Threat-Informed Defense for Cloud Security
Use our latest mappings to replace assumption-driven cloud defense with evidence-based decisions to stop cloud adversaries in their tracks. With …
October 9, 2023
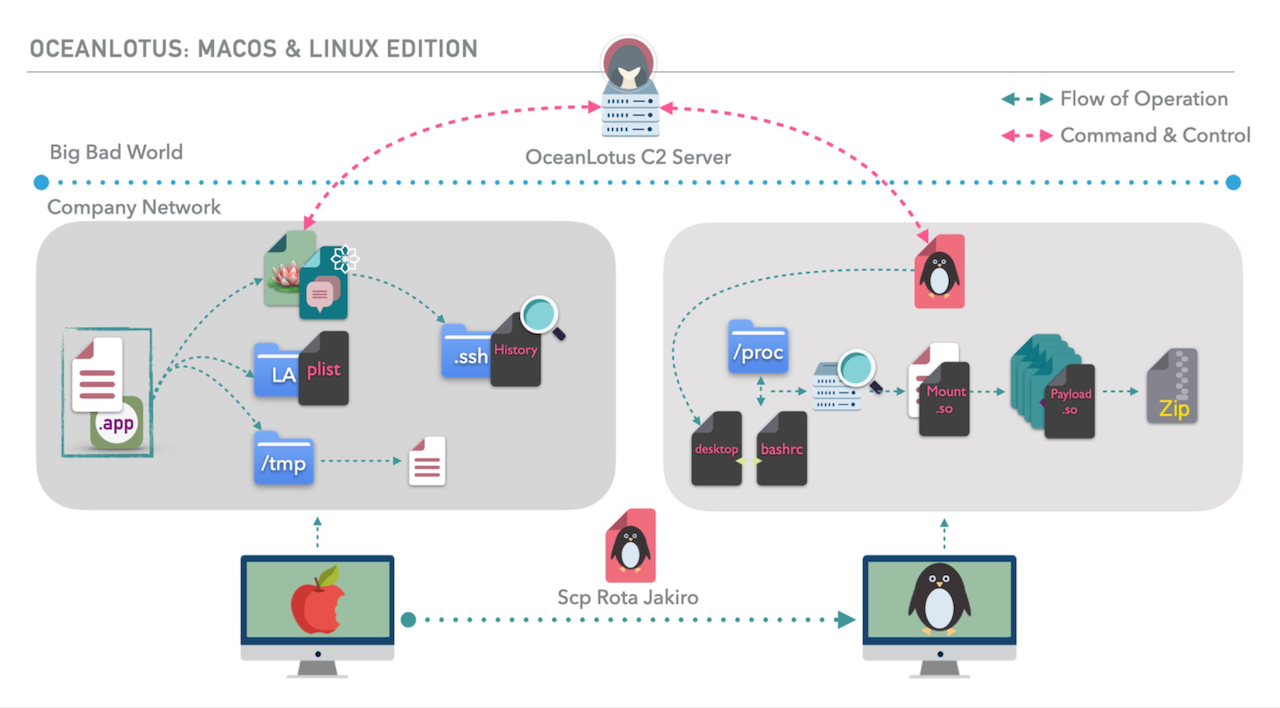
OceanLotus (aka APT32, SeaLotus, APT-C-00) is a suspected Vietnam-based threat group that has been active since at least 2014. The group has targeted multiple private sector industries as well as foreign governments, dissidents, and journalists. This project adds the first macOS and Linux focused plans to the Adversary Emulation library for red and blue teams to systematically test their defenses against real-world adversary TTPs.

Threat intel reporting shows that adversaries are increasingly targeting macOS and Linux systems, and there are no public adversary emulation plans for macOS and Linux with an explanation of defenses from the perspective of the adversary.

We have created an emulation plan for OceanLotus that starts on macOS and ends on a Linux host with explicit defensive telemetry for a full scope purple teaming perspective.

This is the first emulation plan released publicly that enables a purple team operation on macOS and Linux, providing visibility into environments inaccessible with current prior resources.





Use our latest mappings to replace assumption-driven cloud defense with evidence-based decisions to stop cloud adversaries in their tracks. With …
MITRE INFORM is a program-level assessment designed to show how threat-informed your organization is and where to improve next across cyber …
With Attack Flow, you will capture the entire attack and communicate what matters!
Sign up for our "Stay Informed" mailing list to receive announcements for project publications, upcoming events, and other news about the Center.