Cloud Security Built with ATT&CK
Threats to cloud computing span multiple security domains, objectives, and layers of technology. Defenders must protect dynamic, shared …
By Tiffany Bergeron and Daniel Bah • January 28, 2026

Threats to cloud computing span multiple security domains, objectives, and layers of technology. Defenders must protect dynamic, shared environments while adversaries actively exploit misconfigurations, weak controls, and gaps between responsibility boundaries. To keep up, security cannot just focus on how controls are documented. It has to focus on how real adversaries operate in cloud environments.
MITRE’s Center for Threat-Informed Defense (CTID) applies a threat-informed approach that aligns organizations’ security capabilities to real adversary behaviors, connecting specific security controls to adversary tradecraft. As a result, defenders prioritize investments, validate defensive coverage, and assess risk based on observed attack activity.
With CTID members Citigroup, Cloud Security Alliance, CrowdStrike, Fortinet, and JPMorgan Chase Bank N.A., we mapped cloud-native security controls and capabilities to adversary techniques and behaviors documented in MITRE ATT&CK® to design and assess cloud defenses.
We used the Cloud Security Alliance Cloud Controls Matrix (CCM) as the control framework in this effort. The CCM provides a comprehensive set of cloud security controls that address technical and operational aspects of cloud computing across shared responsibility models. By mapping the CCM to ATT&CK techniques, we demonstrate how these industry-recognized cloud controls can mitigate specific adversary behaviors.
The CCM mapping resources, including the mappings themselves, ATT&CK Navigator layers, and the mapping methodology, are all available on our Mappings Explorer website. With these mappings, users will:
We followed our established methodology to connect security capabilities to ATT&CK. This methodology reflects our experience mapping multiple security frameworks and provides a repeatable way to use ATT&CK to understand how security capabilities mitigate adversary behavior. Using this methodology, we mapped the CCM v4.1 controls to ATT&CK v17.1 techniques and sub-techniques. We identified more than 200 controls across 17 cloud security domains as providing in-scope capabilities, including Application and Interface Security (AIS), Data Security and Privacy Lifecycle Management (DSP), Infrastructure Security (I&S), and Threat and Vulnerability Management (TVM). This work resulted in more than 900 mappings connecting the CCM to ATT&CK techniques and sub-techniques those controls can help mitigate.
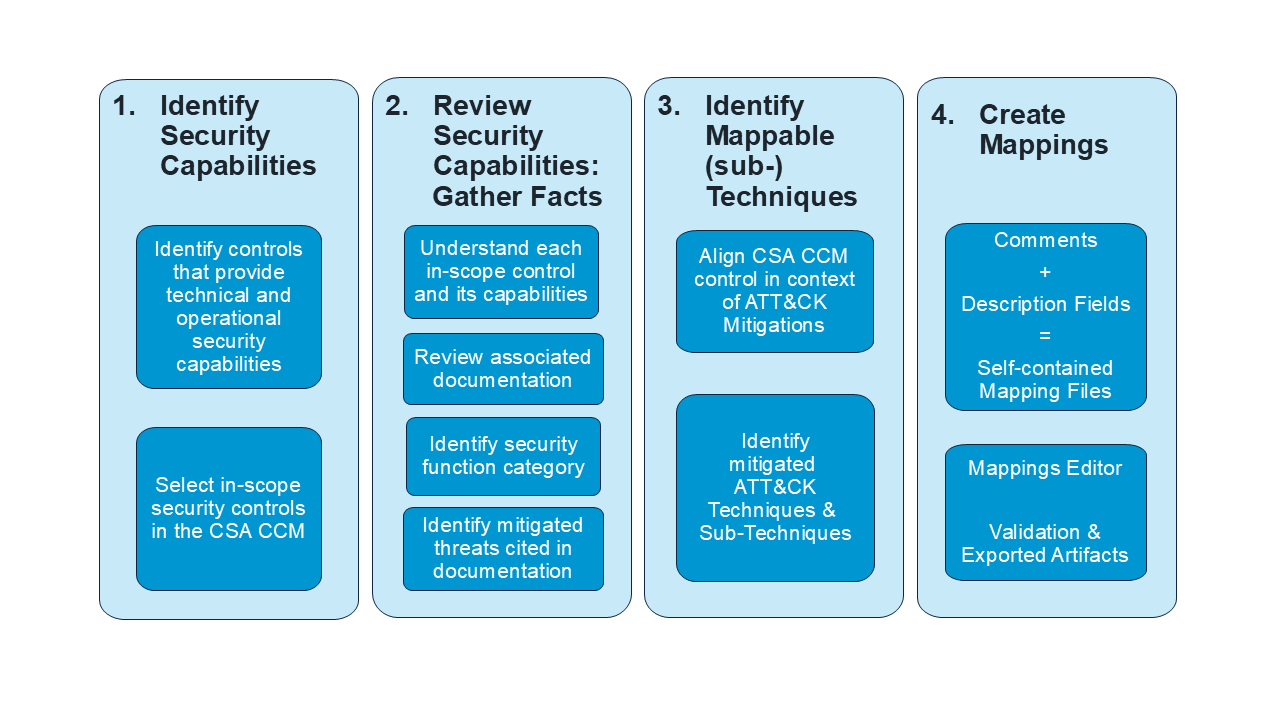
The methodology is iterative and consists of four steps, shown in the diagram below. Each step builds on the previous one, allowing analysts to understand a control’s mitigating capabilities and then map those capabilities to relevant ATT&CK techniques and sub-techniques.
