Threat-Informed Defense for Cloud Security
Use our latest mappings to replace assumption-driven cloud defense with evidence-based decisions to stop cloud adversaries in their tracks. With …
March 27, 2024
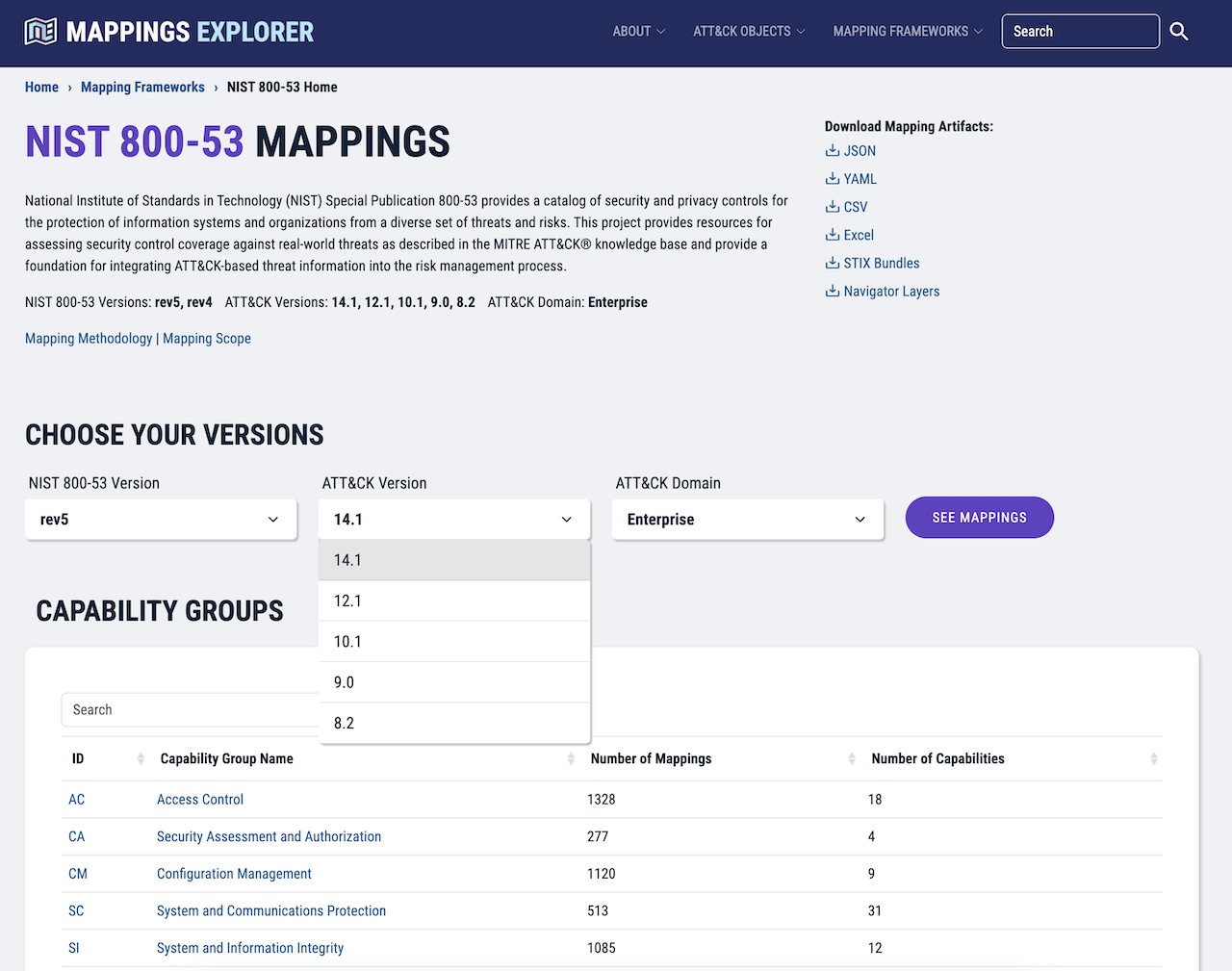
Mappings Explorer is a hub for defenders to explore security capabilities mapped to MITRE ATT&CK®. This singular resource enables cyber defenders to understand how security controls and capabilities protect against the adversary behaviors catalogued in the ATT&CK knowledge base. Our mappings bridge the threat-informed approach to cybersecurity with traditional cyber hygiene through the deployment of security controls.
Mappings Explorer presents threat and mitigation data in easily accessible and customizable ways. This centralized collection enables threat-informed decision making by relating real-world cyber threats to corresponding mapped security capabilities.
Visit the Center’s Mappings Explorer website to navigate, explore, search, and download our mappings of security capabilities to MITRE ATT&CK®.

Defenders lack a single resource to view defensive capabilities mapped to the adversarial attack techniques in ATT&CK.

Create a central hub that provides access to all mappings, and offer standard tools and processes for developing mappings to ATT&CK.

Defenders can easily access and explore mapped security controls from the perspective of the ATT&CK techniques they mitigate.





Use our latest mappings to replace assumption-driven cloud defense with evidence-based decisions to stop cloud adversaries in their tracks. With …
MITRE INFORM is a program-level assessment designed to show how threat-informed your organization is and where to improve next across cyber …
With Attack Flow, you will capture the entire attack and communicate what matters!
Sign up for our "Stay Informed" mailing list to receive announcements for project publications, upcoming events, and other news about the Center.