Cloud Security Built with ATT&CK
Threats to cloud computing span multiple security domains, objectives, and layers of technology. Defenders must protect dynamic, shared …
By Mark Haase, Mike Carenzo, Mike Cunningham and Suneel Sundar • July 8, 2025

From large multinationals with mature cybersecurity programs to small startups, organizations around the globe use Attack Flow to track the APTs that are tracking them. Excitement and adoption of Attack Flow has been growing as evident by the numerous presentations given at security conferences around the world, including Blackhat and FIRSTCON. Users embrace Attack Flow in a variety of job roles, from CTI to cyber defense to red teaming.
MITRE’s Center for Threat-Informed Defense (CTID) has updated Attack Flow in collaboration with our participants AttackIQ, Inc., Citigroup, Fortinet, HCA Healthcare, JPMorgan Chase Bank, N.A., National Australia Bank, and non-profit Cyber Threat Alliance. This release improves how you build, share, and present flows; it also offers new visualization tools that save time and generate insights. This update includes highly requested features, an improved look-and-feel, and expanded training and documentation. We have more features than we can fit into this blog, so follow us on LinkedIn where we will break down all the new features in a series of posts.
A central objective of this Attack Flow release is to improve the visualization of flows. Starting with any flow that you have built, you can now transform it into myriad of different