Vizualize, Understand, and Share with Attack Flow 3
From large multinationals with mature cybersecurity programs to small startups, organizations around the globe use Attack Flow to track the APTs …
By James Ross • September 9, 2024

Describing adversarial behaviors in the form of tactics, techniques, and procedures (TTPs) using MITRE ATT&CK® revolutionized detection and response. Focusing on TTPs creates an opportunity for high-fidelity detection of adversaries. If we can detect a behavior, the adversary will need to change behaviors — increasing cost and risk for the adversary.
Detecting adversary behaviors is challenging. There are often many approaches to implementing a single behavior and adversaries commonly use native capabilities (living off the land), making it difficult to differentiate adversary activity from normal user activity.
Adversary TTPs occur in sequences. Understanding these sequences creates an opportunity to improve detection. If we know that Phishing is followed by Process Injection and then Hijack Execution Flow, we can begin looking for this pattern of TTPs. This sounds good in theory, but how does a defender know which behaviors are likely to have occurred together?
The Technique Inference Engine (TIE) uses a machine learning model trained on cyber threat intelligence to recommend likely TTPs based on a known input TTP. TIE will help analysts quickly understand what is likely to have happened next based on a broad corpus of threat intelligence. In collaboration with experts from Citigroup, Cyber Threat Alliance, Fortinet, Google Cloud, HCA Healthcare, IBM Security, Lloyds Banking Group, Tenable, and Verizon Business, we have built TIE to be a practical resource with immediate benefit for all security teams and designed it to easily enable further research and innovation.
Having the right dataset is critical to the predictive nature of the model. We identified four key attributes of our dataset to assure our model delivers relevant results.
Cyber threat intelligence (CTI) reports meet all the above criteria as they are crafted through expert analysis of cyber intrusions and observed adversary activity. By combining data used in previous Center research projects, CTI repositories, and contributions from our research partners we generated over 6,200 reports, covering 96% of the techniques in ATT&CK.
A common challenge among machine learning and threat-informed defense research is obtaining sufficient data to develop effective models. To support future research, we published our training data, which includes attributes such as campaigns, CTI references, and technique frequency to encourage researchers to build new models and discover novel associations.
