Threat-Informed Defense for Cloud Security
Use our latest mappings to replace assumption-driven cloud defense with evidence-based decisions to stop cloud adversaries in their tracks. With …
June 21, 2024
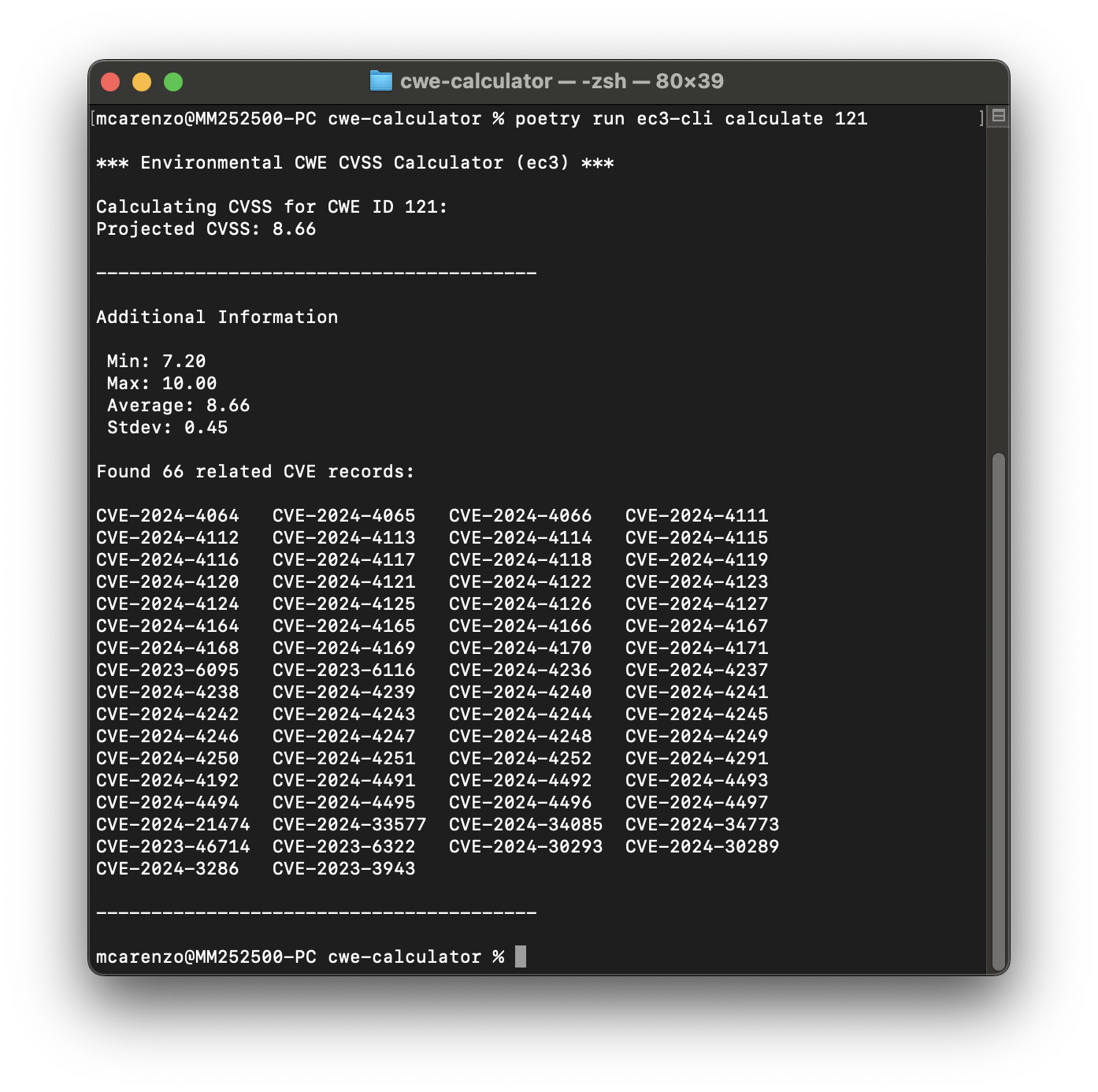
The software industry is faced with managing large numbers of software weaknesses (commonly identified by static-scanning tools using CWE ID reference), alongside large numbers of software vulnerabilities (CVEs), which all sit across many assets with differing security requirements. The calculator enables software development teams to score and prioritize discovered weaknesses empirically based on data in the National Vulnerability Database (NVD).

Without a common system of comparison across software weaknesses (CWEs) and software vulnerabilities (CVEs) that factors in environmental context, engineering teams cannot effectively prioritize their work, and thus waste cycles on wrong things while they miss opportunities to secure systems.

The CWE with Environmental CVSS Calculator will provide output that effectively enables a CWE in a specified environment to be priority ranked against a CVE in the same or different environment.

Software development teams will focus their limited resources on addressing the most dangerous issues.




Use our latest mappings to replace assumption-driven cloud defense with evidence-based decisions to stop cloud adversaries in their tracks. With …
MITRE INFORM is a program-level assessment designed to show how threat-informed your organization is and where to improve next across cyber …
With Attack Flow, you will capture the entire attack and communicate what matters!
Sign up for our "Stay Informed" mailing list to receive announcements for project publications, upcoming events, and other news about the Center.