Threat-Informed Defense for Cloud Security
Use our latest mappings to replace assumption-driven cloud defense with evidence-based decisions to stop cloud adversaries in their tracks. With …
May 3, 2021
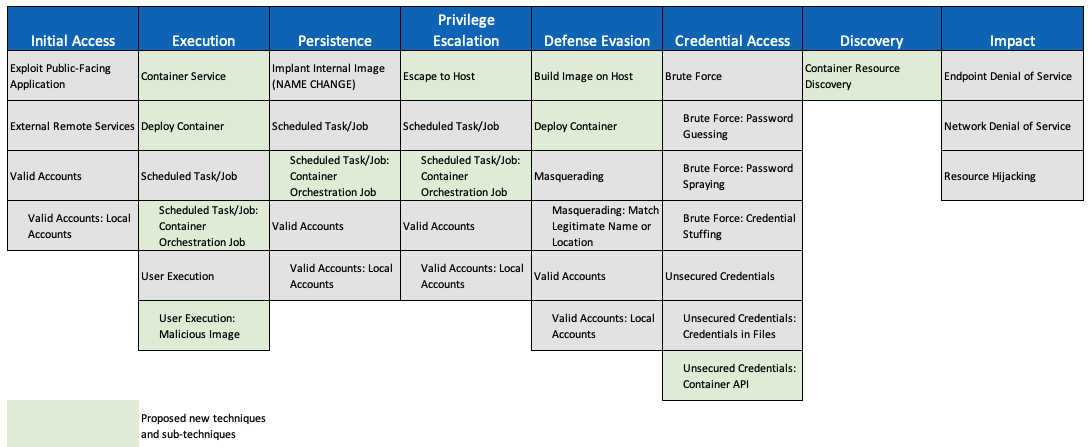
This project investigated the viability of adding container-related techniques into MITRE ATT&CK, leading to the development of an ATT&CK for Containers matrix. This work covers both orchestration-level (e.g., Kubernetes) and container-level (e.g., Docker) adversary behaviors in a single Containers platform which has been incorporated in version 9 of ATT&CK. The project team worked with contributors from around the world to identify and refine both existing ATT&CK techniques as well as completely new container-specific ones.

Defenders lack visibility into adversary behaviors in and against container technologies leaving their organizations exposed to emerging threats.

Expand MITRE ATT&CK to describe adversary behaviors in and against container technologies including Docker and Kubernetes.

Brings focus to adversary behaviors in an emergent domain leveraging the well-understood and widely adopted ATT&CK methodology.




Use our latest mappings to replace assumption-driven cloud defense with evidence-based decisions to stop cloud adversaries in their tracks. With …
MITRE INFORM is a program-level assessment designed to show how threat-informed your organization is and where to improve next across cyber …
With Attack Flow, you will capture the entire attack and communicate what matters!
Sign up for our "Stay Informed" mailing list to receive announcements for project publications, upcoming events, and other news about the Center.