We first identified security capabilities in scope. We then examined the in-scope controls in the context of ATT&CK mitigations and specific techniques and sub-techniques. From that analysis, we created mappings that connect each control to the ATT&CK techniques it helps mitigate.
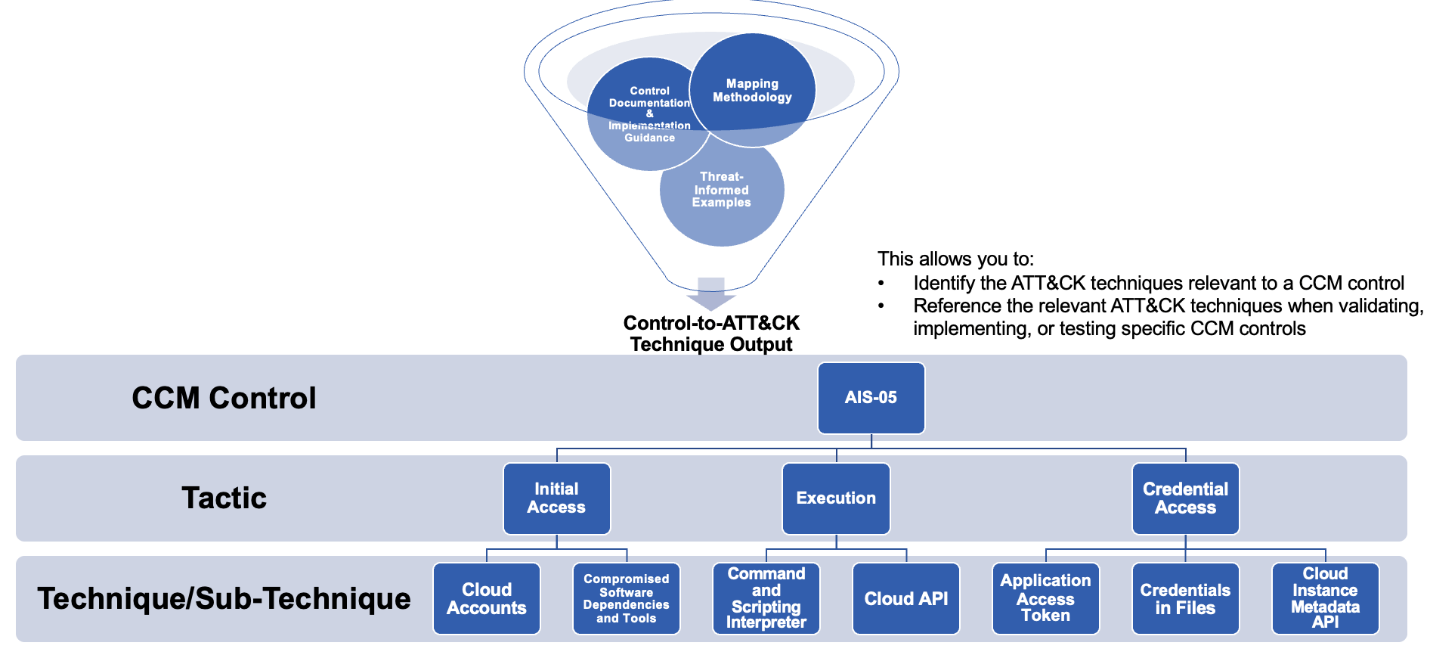
By applying CTID’s mapping methodology alongside the CCM documentation and its threat-focused implementation guidance, we mapped the CCM to specific adversary behaviors documented in ATT&CK.
As an example, the CCM control Automated Application Security Testing (AIS-05) requires both cloud service providers and customers to implement testing strategies for their applications. The AIS-05 implementation guidance explicitly describes the types of threats these testing strategies should address, including:
AIS-05 focuses on testing for different types of attacks and aligning with industry standards to improve application security. Following this guidance can mitigate up to 20 ATT&CK techniques and sub-techniques, including Supply Chain Compromise: Compromise Software Dependencies and Development Tools (T1195.001) for Initial Access and Command and Scripting Interpreter: Cloud API (T1059.009) for Execution.
These mappings align the CCM with cloud exploitation techniques and adversary operations. Use them and your organization will identify effective countermeasures and improve its cloud security posture.
