Threat-Informed Defense for Cloud Security
Use our latest mappings to replace assumption-driven cloud defense with evidence-based decisions to stop cloud adversaries in their tracks. With …
June 7, 2023
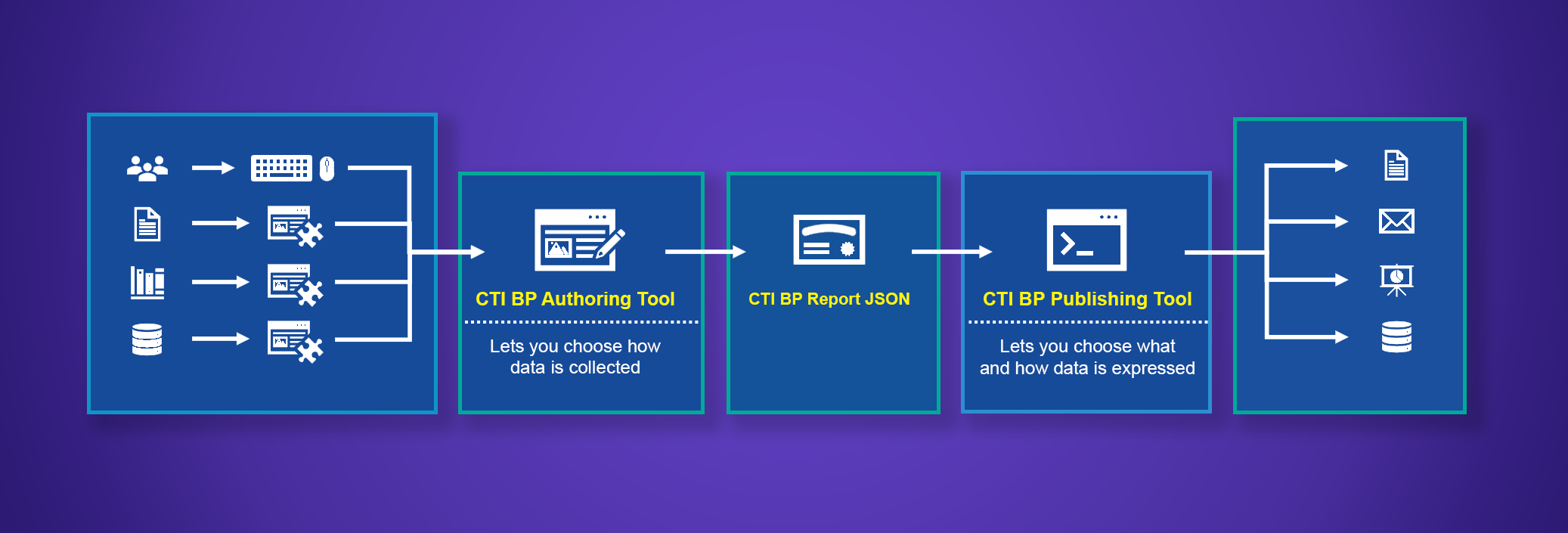
This project developed an approach and prototype tool for creating narrative cyber threat intel reports that analysts need in the form they need them. Reports produced using CTI Blueprints include structured STIX content, are tagged with ATT&CK reference, and enable operational defensive cyber analysis, analytics testing, and adversary emulation. We will establish a new normal for cyber threat intelligence. Producers will create actionable intelligence for their consumers, and consumers will take specific threat-informed action.

Threat intel producers need clear and concrete guidance and tools to create finished intelligence that meet defenders’ needs.

Answer defenders’ critical questions through actionable intelligence reports created from expert-developed templates that reflect defenders’ use cases.

Threat intelligence producers create actionable intelligence that their users can operationalize immediately.









Use our latest mappings to replace assumption-driven cloud defense with evidence-based decisions to stop cloud adversaries in their tracks. With …
MITRE INFORM is a program-level assessment designed to show how threat-informed your organization is and where to improve next across cyber …
With Attack Flow, you will capture the entire attack and communicate what matters!
Sign up for our "Stay Informed" mailing list to receive announcements for project publications, upcoming events, and other news about the Center.