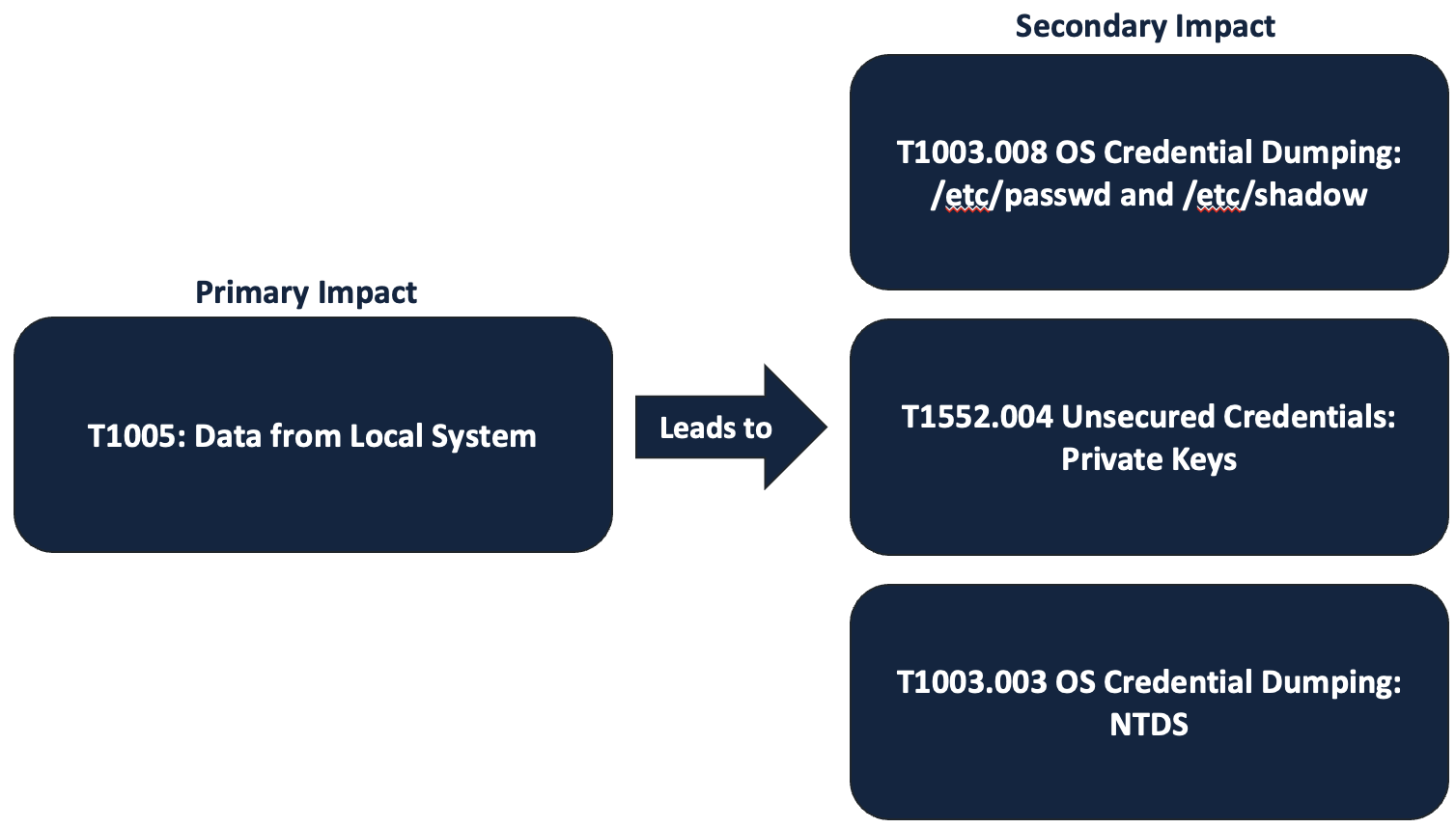
The malicious actors were then seen reading, and presumably exfiltrating, data from various sensitive files like /etc/shadow and .ssh/authorized_keys, both of which contain information related to user authentication. Another security research firm, Mnemonic, has seen malicious actors exploiting this vulnerability to access Active Directory credentials by extracting ntds.dit.
