Context to Confidence: The Next Phase of Ambiguous Techniques Research
MITRE CTID’s latest ambiguous techniques research turns context into confidence with minimum telemetry requirements and a confidence scoring …
By Gananand Kini and Tiffany Bergeron • June 16, 2025

The Cyber Risk Institute (CRI) Profile is a distillation of the NIST Cybersecurity Framework (NIST CSF) tailored to address the financial services sector’s regulatory environment. Financial institutions, financial services companies, financial firms, and their third-party providers use the CRI Profile in their threat identification and management, risk assessments, and security control programs. In collaboration with Citigroup, JPMorgan Chase Bank N.A., and FS-ISAC, and in coordination with CRI, we connected the CRI Profile to the adversarial behaviors as described in MITRE ATT&CK®.
With the CRI Profile, financial institutions can see how the combined regulatory and other supervisory provisions provide security capabilities. With these mappings to ATT&CK, analysts will extend that connection to mitigations of specific adversary behaviors.
Specifically, users of these mappings will:
Find the CRI Profile mapping resources - the mappings themselves, ATT&CK Navigator layers, and the methodology - on our Mappings Explorer website. Mappings Explorer enables defenders to access and explore the mapped security capabilities for the CRI Profile (among other frameworks) from the perspective of the ATT&CK techniques they mitigate. These mappings unite the threat-informed approach to cybersecurity and the security controls perspective.
The CRI Profile consolidates more than 2500 regulatory and other supervisory provisions into a framework of roughly 300 diagnostic statements. Each diagnostic statement (DS) is a specific, measurable objective that helps financial institutions assess and manage their cyber risks. We completed our mappings at the DS level, with consideration given for the function, category, and subcategory levels.
This project maps version 2.1 of the CRI Profile to ATT&CK v16.1 techniques and sub-techniques. We determined 60 DS to be in-scope in four functional areas of Identify, Protect, Detect, and Extend. This resulted in more than 2100 mappings to ATT&CK techniques and sub-techniques. The below figure depicts the CRI Profile coverage of all ATT&CK techniques — the darker the technique is, the more DS map to that technique.
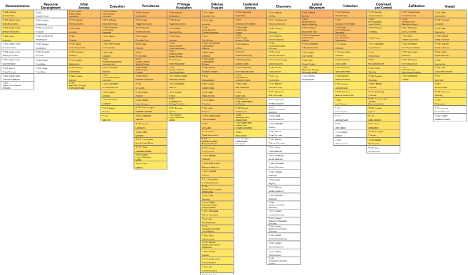
Mapping CRI Profile DS to ATT&CK applies a threat-informed approach to financial institutions cybersecurity programs and provides threat data for security control implementation decisions.
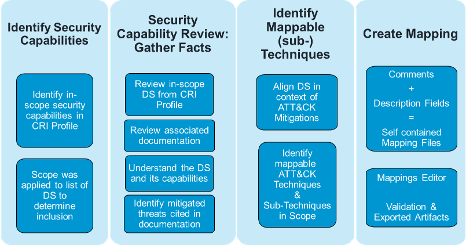
We followed our methodology for mapping framework security capabilities to ATT&CK. This methodology is based upon our experience mapping frameworks and platforms and aims to provide the community with a reusable method of using ATT&CK to determine the capabilities of security offerings.
The first step is to identify the security capabilities in scope, in this case the DS. We applied the following considerations to identify DS in scope:
Once scoped, the mapping methodology is iterative.
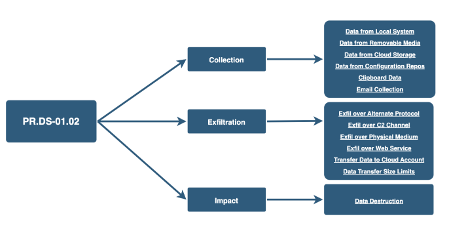
The CRI Profile under Protect: Data Security: Data loss prevention (PR.DS-01.02) provides for the implementation of technical controls to stop the loss and disclosure of sensitive information to outside attackers as well as inadvertent and malicious insiders. The implementation of data loss identification and prevention tools to monitor and protect against confidential data theft or destruction provides protection from adversary techniques related to data collection, data exfiltration, and data destruction, as depicted below.
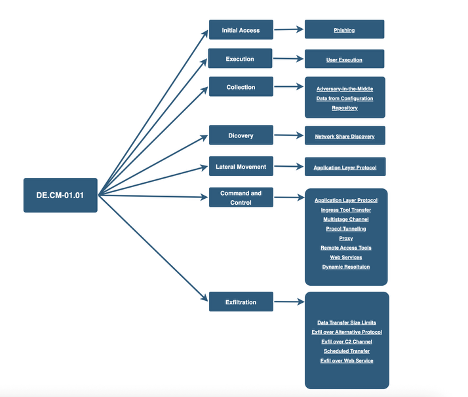
The CRI Profile statement for Detect: Continuous Monitoring: Intrusion detection and prevention (DE.CM-01.01) implements capabilities to detect and prevent potential network intrusions. Having mechanisms such as restricting unnecessary network traffic, blocking legacy protocols, and using SSL/TLS inspection can help to limit adversary movement and data exfiltration techniques, as shown below.
Tell us how you are using our work! If you have any feedback, technical questions, concerns, or contributions you’d like to make to the project, email us at ctid@mitre.org
© 2025 The MITRE Corporation. Approved for Public Release. ALL RIGHTS RESERVED. Document number
25-1854.
MITRE CTID’s latest ambiguous techniques research turns context into confidence with minimum telemetry requirements and a confidence scoring …
Threat-informed defense changes the game on the adversary. Threat-informed defenders read their adversaries’ playbooks and then orchestrate a …
MITRE ATLAS™ analyzed OpenClaw incidents that showcase how AI-first ecosystems introduce new exploit execution paths. OpenClaw is unique because …