Cloud Security Built with ATT&CK
Threats to cloud computing span multiple security domains, objectives, and layers of technology. Defenders must protect dynamic, shared …
By Adrian Garcia Gonzalez and Tiffany Bergeron • August 14, 2024

Critical infrastructure such as electrical generation facilities, water treatment plants, and transportation systems are a lifeline for our communities. Unfortunately, this dependence has made critical infrastructure a prime target for threat actors. Furthermore, these systems often lack security measures we see in enterprise networks, making them easier to attack. By identifying the threat landscape and communicating adversary behaviors affecting information technology (IT) and operational technology (OT) systems, organizations can evaluate and employ security controls for real-world adversary behaviors targeting those environments.
In collaboration with AttackIQ, Booz Allen Hamilton, Ensign InfoSecurity, Global Cyber Alliance and Siemens, the Center for Threat-Informed Defense created Defending OT with ATT&CK to identify and defend against adversarial techniques that impact operations on critical infrastructure. We created three resources to identify assets and technologies in complex IT/OT environments and present an approach to comprehensively identify adversarial behaviors targeting those systems.
This information is essential to implement defensive measures against the techniques that adversaries use against critical infrastructure.
To ensure a thorough analysis and documentation of potential adversarial techniques, this research project developed a methodology to model threats to a hybrid IT/OT environment that includes multiple domains and provides a customizable and repeatable framework for analyzing and building threat collections. The methodology expands the Center’s Defending IaaS with ATT&CK approach by presenting a comprehensive view of adversary behavior that could impact overall operations within a hybrid IT/OT environment.
For Defending OT with ATT&CK, we applied this methodology to identify the assets that constitute the attack surface of a hybrid IT/OT environment. From these assets we developed the reference architecture. We then established selection criteria to assess the threats posed by each one of these technologies based on relevant factors, such as operating system risks or industrial control system (ICS) processes affected.
Step 1. Identify Attack Surface
Identify security boundaries and understand the technologies that form their architecture.
Step 2. Compile Sources
Generate a comprehensive picture of adversarial risks; it is necessary to include CTI sources for the listed assets.
Step 3. Define Selection Criteria
Identify which adversarial risks apply to your scenario and asset and omit irrelevant sources.
Step 4. Select Techniques
Review and evaluate adversarial techniques for each asset to curate the final collection.
Step 5. Build Collection
Assemble the techniques into a custom threat collection to share throughout your organization.
To determine the attack surface where a threat actor can generate a cyber effect, we developed a reference architecture that aligns with the Purdue Model to visualize the technologies within a IT/OT environment. In defining architectural assets, we considered several factors to ensure comprehensive coverage of risks.
