Threat-Informed Defense for Cloud Security
Use our latest mappings to replace assumption-driven cloud defense with evidence-based decisions to stop cloud adversaries in their tracks. With …
February 13, 2025
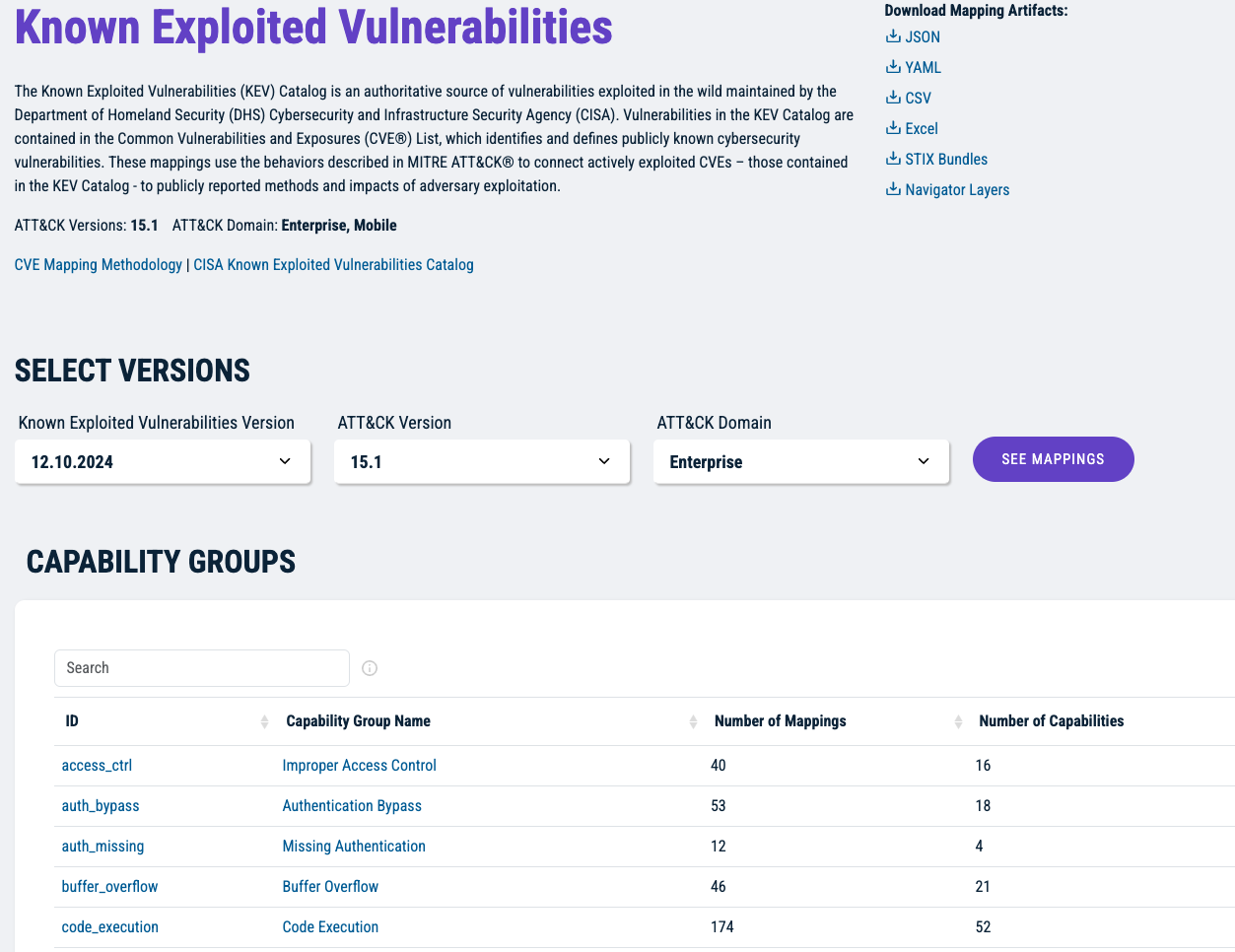
Prioritize Known Exploited Vulnerabilities shows defenders how to take a threat informed approach to vulnerability management.
The Prioritize Known Exploited Vulnerabilities mappings are part of our Mappings Explorer program. Use the Mappings Explorer website to navigate, explore, search, and download our mappings of security capabilities to MITRE ATT&CK®.

Defenders struggle to integrate vulnerability and threat information and lack a consistent view of how adversaries use vulnerabilities to achieve their goals. Without this context, it is difficult to appropriately prioritize vulnerabilities.

Use the adversary behaviors described in ATT&CK to characterize the impact of a vulnerability. Then, apply that methodology to provide critically needed context to known exploited vulnerabilities.

CVEs linked to ATT&CK techniques form a crucial contextual bridge between vulnerability management, threat modeling, and compensating controls, empowering defenders to better assess the true risk posed by specific vulnerabilities in their environment.






Use our latest mappings to replace assumption-driven cloud defense with evidence-based decisions to stop cloud adversaries in their tracks. With …
MITRE INFORM is a program-level assessment designed to show how threat-informed your organization is and where to improve next across cyber …
With Attack Flow, you will capture the entire attack and communicate what matters!
Sign up for our "Stay Informed" mailing list to receive announcements for project publications, upcoming events, and other news about the Center.