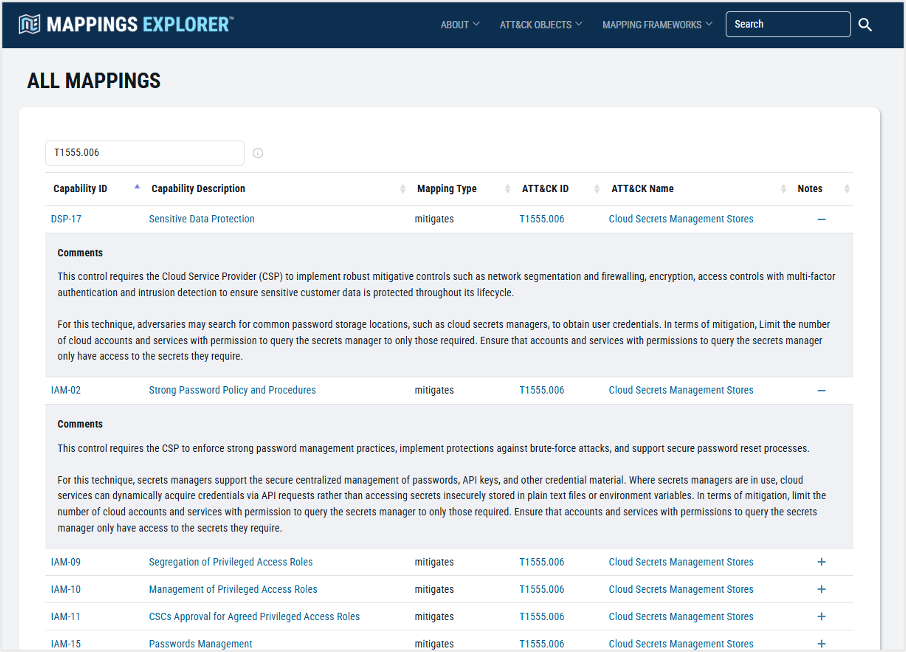
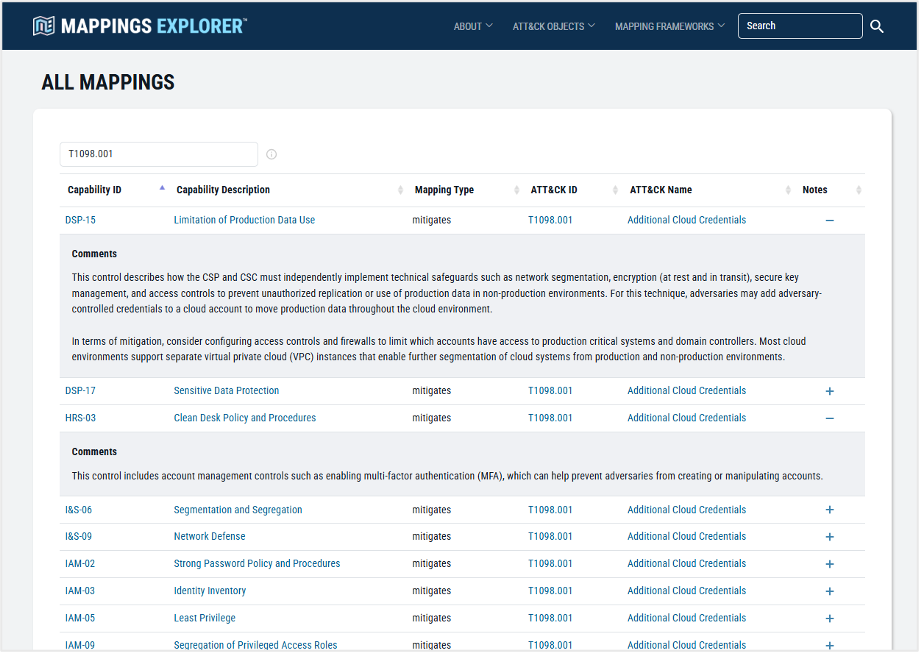
For example, Pacu is an open-source AWS exploitation framework used by both red teams and threat actors to exploit cloud misconfigurations. Pacu exercises multiple ATT&CK techniques, including Credentials from Password Stores: Cloud Secrets Management Stores (T1555.006) and Account Manipulation: Additional Cloud Credentials (T1098.001).
By using Mappings Explorer to examine the CCM to ATT&CK mappings, defenders identify controls that prevent or disrupt the capabilities used in Pacu. The mappings also provide rationale that explains how each control mitigates the associated adversary technique, as shown below.
By connecting the CCM to ATT&CK, organizations gain a common language that enables teams to work together, like the following scenarios:
This shared foundation strengthens coordination across teams and helps organizations apply threat-informed defense consistently across cloud environments.
We welcome your feedback and contributions. There are several ways that you can get involved with this and other mapping projects to help advance threat-informed defense:
You are also welcome to submit issues for any technical questions or concerns, or contact us directly for more general inquiries.
© 2026 The MITRE Corporation. Approved for Public Release. ALL RIGHTS RESERVED. Document number
26-0127.
Threats to cloud computing span multiple security domains, objectives, and layers of technology. Defenders must protect dynamic, shared …
INFORM builds on M3TID to translate threat intelligence, defensive measures, and test & evaluation into a measurable, repeatable practice. …
Threat-informed defenders can use ATT&CK Sync and the enhanced Mappings Editor to keep ATT&CK-based tools and mappings current with major …