Threat-Informed Defense for Cloud Security
Use our latest mappings to replace assumption-driven cloud defense with evidence-based decisions to stop cloud adversaries in their tracks. With …
June 22, 2022
ATT&CK Powered Suit is a freely available browser extension that puts the MITRE ATT&CK® knowledge base at your fingertips. This extension enables quick searches for tactics, techniques, and more without disrupting your workflow. Easily copy snippets into a notebook to streamline your research. Export selected techniques to ATT&CK navigator. The extension supports context menus, omnibar, and more.
This project would not have been possible without our valued partnership with Fujitsu. We are especially grateful to Mr. Toshitaka Satomi for proposing the original concept and for his hard work providing the initial source code.

The MITRE ATT&CK® community spends too much time copying and pasting text from one place to another to achieve simple tasks like looking up ATT&CK technique ids, linking to a software page, or just finding a term from the latest threat intel report in the ATT&CK knowledge base.

Created with cyber threat intel analysts and defenders in mind, Powered Suit creates an overlay in your browser where you can quickly look up ATT&CK objects.

Execute quick searches for tactics, techniques, and more without disrupting your workflow and export those results into your research or ATT&CK Navigator.
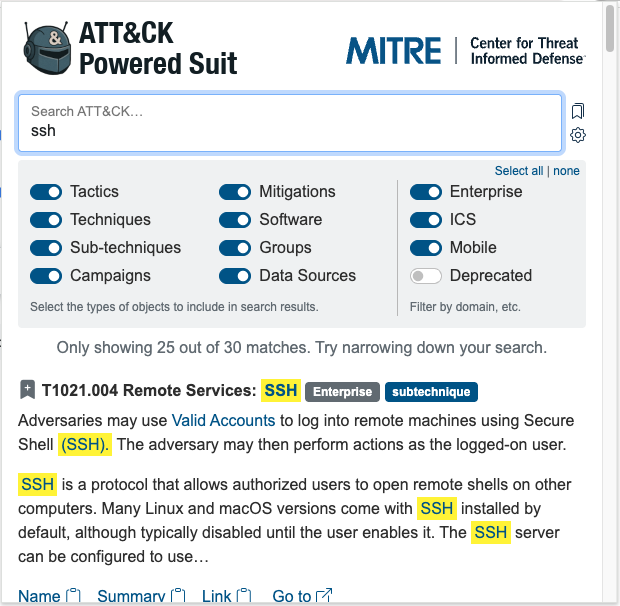

The MITRE ATT&CK community spends too much time copying and pasting text from one place to another to achieve simple tasks like looking up ATT&CK technique IDs, linking to a software page, or just finding a term from the latest threat intel report in the ATT&CK knowledge base. Now, with ATT&CK Powered Suit, you can quickly look up ATT&CK objects. This extension creates an overlay in your browser that lets you copy information with a single click to paste into your research notebook. The demo video below provides a short summary of the key features and use cases.
Use our latest mappings to replace assumption-driven cloud defense with evidence-based decisions to stop cloud adversaries in their tracks. With …
MITRE INFORM is a program-level assessment designed to show how threat-informed your organization is and where to improve next across cyber …
With Attack Flow, you will capture the entire attack and communicate what matters!
Sign up for our "Stay Informed" mailing list to receive announcements for project publications, upcoming events, and other news about the Center.