Cloud Security Built with ATT&CK
Threats to cloud computing span multiple security domains, objectives, and layers of technology. Defenders must protect dynamic, shared …
By Suneel Sundar • November 22, 2024

In Part One of our 2024 Roadmap Update, we shared that the Center for Threat-Informed Defense shaped our R&D program upon three principles; first was
Good work becomes better work. We observed which prior Center publications are impactful to the community, and we heard from you how our research can provide further solutions. Some of our 2024 projects build upon Summiting the Pyramid, Security Capability Mappings, and Attack Flow.
Our mission is to advance the state of the art and state of the practice in threat-informed defense globally. To make that transition from art to practice for all defenders, our second principle is Share the how.
We made a conscious investment to make new releases more accessible. What once might have been a GitHub directory is now a mobile-friendly browser-based application. And we went one step further by developing resources to train threat-informed defenders how to apply our work. Threat-informed defense enables the collective resources of all defenders to be greater than those of any one adversary. So we develop those resources for the collective in the course of delivering our research.
In 2024, we actively participated with the community in the application of threat-informed defense through virtual and in-person training, threat-informed exercises, and bespoke applications of our project resources in specific environments.
This Center initiative began at the Asia-Pacific ATT&CK Community Workshop in April 2024. Prior to the workshop the Center offered training to identify which data sources identify particular adversary techniques and practical instruction in how to refine detection rules based on those data sources. These derive from the Center’s Sensor Mappings to ATT&CK and Summiting the Pyramid project releases.
We learned from our training cohort how these resources would be impactful in their threat scenarios. To continue our learning loop, we offered that training virtually and in-person through 2024. We were so inspired by the engagement with our work that we have developed project training resources for more of your favorite Center projects.
Our Defending Operational Technology (OT) with ATT&CK project was inspired by the observation that adversaries who target OT systems avail themselves of techniques on IT systems. We developed a methodology to model threats to a hybrid IT/OT environment that includes multiple domains and provides a customizable and repeatable framework for analyzing and building threat collections. Furthermore, we developed a reference architecture to visualize the technologies in an IT/OT environment so that defenders can determine the attack surface where a threat actor can generate a cyber effect.
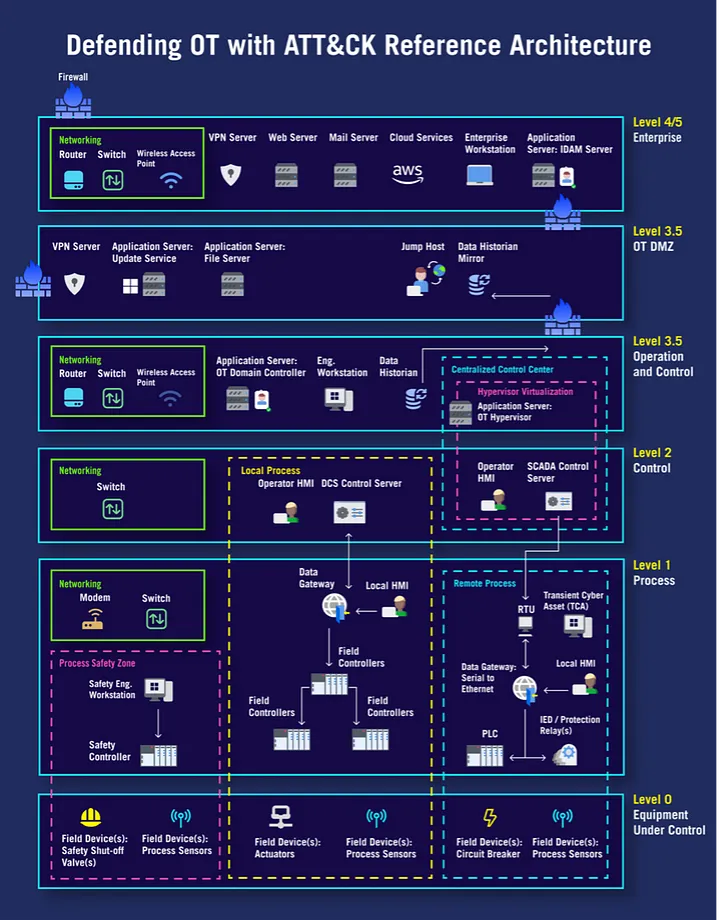
And to demonstrate the threat, we built a custom collection of threats based on a compilation of real-world adversary behaviors associated with the 20 architectural assets outlined in the reference architecture. This process resulted in a comprehensive threat collection comprising 251 techniques and 441 sub-techniques.
With these resources we developed an ATT&CK-based Cyber Tabletop Exercise to discuss a real-world example and understand the best defensive capabilities to counter those threats. We selected the 2022 Ukraine Electric Power attack by Sandworm, because the campaign utilized a mix of techniques from ATT&CK for Enterprise and ICS to infiltrate a Ukrainian electric utility and send unauthorized commands from their SCADA system. Please run this exercise with us by contacting the Center here.