visualizations. The alternative ways of looking at your flow data can save time and effort as well as generate insights into cyber attacks.
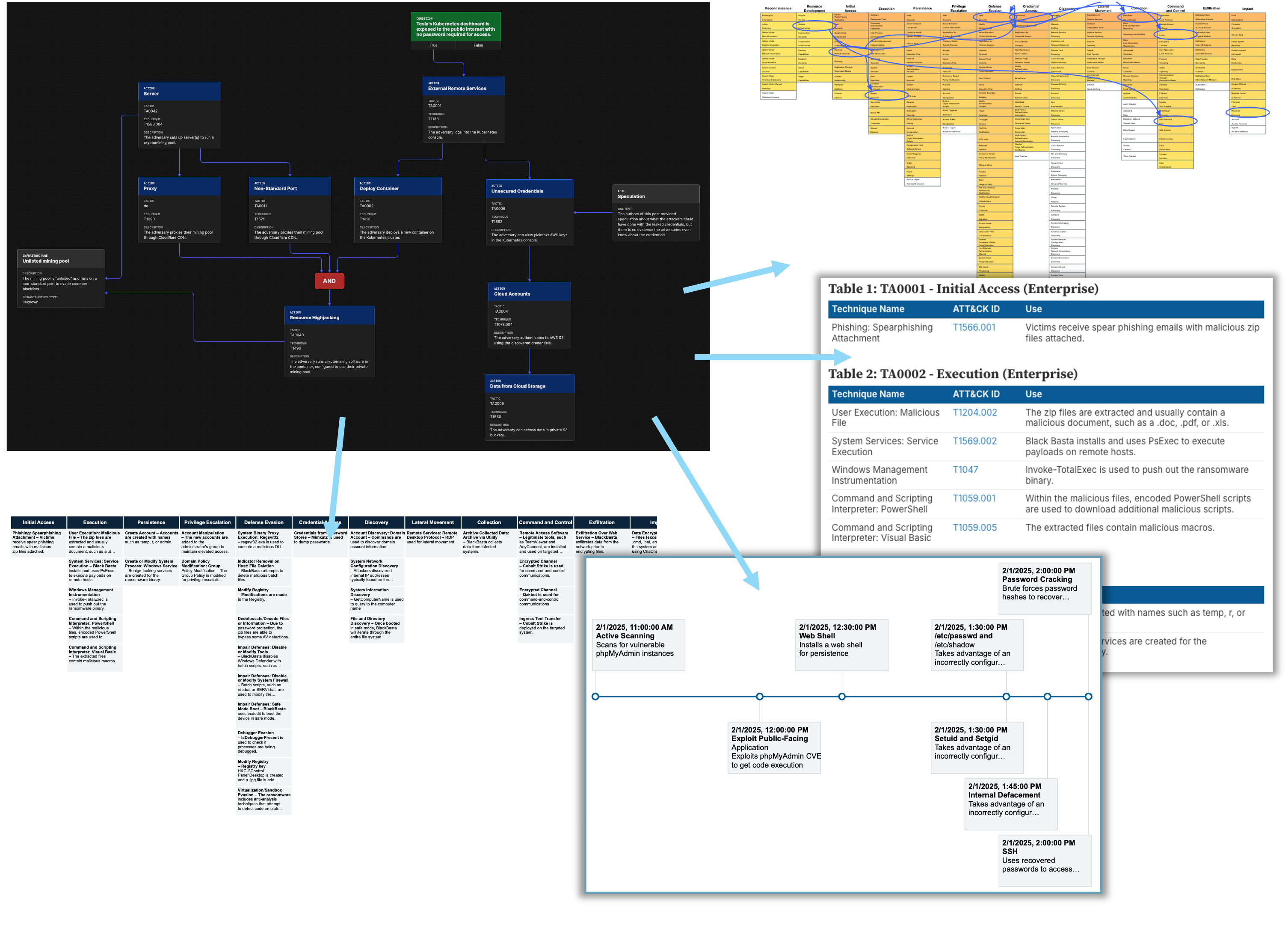
For example, it’s simple to generate an ATT&CK matrix from your flow. Download the Black Basta Ransomware JSON from our Example Flows, and then generate an ATT&CK matrix view by uploading the JSON into the Matrix View tool.
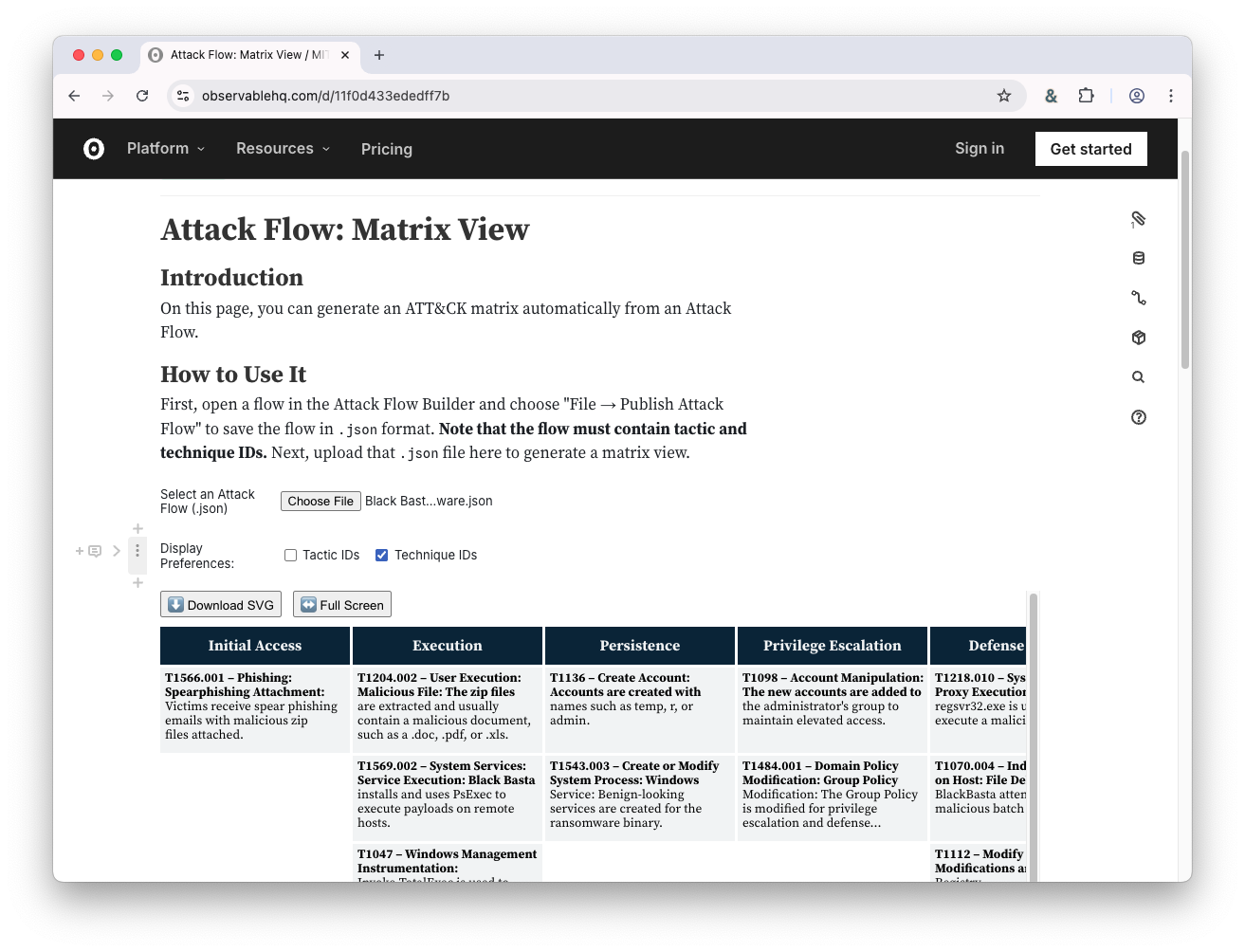
When you’re done, you can export the graphic to a high-quality image format to put into a report or presentation. Click here to see an example.
In the past, we saw CTI reporting with embedded screenshots of flows, but the screenshots were large and unwieldy. As part of our push to make it easier for users of Attack Flow to share their flows with the public, we built a way to embed interactive flows into a webpage.
