Cloud Security Built with ATT&CK
Threats to cloud computing span multiple security domains, objectives, and layers of technology. Defenders must protect dynamic, shared …
By Mike Cunningham and Val Valenzuela • January 8, 2026
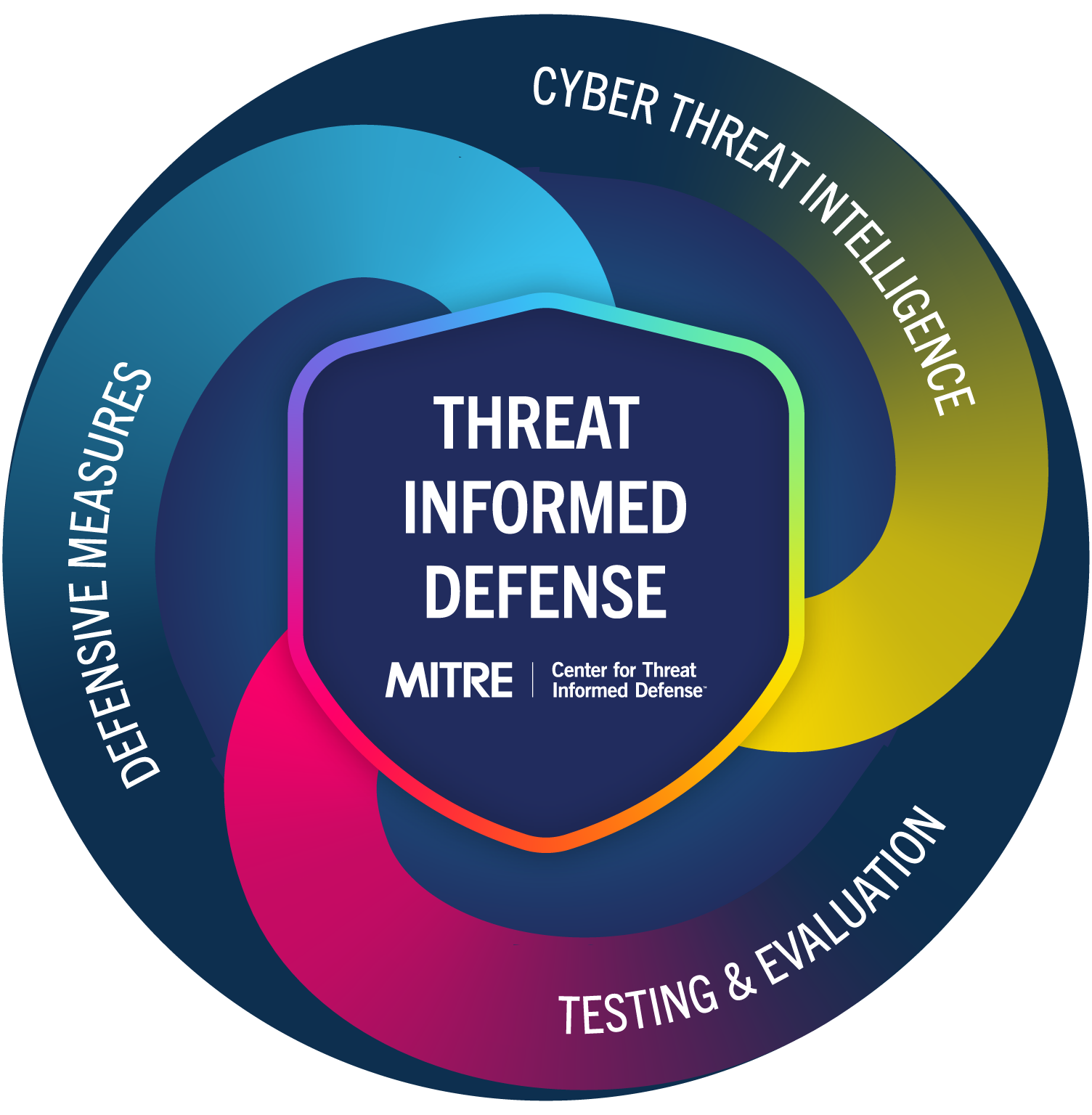
Threat-informed defense only works when adversary knowledge shapes decisions across the entire security program. Many organizations have adopted ATT&CK-based practices, invested in cyber threat intelligence, and expanded their testing and evaluation. The challenge lies in addressing two remaining questions: how well-informed is your defense about current threats today, and how can you improve it?
To answer those questions, MITRE CTID evolved its original M3TID research into INFORM, a practical, measurable approach for assessing and maturing threat-informed defense at the strategic level. We built INFORM with CTID members AttackIQ, Fortinet, HCA Healthcare, Infineon, and Lloyds Banking Group. Their expertise kept us anchored to what teams need to operate threat-informed programs at scale.
Two years ago, we created Measure, Maximize, Mature Threat-Informed Defense (M3TID) to help teams determine whether their defense was truly threat-informed. M3TID defined threat-informed defense as a continuous loop across three dimensions:
M3TID gave teams a way to assess maturity and identify gaps, delivered via the tried-and-true method of an Excel spreadsheet. Over time, practitioner feedback and real-world use showed us where we had gaps of our own. We needed to align M3TID with strategic operations, replace the spreadsheet with a professional UI, and make it more actionable for program leaders. Threat-informed defense works best when it is a program-wide practice instead of a set of disconnected initiatives, so we set out to accurately capture that.
INFORM retains the core intent of M3TID and sharpens it to address how organizations operate today. INFORM improves upon our original model in the following ways:
M3TID defined the three dimensions of TID (CTI, DM, and T&E) with each dimension containing five components and 25 levels. Our original scoring algorithm weighed each of the components and levels evenly. While this was good for a first effort, it ignored the larger significance that some security decisions can have over others. For instance, tracking IOCs is not as significant as tracking adversary behaviors because IOCs are often temporary and reactive, while adversary behaviors provide deeper insights into tactics, techniques, and procedures that are more consistent and predictive of future attacks. To account for this, we assigned points to each level based on its significance relative to its dimension.
We also examined our component list and noticed that while our dimensions had different weights (CTI at 35%, DM at 40%, and T&E at 25%), components were evenly distributed. This was incongruous, so we dug into each dimension to see if we were accurately capturing the important aspects of them. Our research identified several gaps so we expanded the dimensions, which neatly coincides with the dimension weights.

