Threat-Informed Defense for Cloud Security
Use our latest mappings to replace assumption-driven cloud defense with evidence-based decisions to stop cloud adversaries in their tracks. With …
April 10, 2024
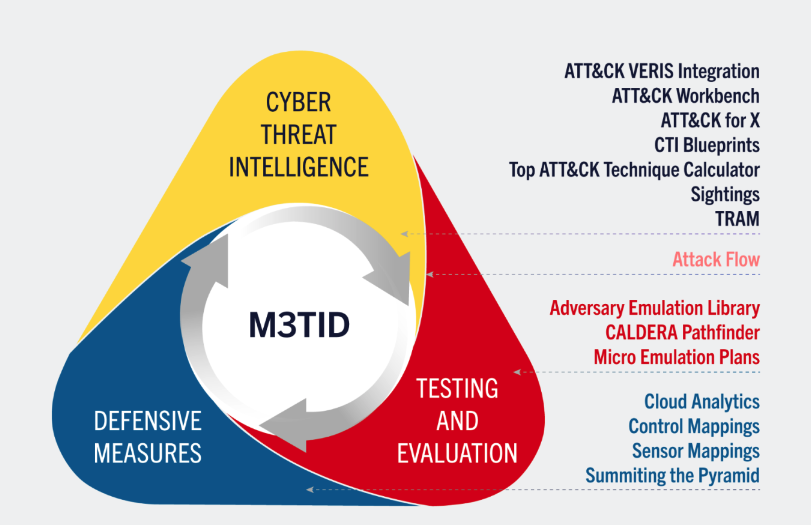
M3TID leverages threat understanding to improve a security program by creating an actionable definition of threat-informed defense and its associated key activities, and a formalized approach to measure your threat-informed defense. This maturity model complements existing cybersecurity maturity models by incorporating a measure of how well threat information is leveraged.
Leveraging knowledge of cyber threats to prioritize the allocation of limited resources is one of the most impactful and efficient ways to reduce overall risk.

Using a threat-informed defense is one of the most effective ways to defend yourself against cyber-attacks, yet there is no definitive guidance on how to create and mature a threat-informed defense.

Create a foundational resource that defines threat-informed defense, all of its components, and develop a solution to measure, maximize, and mature threat-informed defense.

Organizations can strategically enhance their cybersecurity capabilities, optimize resource allocation, and improve defenses against cyber-attacks, contributing to a stronger and more resilient infrastructure.









Use our latest mappings to replace assumption-driven cloud defense with evidence-based decisions to stop cloud adversaries in their tracks. With …
MITRE INFORM is a program-level assessment designed to show how threat-informed your organization is and where to improve next across cyber …
With Attack Flow, you will capture the entire attack and communicate what matters!
Sign up for our "Stay Informed" mailing list to receive announcements for project publications, upcoming events, and other news about the Center.