Threat-informed defense is a team sport, and the Center’s Threat Modeling with ATT&CK project brings the security architects and threat modelers onto the field with security operators and threat intelligence. We observed that there is a lack of guidance on how to best utilize existing tools and data with ATT&CK to improve existing threat modeling methodologies. This project applied the Four Questions Framework and integrates ATT&CK into existing threat modeling methodologies like Attack Trees. Apply this process to identify critical assets, assess threats, measure existing defensive capabilities, and recommend threat and defense informed mitigations.
Organizations of any size or maturity level can use this process to model threats to their own assets using their existing tools and CTI data. Even with this process published and available for all, there remains a need to introduce threat modelers and security operators to this common language. We offer a guided beta test integrating Threat Modeling with ATT&CK into your threat modeling practice.
Teams that are planning to conduct threat modeling exercises should join this beta. Your team will identify the most likely techniques adversaries will use, evaluate these techniques against your existing defensive capabilities, and recommend security investments in areas of residual risk. Your team will apply the step-by-step threat modeling guidance provided on the Threat Modeling with ATT&CK website to a real threat modeling task in your organization. This is an opportunity to integrate ATT&CK into your threat modeling process. Contacting the Center here to participate.
Our Secure AI project had a featured role at the Asia-Pacific FIRST conference in 2024, where workshop participants learned how to navigate the ATLAS matrix and case studies and created a new case study and incident report using the new incident page launched through the Secure AI project.
The workshop participants represented 17 organizations from 15 countries and all were familiar with MITRE ATT&CK. For most it was their first hands-on experience with the unique adversarial attacks that have been leveraged against AI systems in real-world incidents and realistic red-teaming demonstrations. Join the AI-incident sharing program here.
In March 2024, the Center undertook the ambitious effort to Measure, Maximize, and Mature Threat-Informed Defense (M3TID). M3TID created an actionable definition of threat-informed defense and its associated key activities, and a formalized approach to measure your threat-informed defense. This maturity model complements existing cybersecurity maturity models by incorporating a measure of how well threat information is leveraged. M3TID gives organizations the ability to measure the current state of their defense, to identify and prioritize areas to advance, and a repeatable method to track their progress.
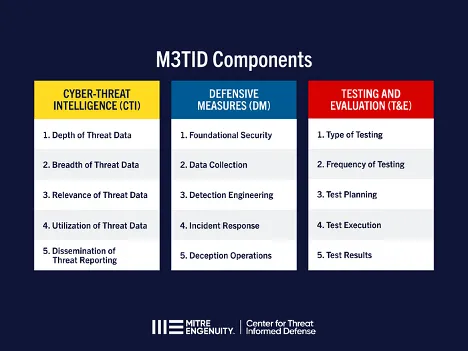
In 2025, the Center will deliver a survey for organizations to calibrate their posture. Completing the survey will generate actionable recommendations as to how to improve. In addition, the Center will debut training for defenders at the March 2025 APAC ATT&CK Community Workshop in Singapore. This training will cover topics in each component area, leading to a holistic advancement of threat-informed defense in your enterprise.

Threat-informed defense changes the game on the adversary, and it will always be a team sport. We are grateful for your feedback on the products of our research, on how you use Center resources, and the content of our trainings, workshops, and other engagements. We aim to create widely used, easily accessible, and practical resources through our R&D program. That is only possible with community support and engaged Center Participants. Your feedback is key to evolving our work and maximizing its impact. Your hard problems and ideas inform our R&D program.
Please read the rest of our 2024 R&D Roadmap Update
Stay informed — Be the first to know about R&D project releases by signing up for our newsletter and following us on LinkedIn.
Use Center R&D and share your feedback — Using our work to advance threat-informed defense in your organization goes a long way to ultimately changing the game on the adversary. Letting us know how you are using Center R&D allows us to continually refine our work, making it more accessible and impactful.
Join us to advance Threat-Informed Defense — Our Participants are thought leaders with sophisticated security teams that are advanced practitioners of threat-informed defense and users of ATT&CK. With the understanding that the cyber challenges we face are bigger than ourselves, our members join the Center prepared to tackle hard problems in a uniquely collaborative environment. If this sounds like your organization, learn more here about how to become a Center Participant.
© 2024 The MITRE Corporation. Approved for Public Release. ALL RIGHTS RESERVED. Document number
CT0132.
Threats to cloud computing span multiple security domains, objectives, and layers of technology. Defenders must protect dynamic, shared …
INFORM builds on M3TID to translate threat intelligence, defensive measures, and test & evaluation into a measurable, repeatable practice. …
Threat-informed defenders can use ATT&CK Sync and the enhanced Mappings Editor to keep ATT&CK-based tools and mappings current with major …