Context to Confidence: The Next Phase of Ambiguous Techniques Research
MITRE CTID’s latest ambiguous techniques research turns context into confidence with minimum telemetry requirements and a confidence scoring …
By Suneel Sundar • November 22, 2024
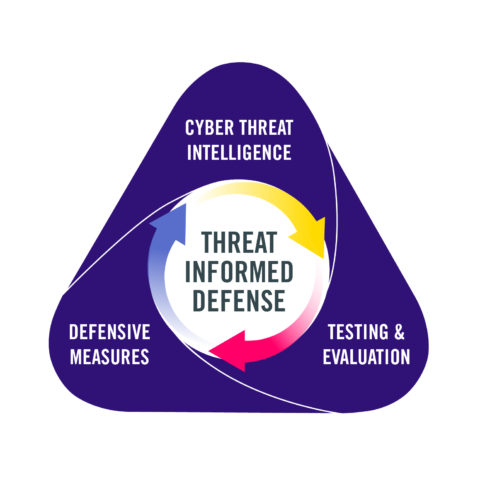
This is the third and final part of the Center for Threat-Informed Defense 2024 R&D Roadmap. In Part One and Part Two, we shared the Center’s guiding principles for research in 2024.
Threat-informed defense aligns defensive measures to real-world observations of adversary tradecraft. Where cybersecurity often focused on brittle indicators of compromise that are easy for an adversary to change, threat-informed defense focuses energy on adversary behavior, which is more stable over time and more expensive for adversaries to evade. The result is more efficient use of defenders’ resources and a more robust program of prevention, detection, and response.
The third principle for our 2024 research program is Threat-Informed Defense applies broadly. You will find Center projects that apply threat-informed defense to artificial intelligence enabled systems, to hardware, and a variety of platforms.
In 2024, the Center and 16 of our member organizations applied the principles of threat-informed defense to AI-enabled systems in our first Secure AI project. This resulted in a significant expansion of the MITRE ATLAS database with case studies that are curated by and relevant to industry partners, as well as the launch of the AI Incident Sharing Initiative.
These successes demonstrated that there is more the Center can and will do in AI security research. In 2025, we will further our AI Focus Area in four ways:
MITRE ATT&CK techniques are not all intrinsically malicious. In fact, threat actors commonly achieve their objectives by living-off-the-land, leveraging native platform capabilities that may be critical business enablers. These ambiguous techniques are difficult to detect as adversary behaviors due to the need to separate benign activity from malicious activity. Our Ambiguous Techniques project will identify core behaviors and observables associated with ambiguous techniques and build robust detections for them. This research will lower the false positive rate of ambiguous techniques.
We endeavor to map security capabilities in hardware to adversary behaviors in Security Stack Mappings — Hardware-Enabled Defense. This will require us to extend our mappings methodology. In this project we will determine how hardware capabilities, in tandem with an operating system,
Such integration is essential for proactive and robust threat-informed defense for enterprise environments. We have included emulation plans for some techniques to demonstrate the effectiveness of the hardware capability with anti-virus or endpoint detection and response software features. These results will be published in January 2025 and affect billions of enterprise-class systems worldwide.
Following the development of the Center’s first Linux-based adversary emulation plan OceanLotus, we see the need for Linux defenders to possess the expanded resources and awareness as every other threat-informed defender. Currently, Linux OS native security functions have not matured to log data required to detect adversarial behaviors using ATT&CK-based hunting methodologies. The Center’s Threat-Informed Defense for Linux project will create and validate open-source tooling configurations for Linux compatible with ATT&CK-based hunting methodologies that are suitable for operational environments.
Cybersecurity analysts encounter novel situations every day and must research, study, and evaluate exponentially more options for defense than attackers. This GenAI for Threat-Informed Defense project will use Generative AI, such as LLMs and chatbots, to provide contextual information for cybersecurity scenarios and automate common tasks in the analyst’s workflow. This research will demonstrate that GenAI can deliver actionable advice to cyber analysts at scale, enabling defenders to respond to novel situations while automating repetitive tasks out of the analyst’s queue.
Our R&D program grows with the needs of defenders — your needs. So you influence our next research project, as you have influenced all that we have released to the community to date. Here are your next steps to make a difference as a threat-informed defender.
Read Part One and Part Two of the Center’s 2024 R&D Roadmap Update.
Stay informed — Be the first to know about R&D project releases by signing up for our newsletter and following us on LinkedIn.
Use Center R&D and share your feedback — Using our work to advance threat-informed defense in your organization goes a long way to ultimately changing the game on the adversary. Letting us know how you are using Center R&D allows us to continually refine our work, making it more accessible and impactful.
Join us to advance Threat-Informed Defense — Our Participants are thought leaders with sophisticated security teams that are advanced practitioners of threat-informed defense and users of ATT&CK. With the understanding that the cyber challenges we face are bigger than ourselves, our members join the Center prepared to tackle hard problems in a uniquely collaborative environment. If this sounds like your organization, learn more here about how to become a Center Participant.
© 2024 The MITRE Corporation. Approved for Public Release. ALL RIGHTS RESERVED. Document number
CT0132.
MITRE CTID’s latest ambiguous techniques research turns context into confidence with minimum telemetry requirements and a confidence scoring …
Threat-informed defense changes the game on the adversary. Threat-informed defenders read their adversaries’ playbooks and then orchestrate a …
MITRE ATLAS™ analyzed OpenClaw incidents that showcase how AI-first ecosystems introduce new exploit execution paths. OpenClaw is unique because …