These three observed techniques are the secondary impact, respectively mapped to T1003.008: OS Credential Dumping: /etc/passwd and /etc/shadow, T1552.004: Unsecured Credentials: Private Keys, and T1003:003: OS Credential Dumping: NTDS.
By applying the mapping methodology, we have created the vulnerability impact description:
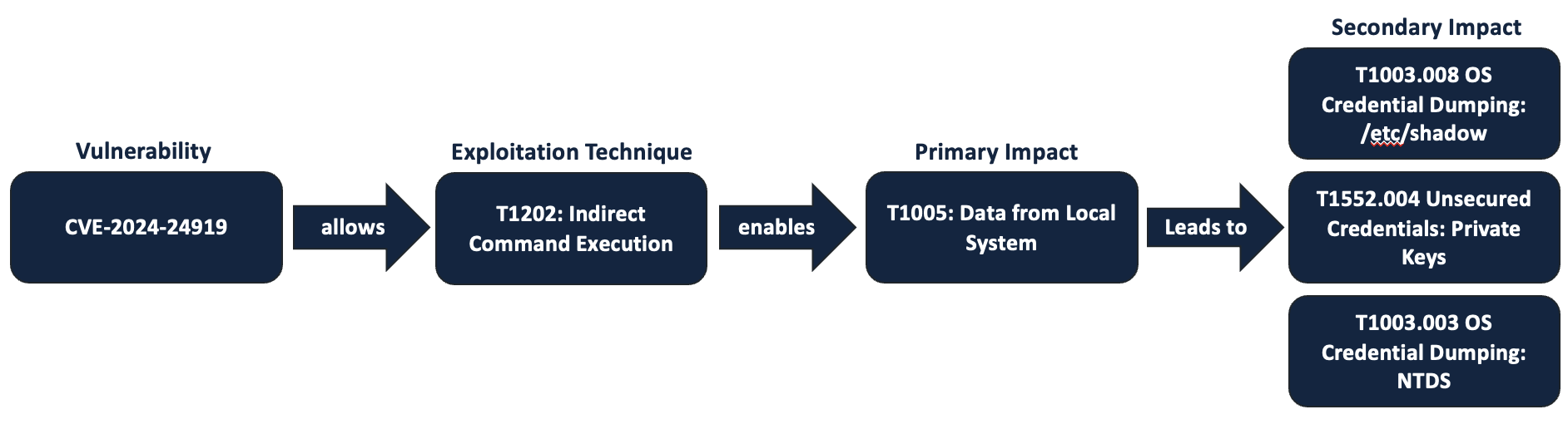
PKEV characterizes the exploitation and impact of vulnerabilities using the adversary behaviors described in ATT&CK. This connects vulnerability management, threat modeling, and compensating controls. A threat-informed approach to vulnerability and risk management:
We welcome your feedback and contributions to continue to advance the PKEV mapping project. There are several ways that you can get involved with this and other mapping projects to help advance threat-informed defense:
You are also welcome to submit issues for any technical questions/concerns or contact the Center directly for more general inquiries.
The Center is a non-profit, privately funded research and development organization operated by MITRE. The Center’s mission is to advance the state of the art and the state of the practice in threat-informed defense globally. Comprised of participant organizations from around the globe with highly sophisticated security teams, the Center builds on MITRE ATT&CK®, an important foundation for threat-informed defense used by security teams and vendors in their enterprise security operations. Because the Center operates for the public good, outputs of its research and development are available publicly and for the benefit of all.
© 2025 The MITRE Corporation. Approved for Public Release. ALL RIGHTS RESERVED. Document number
CT0138.
Threats to cloud computing span multiple security domains, objectives, and layers of technology. Defenders must protect dynamic, shared …
INFORM builds on M3TID to translate threat intelligence, defensive measures, and test & evaluation into a measurable, repeatable practice. …
Threat-informed defenders can use ATT&CK Sync and the enhanced Mappings Editor to keep ATT&CK-based tools and mappings current with major …