Threat-Informed Defense for Cloud Security
Use our latest mappings to replace assumption-driven cloud defense with evidence-based decisions to stop cloud adversaries in their tracks. With …
May 13, 2025
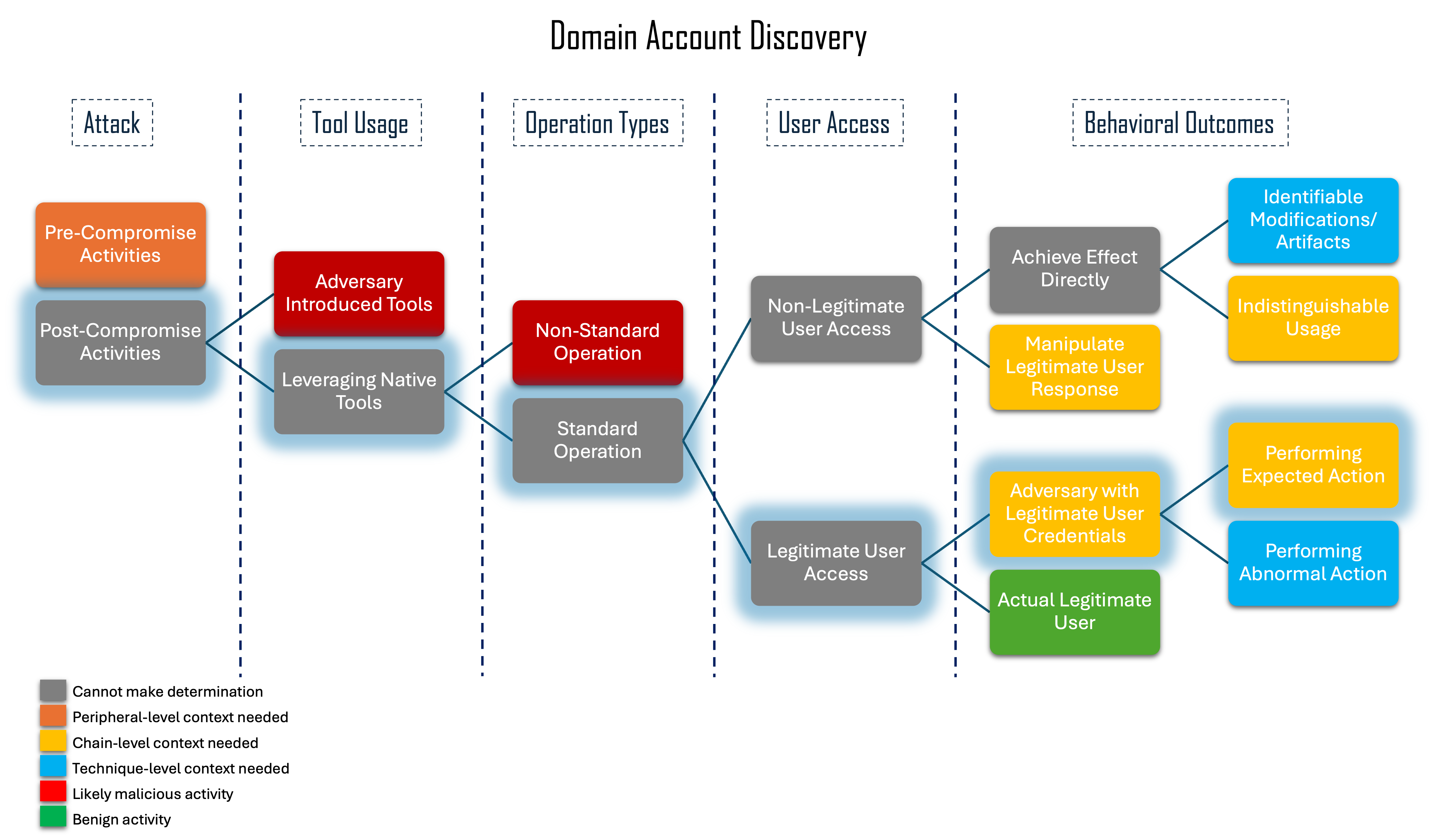
Building upon the research of Summiting the Pyramid, Ambiguous Techniques is a methodology to determine malicious intent behind seemingly benign behavior by applying contextual analysis to ATT&CK techniques. Reduce false positives and uncover adversarial use of living-off-the-land activity.

Many ATT&CK techniques, especially those used in living-off-the-land activity, produce observables that are indistinguishable from benign behavior, making it difficult for defenders to determine malicious intent and resulting in unreliable or overly noisy detections.

Create a methodology that uses the surrounding context of a detection event to infer the intent of the actor, thus removing the ambiguity.

Reduce false positives and improve detection accuracy so defenders can prioritize the alerts that truly matter.








Use our latest mappings to replace assumption-driven cloud defense with evidence-based decisions to stop cloud adversaries in their tracks. With …
MITRE INFORM is a program-level assessment designed to show how threat-informed your organization is and where to improve next across cyber …
With Attack Flow, you will capture the entire attack and communicate what matters!
Sign up for our "Stay Informed" mailing list to receive announcements for project publications, upcoming events, and other news about the Center.