Threat-Informed Defense for Cloud Security
Use our latest mappings to replace assumption-driven cloud defense with evidence-based decisions to stop cloud adversaries in their tracks. With …
August 15, 2024
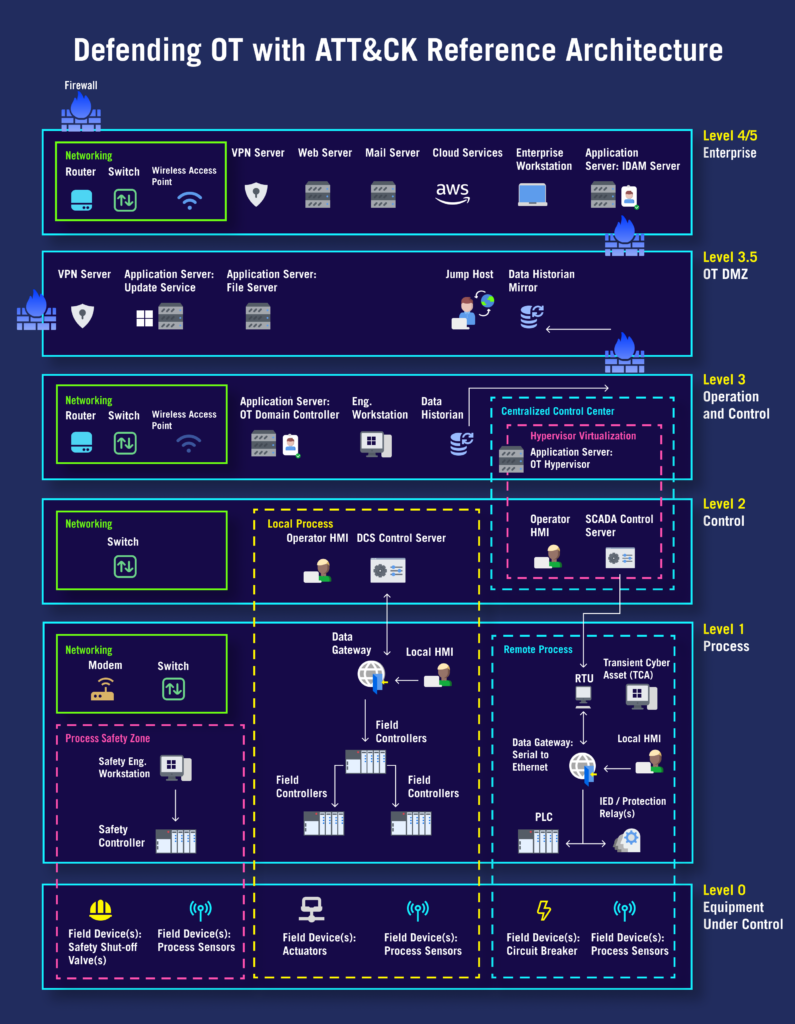
Defending Operational Technology (OT) with ATT&CK provides a customized collection of MITRE ATT&CK® techniques tailored to the attack surface and threat model for OT environments. Historical attacks against OT and adversarial techniques contained in ATT&CK for Enterprise, ATT&CK for ICS, and other relevant ATT&CK platforms were analyzed to identify and define a reference architecture and threat collection of techniques adversaries could use within an IT/OT hybrid architecture. The resultant resources can be used by organizations that use OT to evaluate and employ security controls for real-world adversary behaviors targeting those environments.

Organizations need to understand the techniques adversaries use against OT and the enterprise systems that manage OT.

Develop a straightforward approach to understanding and working with the techniques applicable to OT.

Organizations defend against the full set of techniques against OT.






Use our latest mappings to replace assumption-driven cloud defense with evidence-based decisions to stop cloud adversaries in their tracks. With …
MITRE INFORM is a program-level assessment designed to show how threat-informed your organization is and where to improve next across cyber …
With Attack Flow, you will capture the entire attack and communicate what matters!
Sign up for our "Stay Informed" mailing list to receive announcements for project publications, upcoming events, and other news about the Center.