Threat-Informed Defense for Cloud Security
Use our latest mappings to replace assumption-driven cloud defense with evidence-based decisions to stop cloud adversaries in their tracks. With …
September 9, 2024
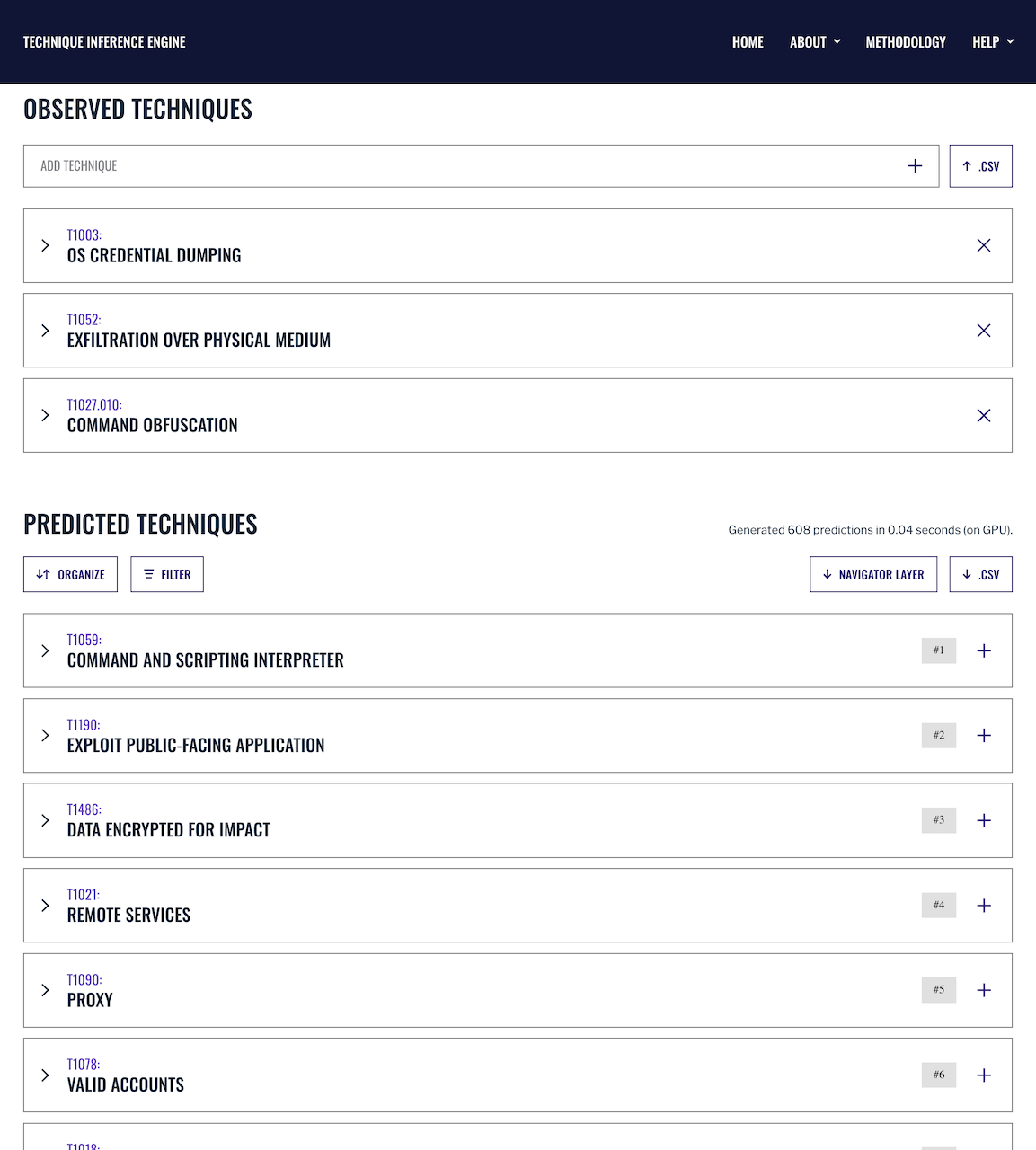
Know your adversary’s next move with the Technique Inference Engine, a machine learning-powered tool that infers unseen adversary techniques, providing security teams actionable intelligence.

Detections only find techniques for which we have an alert and fall short of guiding us to other likely-used techniques.

A model to infer an attacker’s other likely-used techniques, based on observed adversary operations.

Analysts identify more intrusion methods with fewer detections, and thus reduce mean time to respond.










Use our latest mappings to replace assumption-driven cloud defense with evidence-based decisions to stop cloud adversaries in their tracks. With …
MITRE INFORM is a program-level assessment designed to show how threat-informed your organization is and where to improve next across cyber …
With Attack Flow, you will capture the entire attack and communicate what matters!
Sign up for our "Stay Informed" mailing list to receive announcements for project publications, upcoming events, and other news about the Center.