Another piece of feedback we received on M3TID was that the levels do not represent the speed at which operational information needs to move across an organization. This requires accounting for speed of dissemination, as well as an organization’s ability to work across teams. We created new levels to reflect this reality. As programs mature, progress increasingly depends on quick cooperation across threat intelligence, engineering, operations, and leadership. This shifts maturity from “one team improved” to “the program improved,” which reflects how threat-informed defense succeeds.
INFORM is strategic. It provides a program-level view and complements tactical models that focus on specific teams and functions. For example, capability maturity models such as CTI-CMM, SOC-CMM, and Red Team-CMM typically operate at the tactical level, driving depth within a function. INFORM operates at the strategic level, helping leaders understand whether the overall program consistently applies threat-informed defense and where coordinated investment will improve outcomes.
INFORM also fits naturally alongside Continuous Threat Exposure Management (CTEM) programs. CTEM weaves threat-informed thinking throughout its five-step cycle. Both CTEM and INFORM provide a way to measure whether threat-informed defense is consistently applied across a program, and how it changes over time. Threat-informed defense should span the entire program and INFORM is designed to help teams make that measurable.
INFORM is delivered through a user-friendly web tool located at ctid.mitre.org/inform. The assessment is designed for repeated use that allows you to:
Users can upload up to four past results to see trends over time, and more specifically, how program-wide decisions affect threat-informed defense. Teams can revisit past results as their environment, threats, and capabilities evolve.

Teams often know they want to be more threat-informed, but they struggle to choose which actions will deliver real value quickly. INFORM addresses that with recommendations driven by an impact vs. complexity model.
Each level in INFORM is scored on:
The tool represents these scores in a matrix that is personalized based on the user’s inputs. This matrix helps teams prioritize work that will deliver high value with manageable effort and supports longer-term planning for high-impact changes that require more coordination.

Start by running the assessment and sharing the PDF summary with stakeholders. Then pick one or two high-impact, low-complexity improvements to pilot. Reassess after each cycle to show progress and maintain alignment across CTI, defensive measures, and test and evaluation.
Threat-informed defense is not a one-time project. It is a continuous cycle of understanding threats, improving defenses, and validating results. INFORM provides a practical way to measure that cycle and mature it across the entire program.
© 2026 The MITRE Corporation. Approved for Public Release. ALL RIGHTS RESERVED. Document number
PR_25-02691-3.
Threats to cloud computing span multiple security domains, objectives, and layers of technology. Defenders must protect dynamic, shared …
INFORM builds on M3TID to translate threat intelligence, defensive measures, and test & evaluation into a measurable, repeatable practice. …
Threat-informed defenders can use ATT&CK Sync and the enhanced Mappings Editor to keep ATT&CK-based tools and mappings current with major …