Give it a try with the flow below by zooming and scrolling around to explore.
Anybody can embed an interactive flow into their web page that can be panned and zoomed. This new feature makes it easier to share flows in your CTI reporting.
To improve efficiency, we have added a feature that lets you copy items from one flow and paste them into another flow. You can also paste the selection as an image into common applications such as Word and PowerPoint, which is a great way to quickly build reports and presentations. Another highly requested feature is the ability to select multiple elements at once, which you can now do by holding down the Alt/Option key as you drag a selection rectangle.
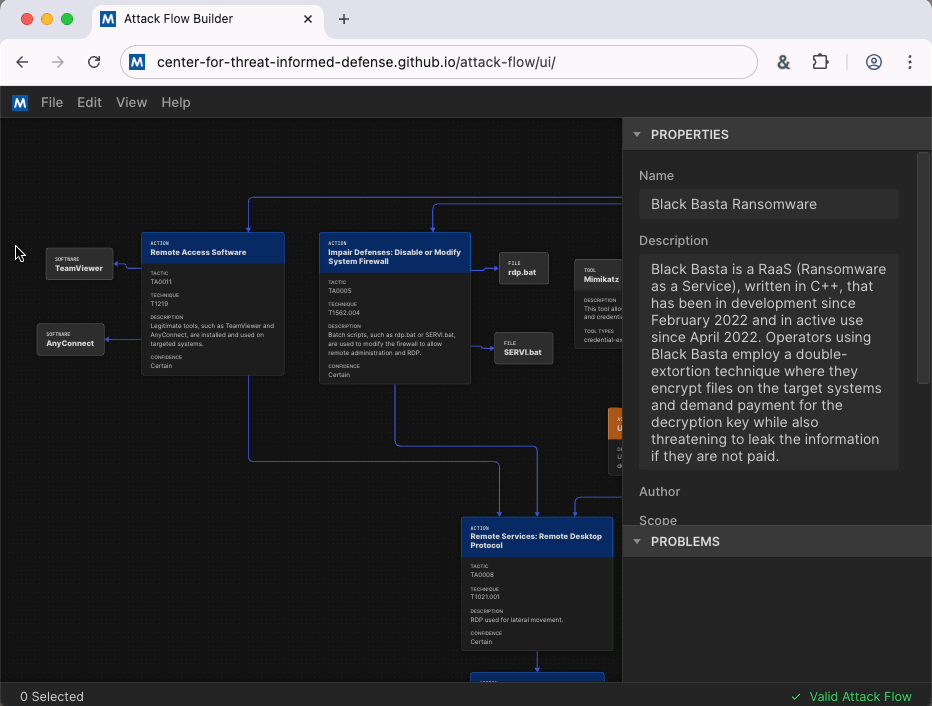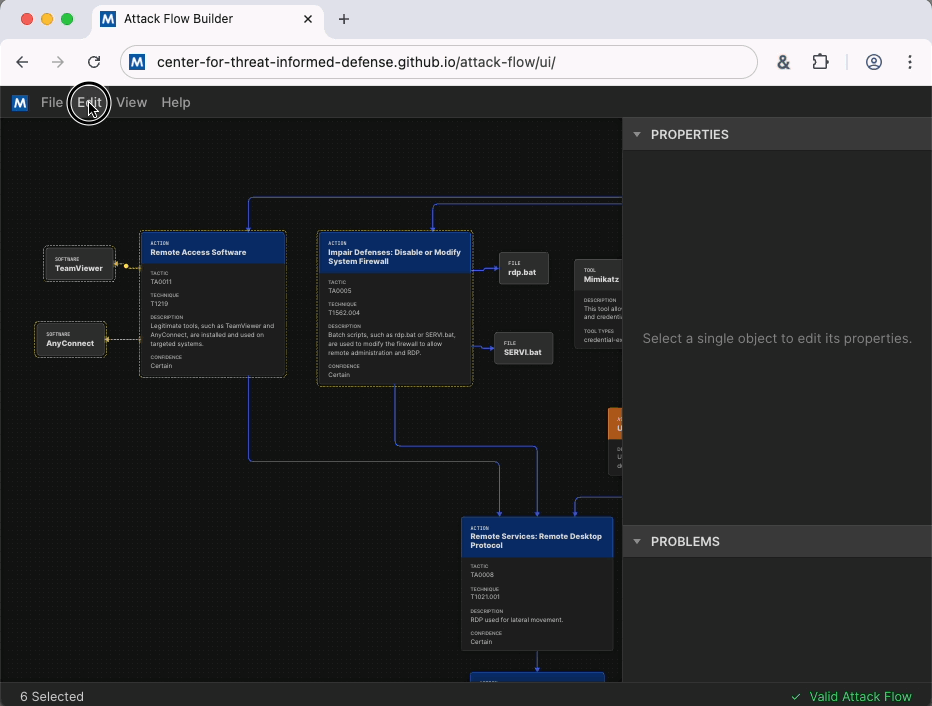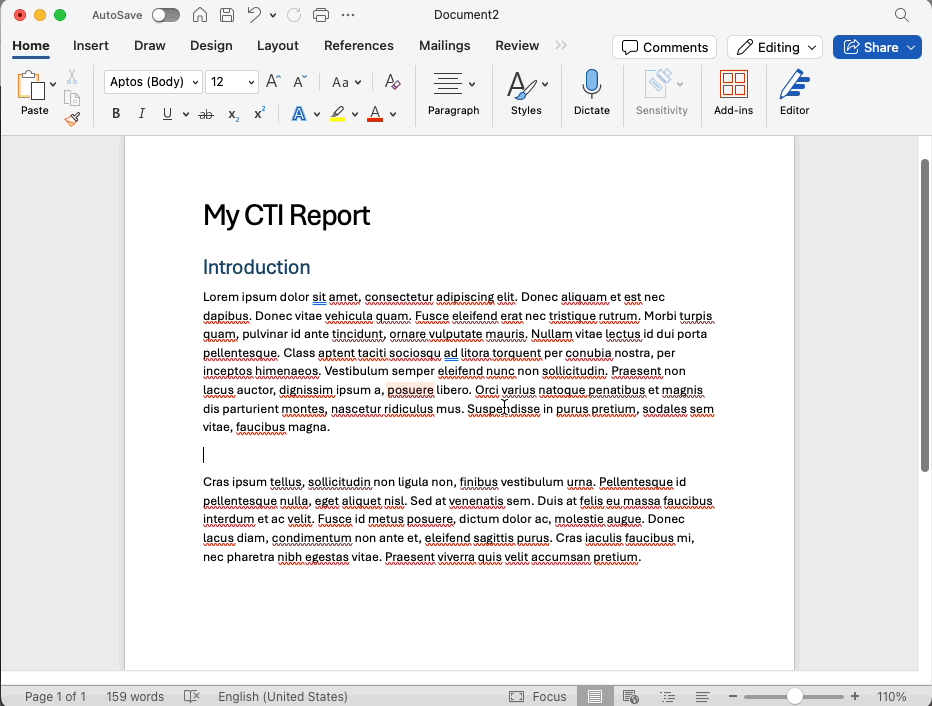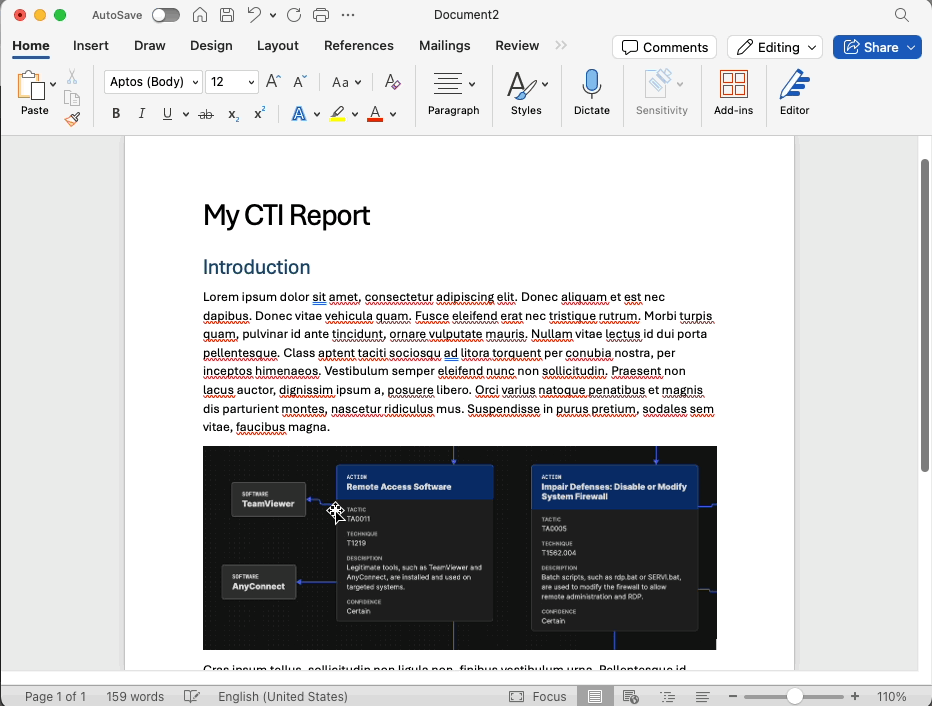
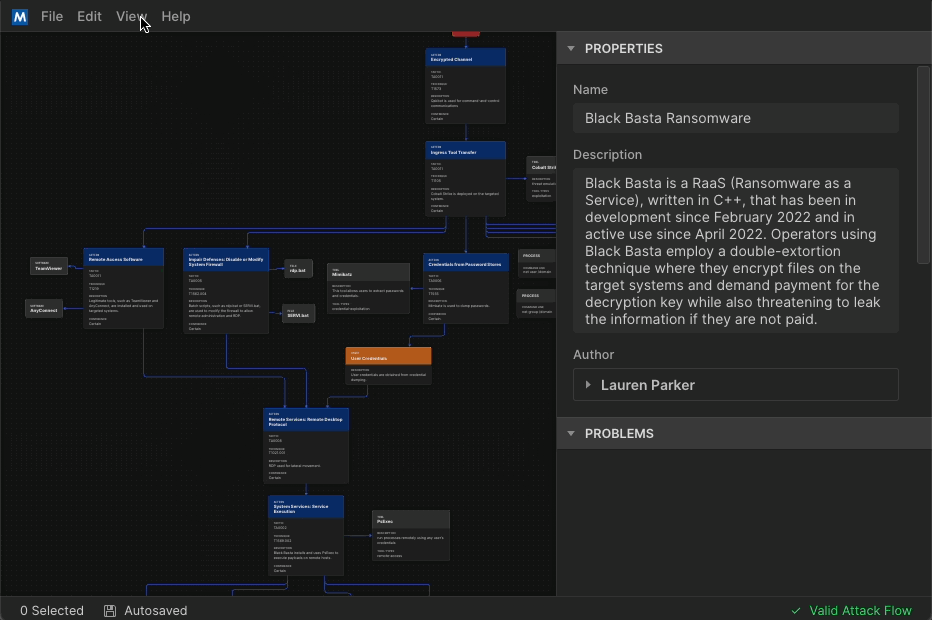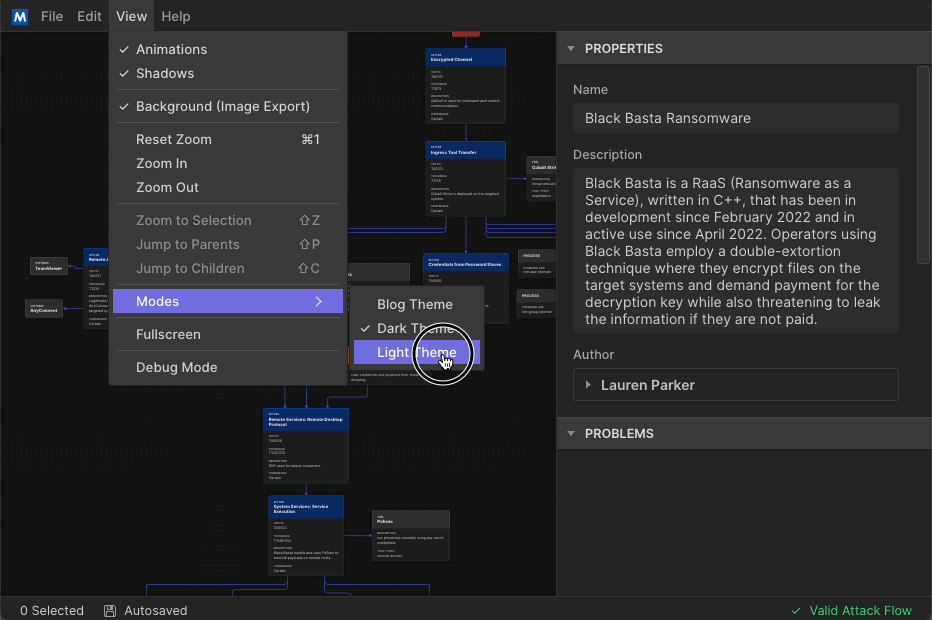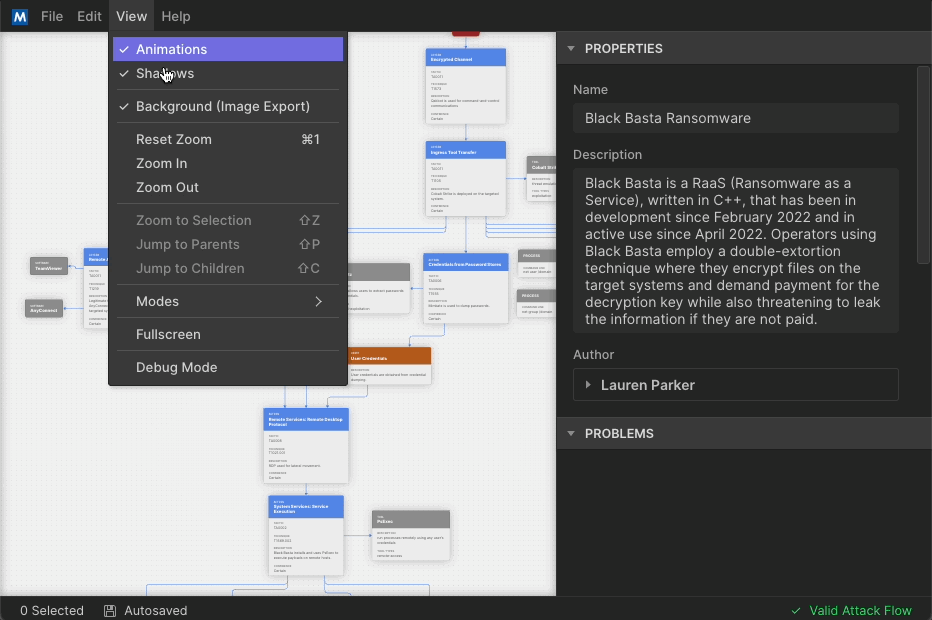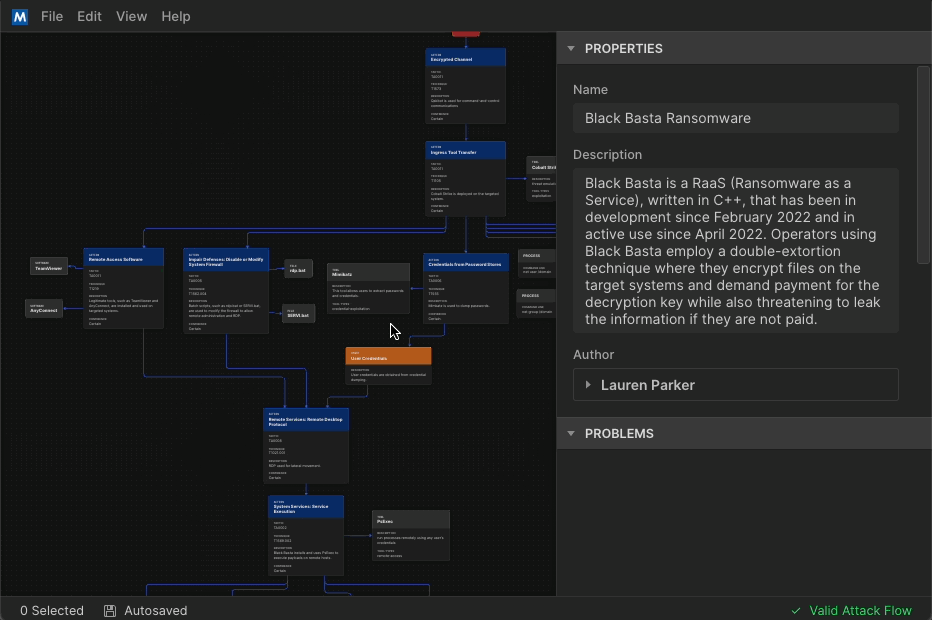
As a visual improvement, we now offer both a “Light Mode” and “Dark Mode.” When copy or save graphics from Attack Flow, they appear in your chosen mode. Light mode is a great option for building professional deliverables using snippets from your flow for your management team or customers.
Learn more about all of the new visualization options on our Visualization page.
With our Research Participants, we envision that Attack Flow will become an industry-wide tool for threat-informed visualization and sharing. To get there, we developed new usage guides that explain how to apply Attack Flow to specific job roles such as Incident Responder or Red Teamer. We are also hosting Attack Flow training sessions this summer.
If you work for a CTID member organization, reach out to your point of contact for more information. If you are not yet a CTID member and would like to request training in person or virtually, please contact us.
Later this month, we will release a set of open-source trainings in video and PowerPoint formats. The video format is ideal for self-study, while the PowerPoint slides are for Attack Flow power users who want to host their own training events.
We welcome your feedback and contributions. There are several ways that you can get involved with Attack Flow and help advance threat-informed defense:
Please submit issues for any technical questions or contact us directly for general inquiries.
© 2025 The MITRE Corporation. Approved for Public Release. ALL RIGHTS RESERVED. Document number
25-2036.
Threats to cloud computing span multiple security domains, objectives, and layers of technology. Defenders must protect dynamic, shared …
INFORM builds on M3TID to translate threat intelligence, defensive measures, and test & evaluation into a measurable, repeatable practice. …
Threat-informed defenders can use ATT&CK Sync and the enhanced Mappings Editor to keep ATT&CK-based tools and mappings current with major …