Threat-Informed Defense for Cloud Security
Use our latest mappings to replace assumption-driven cloud defense with evidence-based decisions to stop cloud adversaries in their tracks. With …
October 13, 2020
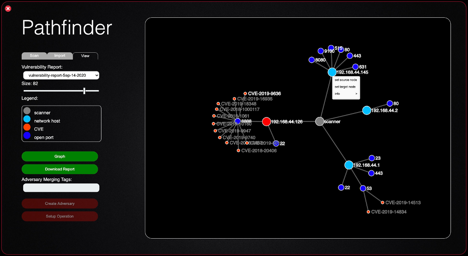
This open-source CALDERA plugin helps you understand what a vulnerability exposes to an adversary and what potential destructive paths an adversary could take within the network as a result of those vulnerabilities. Pathfinder aims to push the boundaries on vulnerability scanning, moving them to the next generation by integrating vulnerability scan data with the CALDERA automated adversary emulation platform. Pathfinder first conducts a scan of a target network, and the results of the scan are ingested into CALDERA’s knowledge store, where it can then map out the network. Pathfinder is then able to combine the information from the scan with the power of a breach and attack simulation tool in order to map out potential attack paths within the target network.

Traditional vulnerability scanning often lacks the perspective of the adversary and doesn’t effectively convey the true impact of a given vulnerability in your organization.

Push the boundaries on vulnerability scanning, moving them to the next generation by integrating vulnerability scan data with the CALDERA automated adversary emulation platform.

Show defenders what a vulnerability exposes to an adversary and what potential destructive paths an adversary could take within the network as a result of those vulnerabilities.


Use our latest mappings to replace assumption-driven cloud defense with evidence-based decisions to stop cloud adversaries in their tracks. With …
MITRE INFORM is a program-level assessment designed to show how threat-informed your organization is and where to improve next across cyber …
With Attack Flow, you will capture the entire attack and communicate what matters!
Sign up for our "Stay Informed" mailing list to receive announcements for project publications, upcoming events, and other news about the Center.