Threat-Informed Defense for Cloud Security
Use our latest mappings to replace assumption-driven cloud defense with evidence-based decisions to stop cloud adversaries in their tracks. With …
May 10, 2022
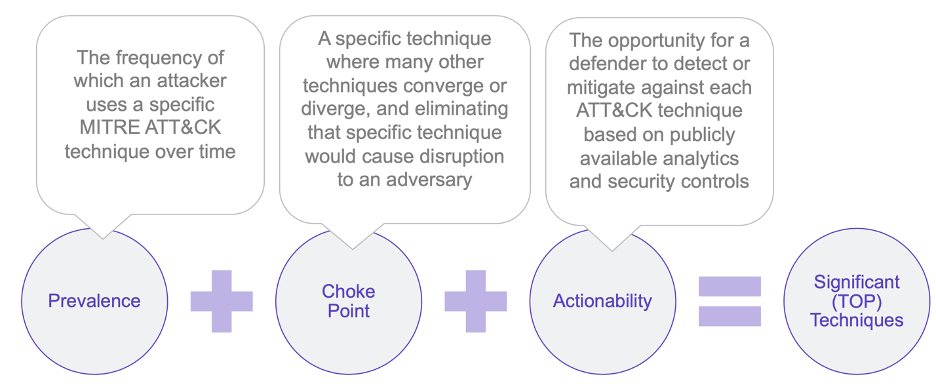
Top ATT&CK Techniques provides defenders with a systematic approach to prioritizing ATT&CK techniques. Our open methodology considers technique prevalence, common attack choke points, and actionability to enable defenders to focus on the ATT&CK techniques that are most relevant to their organization.
The Top ATT&CK Techniques Calculator makes building customized top technique lists easy. Users can create a top 10 technique list tailored to their organization.
The Top Ransomware Technique List provides a starting point for defending against ransomware attacks and demonstrates how the Top ATT&CK Techniques methodology can be tailored to different use cases.
This is an old verison of the Top ATT&CK Techniques project. For the latest version, see: Top ATT&CK Techniques

Defending against all ATT&CK techniques is simply not practical, and without guidance, determining which techniques to focus on is overwhelming.

Publish a methodology and tools to help defenders systematically prioritize ATT&CK techniques.

Defenders focus on the adversary behaviors that are most relevant to their organization and have the greatest effect on their security posture.









Use our latest mappings to replace assumption-driven cloud defense with evidence-based decisions to stop cloud adversaries in their tracks. With …
MITRE INFORM is a program-level assessment designed to show how threat-informed your organization is and where to improve next across cyber …
With Attack Flow, you will capture the entire attack and communicate what matters!
Sign up for our "Stay Informed" mailing list to receive announcements for project publications, upcoming events, and other news about the Center.