Threat-Informed Defense for Cloud Security
Use our latest mappings to replace assumption-driven cloud defense with evidence-based decisions to stop cloud adversaries in their tracks. With …
December 10, 2023
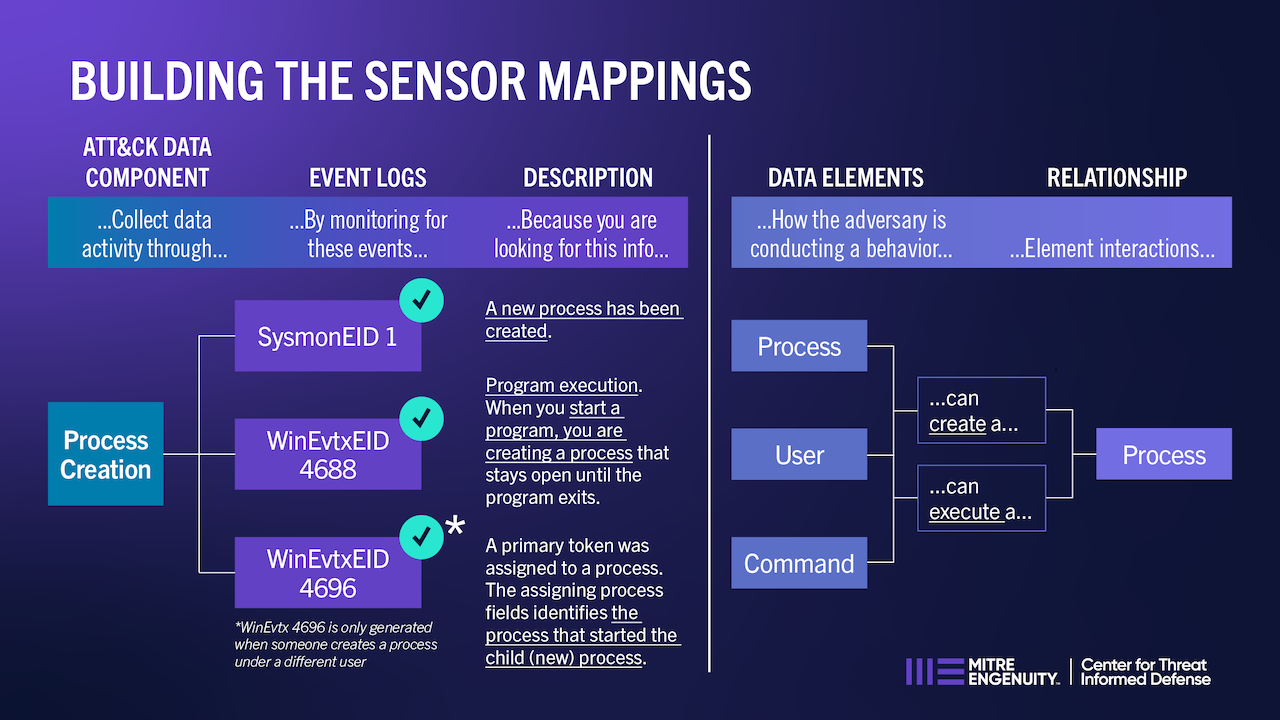
Sensor Mappings to ATT&CK gives cyber defenders the information they need to identify and understand cyber incidents occurring in their environment. Various tools and services are available to collect system or network information, but it is not always clear how to use those tools to provide visibility into specific threats and adversarial behaviors occurring in their environment. These mappings between sensor events and ATT&CK data sources allows cyber defenders to create a more detailed picture of cyber incidents, including the threat actor, technical behavior, telemetry collection, and impact.

Cyber defenders need to connect which tools, capabilities, and events detect specific adversary behaviors.

Link adversary behaviors to defenders’ tools, capabilities, and sensors through ATT&CK Data Sources.

Defenders collect and analyze the data necessary to observe adversary behaviors.












Use our latest mappings to replace assumption-driven cloud defense with evidence-based decisions to stop cloud adversaries in their tracks. With …
MITRE INFORM is a program-level assessment designed to show how threat-informed your organization is and where to improve next across cyber …
With Attack Flow, you will capture the entire attack and communicate what matters!
Sign up for our "Stay Informed" mailing list to receive announcements for project publications, upcoming events, and other news about the Center.