Threat-Informed Defense for Cloud Security
Use our latest mappings to replace assumption-driven cloud defense with evidence-based decisions to stop cloud adversaries in their tracks. With …
September 10, 2023
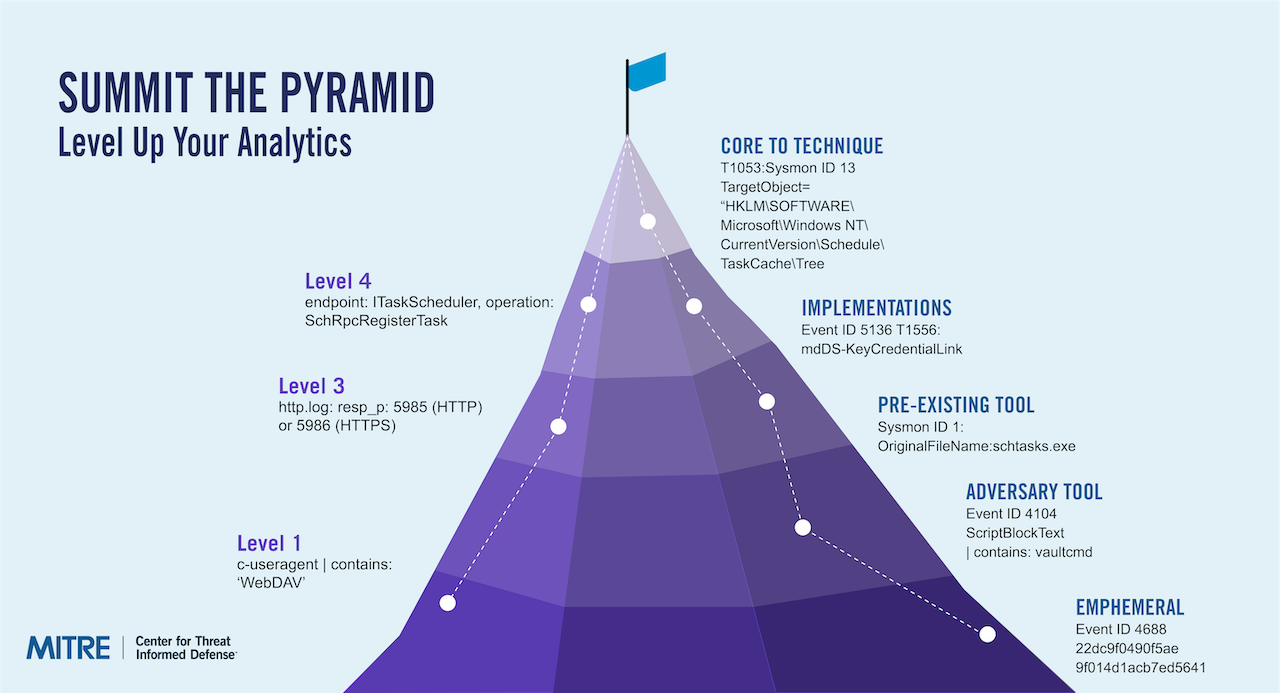
Many analytics are dependent on specific tools or artifacts. Adversaries can easily evade these with low-cost changes that exploit the dependencies. This project developed a method to evaluate analytics relative to the adversary’s cost to evade. We further created approaches and tips for defenders to make their analytics less evadable. We demonstrated the methodology with a core set of analytics.
This is an old version of the Summiting the Pyramid project. For the latest version, see: Summiting the Pyramid.

Adversaries can easily evade cyber analytics that are dependent on specific tools or artifacts.

Create and apply a methodology to evaluate the dependencies inside analytics and make them more robust by focusing on adversary behaviors.

Shift the advantage towards defenders with improved analytics that catch adversaries even as they evolve and detect future campaigns.







Use our latest mappings to replace assumption-driven cloud defense with evidence-based decisions to stop cloud adversaries in their tracks. With …
MITRE INFORM is a program-level assessment designed to show how threat-informed your organization is and where to improve next across cyber …
With Attack Flow, you will capture the entire attack and communicate what matters!
Sign up for our "Stay Informed" mailing list to receive announcements for project publications, upcoming events, and other news about the Center.