This reference architecture provides a common, reusable view of assets and technologies used in IT/OT environments where a threat actor can impact operations. It serves as a framework for depicting assets through functional components across the technology stack of an OT environment in hierarchical levels. All assets depicted in the architecture were mapped to ATT&CK for Enterprise’s platforms or ATT&CK for ICS’ assets, with nine hybrid assets overlapping techniques from multiple domains of ATT&CK. The architecture aids in evaluating security boundaries between different operational zones and assessing plausible attack vectors between IT and OT assets.
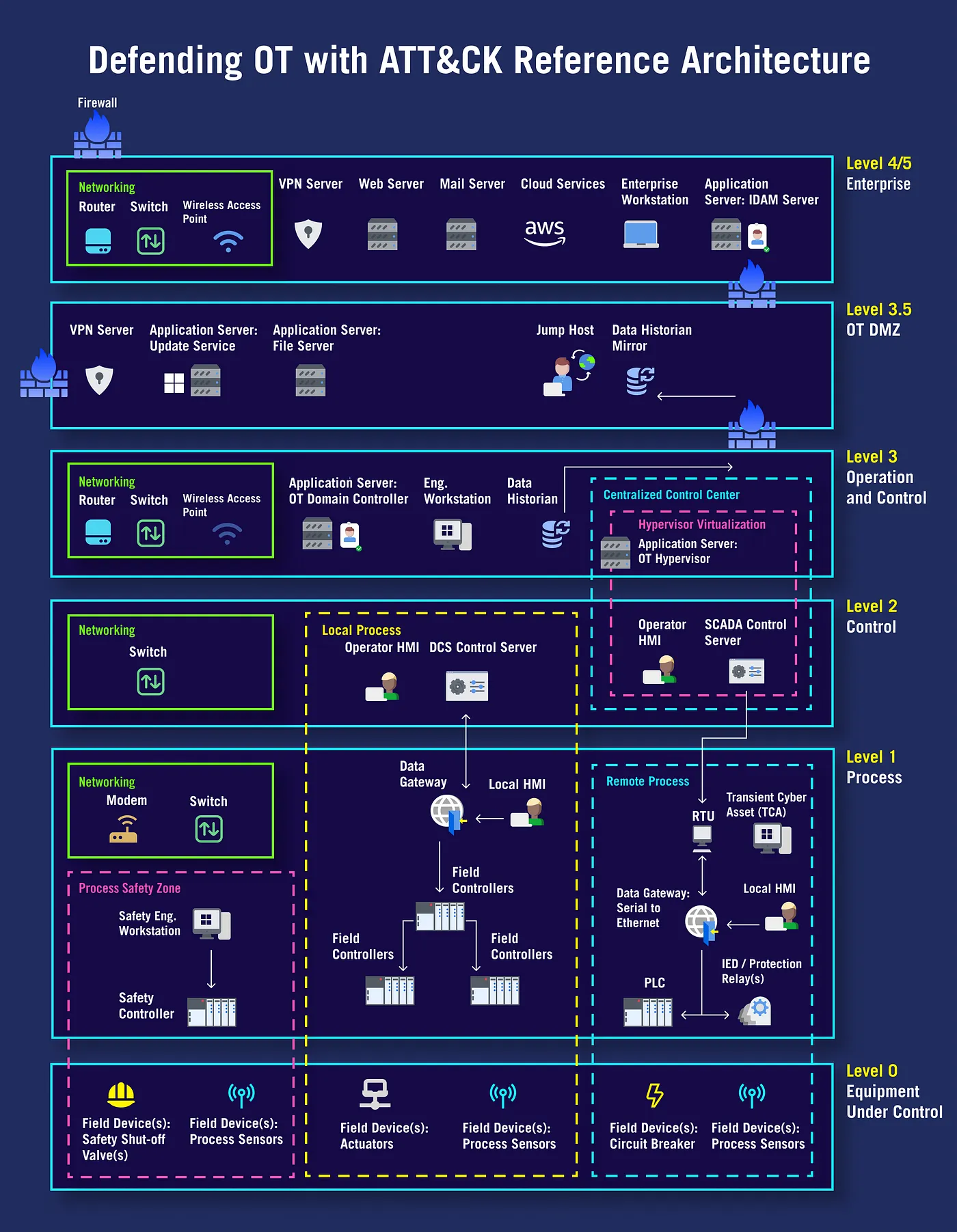
The Defending OT with ATT&CK threat collection is a set of ATT&CK techniques tailored to the attack surface and threat model for OT environments. To identify and define this multi-domain collection, we analyzed adversarial tactics, techniques, and procedures (TTPs) as contained in ATT&CK for Enterprise, ATT&CK for ICS, and other relevant ATT&CK datasets such as Cloud and Containers. The threat collection is designed to evaluate, plan, and employ mitigating security controls for adversarial techniques within an IT/OT architecture.
We utilized the Center’s ATT&CK Workbench to build a custom collection of threats based on a compilation of real-world adversary behaviors documented in ATT&CK v15. ATT&CK Workbench provides the flexibility and customization needed to identify specific adversarial risks associated with the 20 architectural assets outlined in the reference architecture. This process resulted in a comprehensive threat collection comprising 251 techniques and 441 sub-techniques. ATT&CK Workbench streamlined the analysis of threats and facilitated the communication of various risks for each asset. Additionally, we created a custom threat collection that can be exported and shared as a STIX bundle.
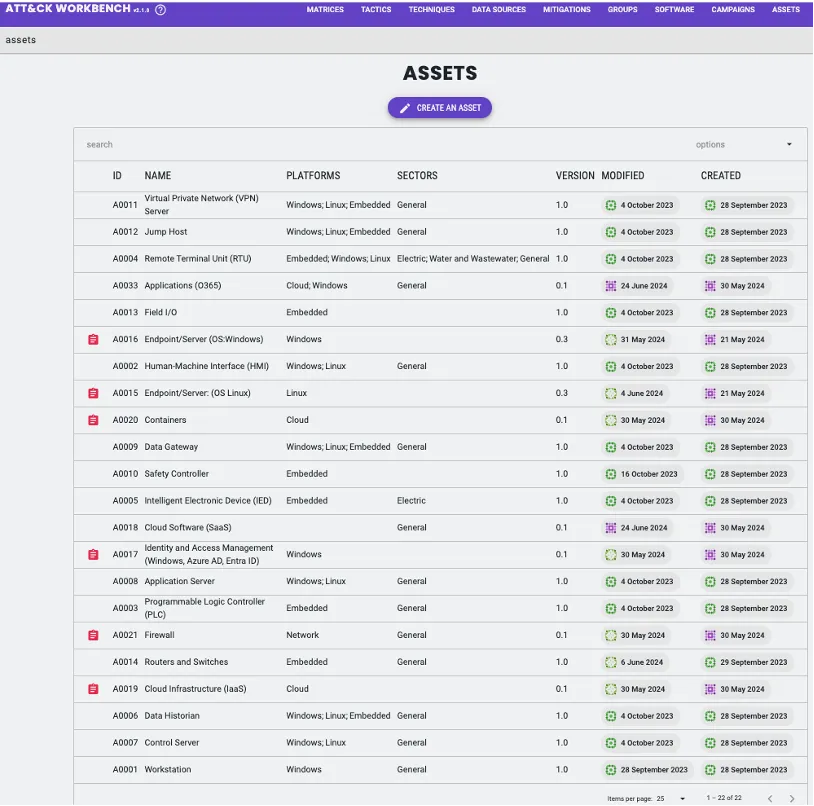
Organizations looking to tailor research for specific needs can view the collection of techniques using the latest version of ATT&CK Workbench. These resources offer a template for organizations looking to extend our approach for their intended use cases, including:
There are several ways that you can get involved with this project and help advance threat-informed defense. Please review the project resources, use them, and tell us what you think.
We welcome your contributions to help advance Defending OT with ATT&CK in the form of pull requests; please review the contributor notice before making a pull request.
For any technical questions or requests, please submit issues on GitHub . You may also contact ctid@mitre.org directly for more general inquiries about the Center for Threat-Informed Defense.
© 2024 The MITRE Corporation. Approved for Public Release. ALL RIGHTS RESERVED. Document number
CT0121.
Threats to cloud computing span multiple security domains, objectives, and layers of technology. Defenders must protect dynamic, shared …
INFORM builds on M3TID to translate threat intelligence, defensive measures, and test & evaluation into a measurable, repeatable practice. …
Threat-informed defenders can use ATT&CK Sync and the enhanced Mappings Editor to keep ATT&CK-based tools and mappings current with major …