Our recommender model uses a simple and powerful method to characterize each technique in the training data. This approach delivers technique predictions in a fraction of a second and is written in a way that is easily interpreted by security teams and machine learning experts alike. Advanced users can launch our code in a Jupyter notebook to adjust model parameters, retrain the model with a custom data set, and more.
Context is crucial in information fusion. Security teams require more than just a list of techniques to respond to incidents, emulate the adversary, or derive actionable threat intelligence. To make our predictions accessible to the broadest possible audience, we integrated TIE directly into your browser.
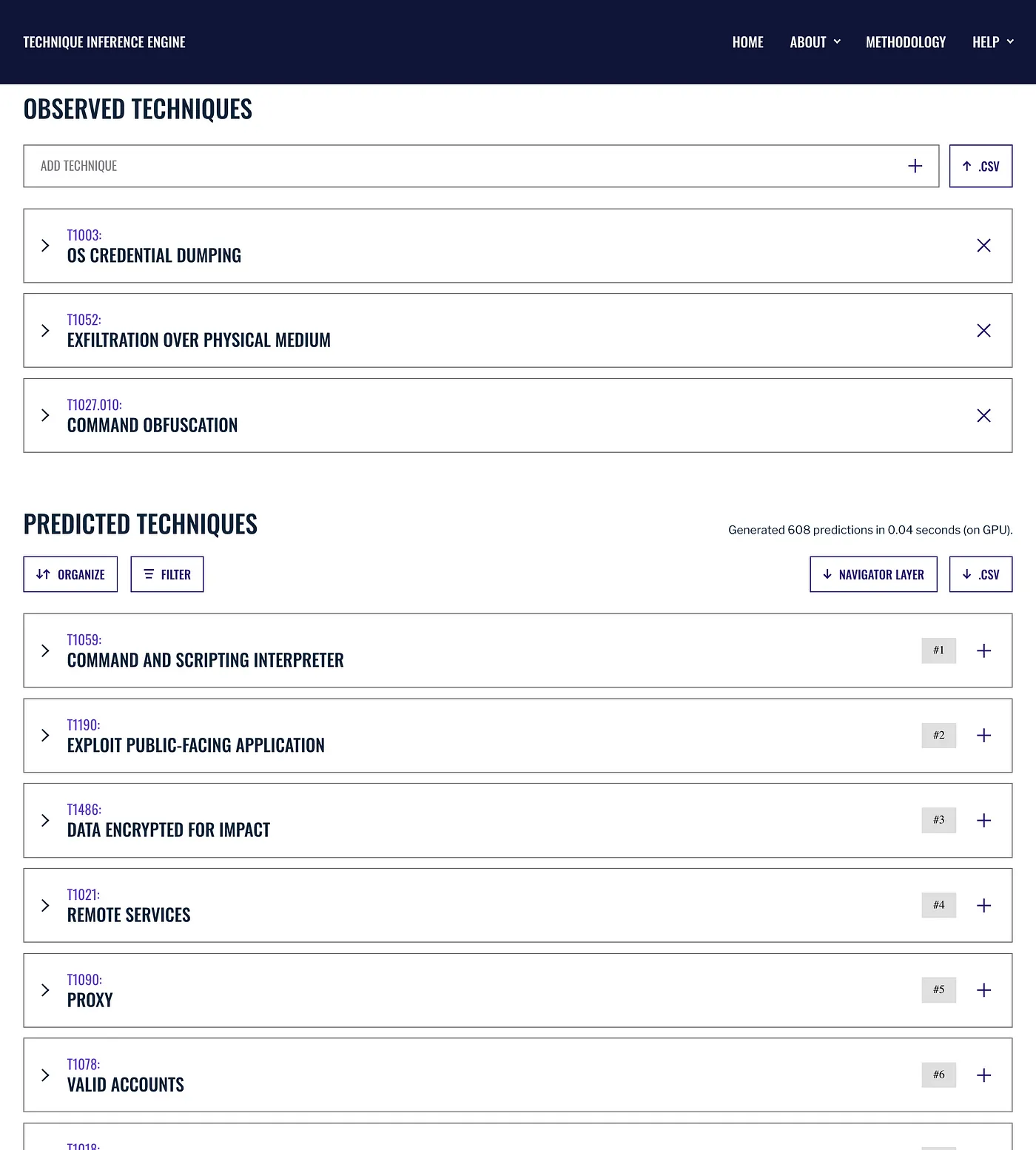
The web tool is the most accessible way to get a complete picture of the adversary. TIE uses on-device machine learning to predict related techniques — no information is sent over the network or stored. The predicted techniques can be organized by technique name, rank, or tactic. Filter results based on inference score, threat actor, campaign, or platform. Use TIE to visualize results through ATT&CK navigator to add emphasis via a heatmap or compare to other reports in a common format.
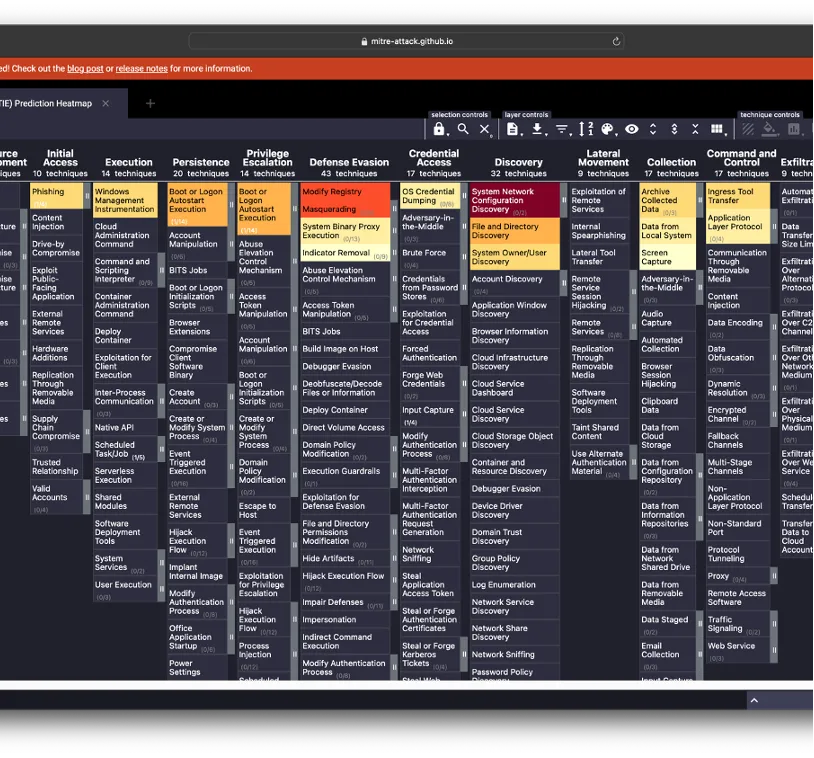
We’re delighted to provide the community with a tool that gives defenders a way to identify what you don’t detect. Our documentation walks through each step of our research and has examples of how TIE augments new lead generation for SOC teams, improves post-mortem incident analysis by filling in potential reporting gaps, and can create more comprehensive adversary emulation plans.
Building solutions that improve threat-informed defense is a community effort. Here are a few ways to stay involved:
Email us at ctid@mitre.org for more general inquiries.
© 2024 The MITRE Corporation. Approved for Public Release. ALL RIGHTS RESERVED. Document number CT0124.
From large multinationals with mature cybersecurity programs to small startups, organizations around the globe use Attack Flow to track the APTs …
The Cyber Risk Institute Profile is a distillation of the NIST Cybersecurity Framework tailored to address the financial services sector’s …
An ambiguous technique is a MITRE ATT&CK® technique whose observable characteristics are insufficient to determine intent. This means that …